Below you can find a step by step tutorial on how to integrate Microsoft Azure Active Directory with MetaDefender Managed File Transfer using the OpenID Connect protocol.
Prerequisites: An Entra Tenant (quick guide: https://learn.microsoft.com/en-us/entra/identity-platform/quickstart-create-new-tenant )
Microsoft Azure with Active Directory name changed to Microsoft Entra ID
Credentials and other sensitive information are blurred in the below examples for security purposes
Register application in Microsoft Entra ID
- Sign into Microsoft Entra ID and navigate to admin dashboard
- Go to App registrations and select New registration

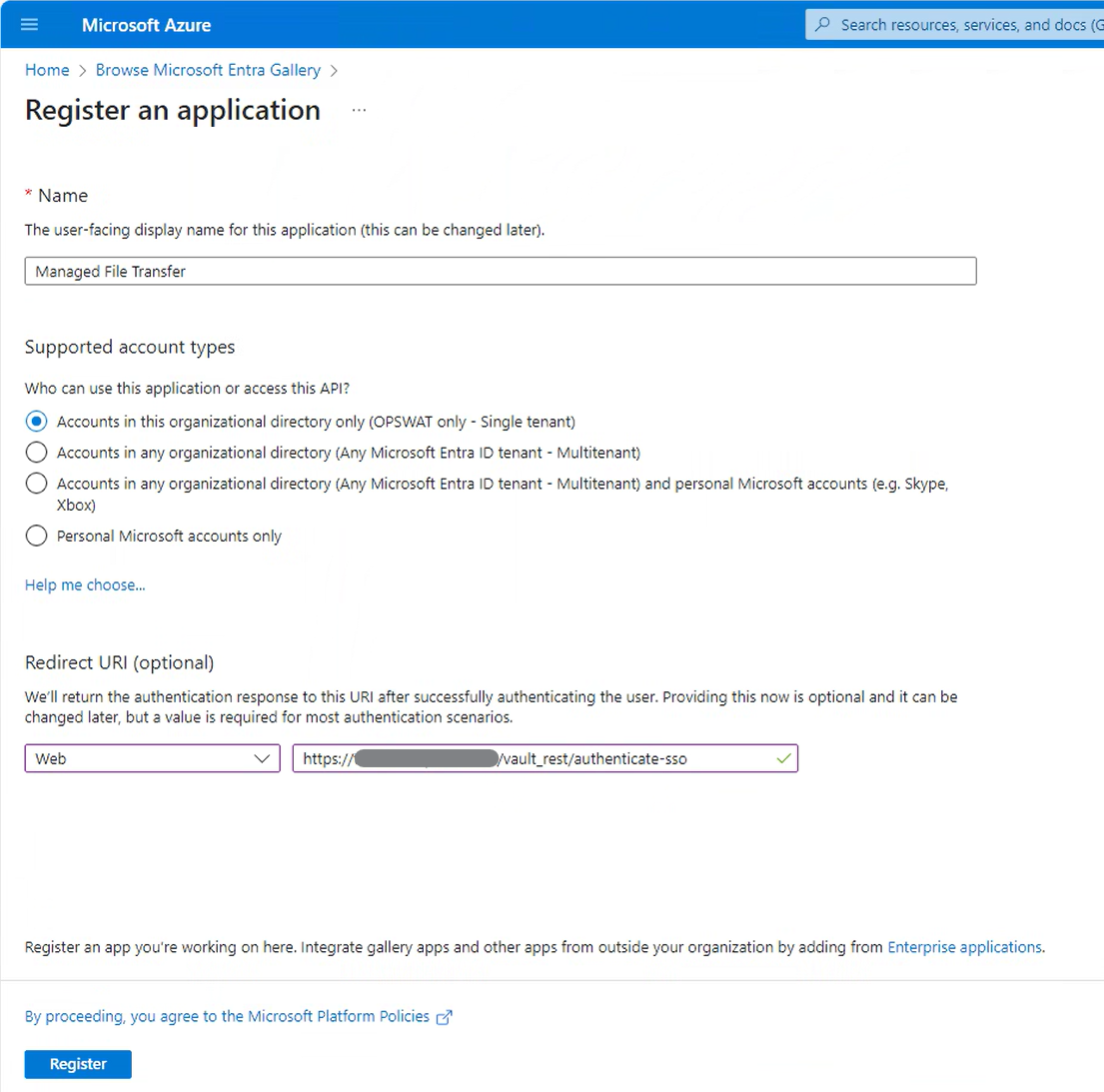
- Let’s configure the application settings.
- Give the application a name. for example “OPSWAT Managed File Transfer”.
- Configure the Redirect URL (
https://host:port/vault_rest/authenticate-sso) - this can also be found in MetaDefender Managed File Transfer → Settings → Authentication → Single Sign-On after you fill in IP Address Or Domain
Microsoft Entra ID supports only HTTPS protocol for redirect URI
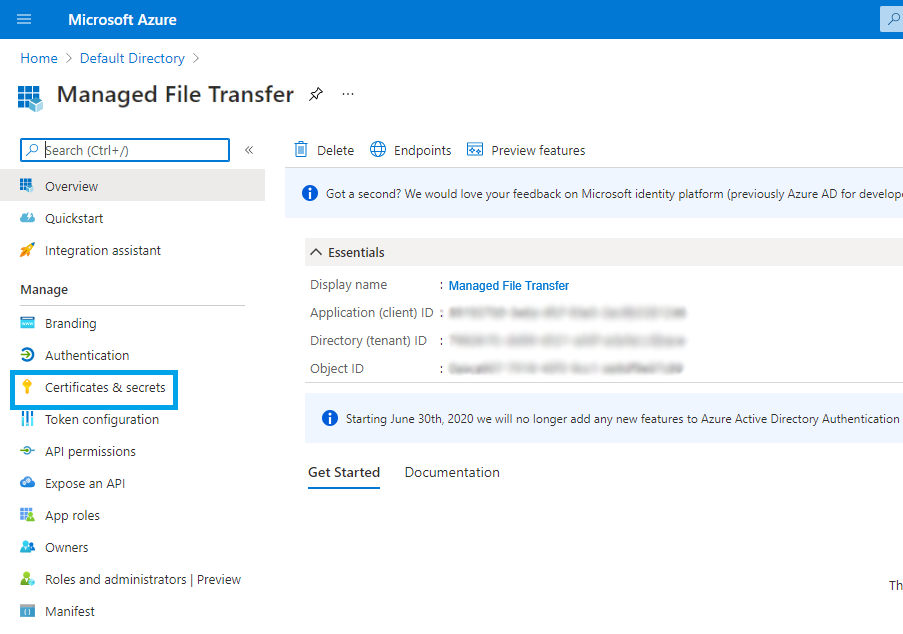
- Record Application (client) ID and Directory (tenant) ID
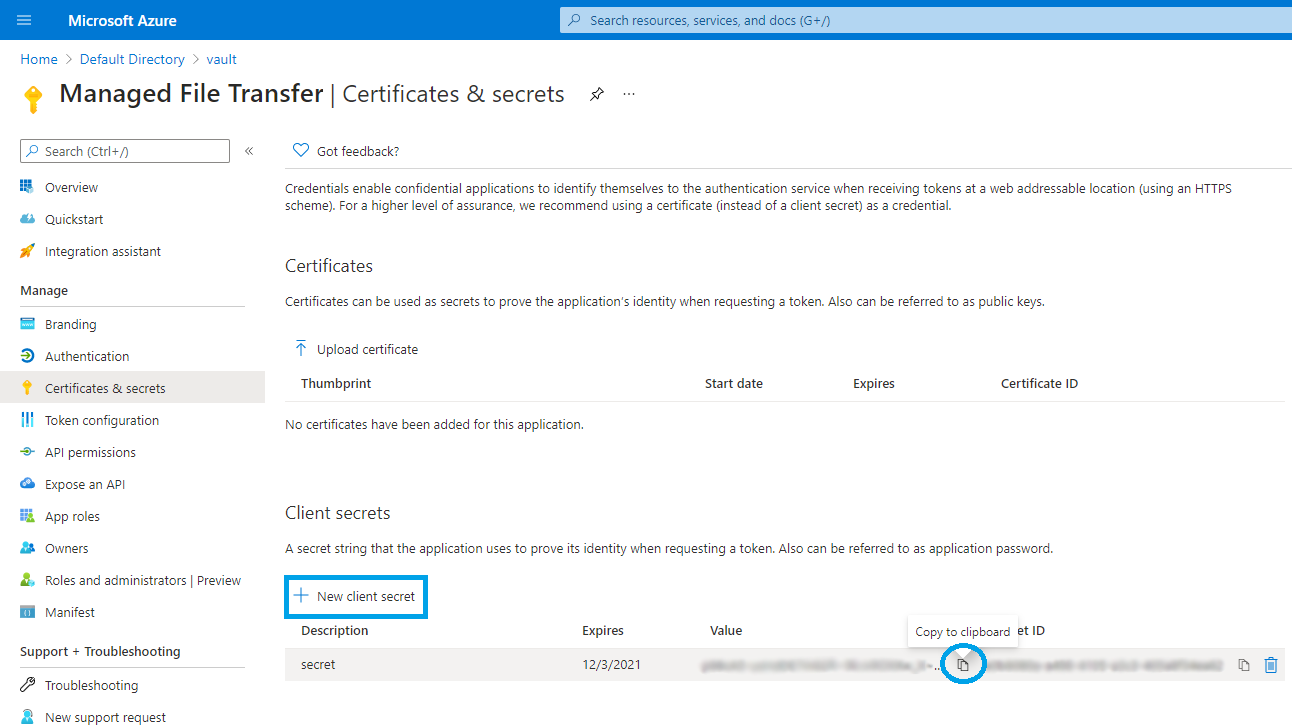
Generate Secret key for Entra ID SSO
Go to Certificates & Secrets and generate a new client secret string (also referred to as an application password). Record the client secret.
You will not be able to retrieve client secret at a later time because it will be hidden. You need to generate a new secret in this case.
Configure Managed File Transfer for Entra ID SSO
Let’s configure MetaDefender Managed File Transfer SSO settings using the information collected above
Go to MetaDefender Managed File Transfer web console and navigate to Settings → Authentication → Single Sign-On
Turn on Enable Single Sign-On
Disable Ignore Certificate Issues as Entra ID will provide a trusted certificate
Turn on Load User Profile such that MetaDefender Managed File Transfer can acquire the following claims:
- name
- preferred_username
- given_name
- family_name
Authority should point to your Microsoft Azure AD URL. You can find this URL in the Azure AD dashboard under your application endpoints. The format is:
https://login.microsoftonline.com/{directory (tenant) ID}/v2.0IP Address or Domain should point to the location of your Managed File Transfer instance. Once you fill this information, Managed File Transfer will automatically generate the Redirect URI
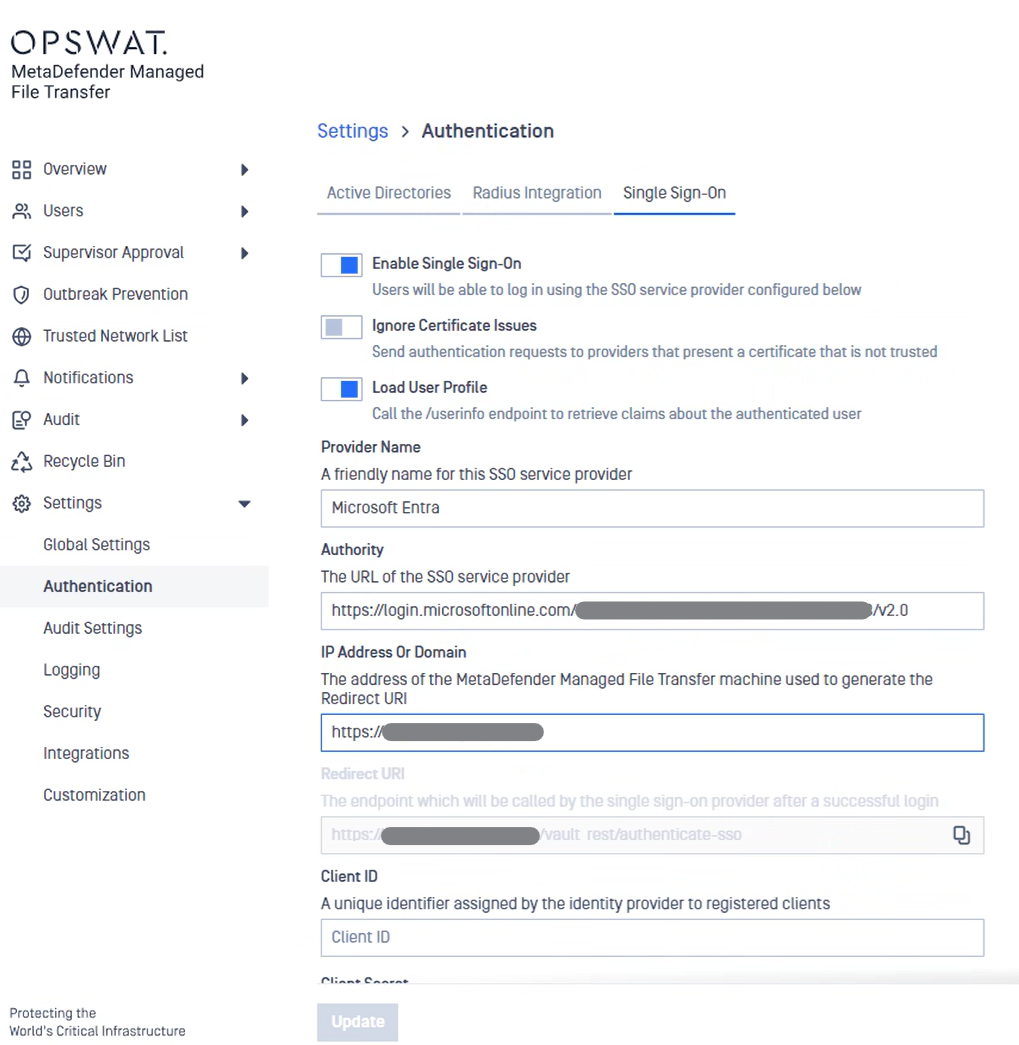
- Redirect URI should be used in Azure AD Application Settings (step 3) - This field auto generated!
- Copy Entra ID Application (client) ID (step 4) into Client ID field.
- Copy Entra ID Client secret -> Value (step 5) into Client Secret field.
- Administrator Emails: if some of the Microsoft Entra ID users should have administrative rights in Managed File Transfer, please enter a list of emails in this field. MetaDefender Managed File Transfer will compare the email of users that login from Microsoft Entra ID against the provided list to determine if a user should be an administrator.
- You don’t need to specify additional integration scopes.
- Microsoft Entra ID requires to add 2 additional endpoints:
https://login.microsoftonline.com/{Directory (tenant) ID}/https://graph.microsoft.com/oidc/userinfo
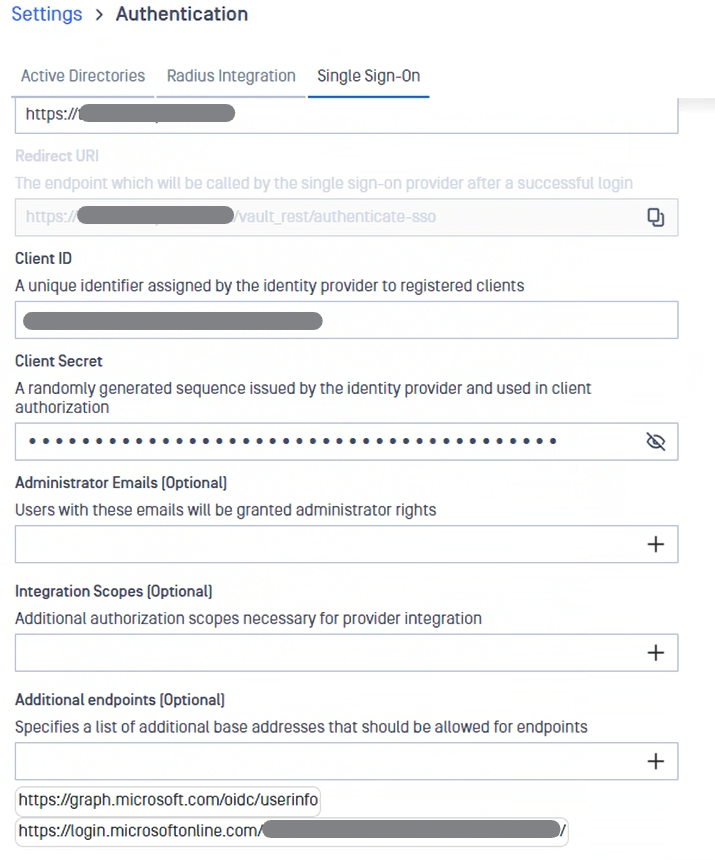
- Review final configuration
- If everything is ready, click Update.
Login as an Entra organization admin
Depending on Entra ID configuration, and organization admin should approve/allow a new application beforehand.
Log on Managed File Transfer SSO with the Entra ID administrative account and accept the newly created application:
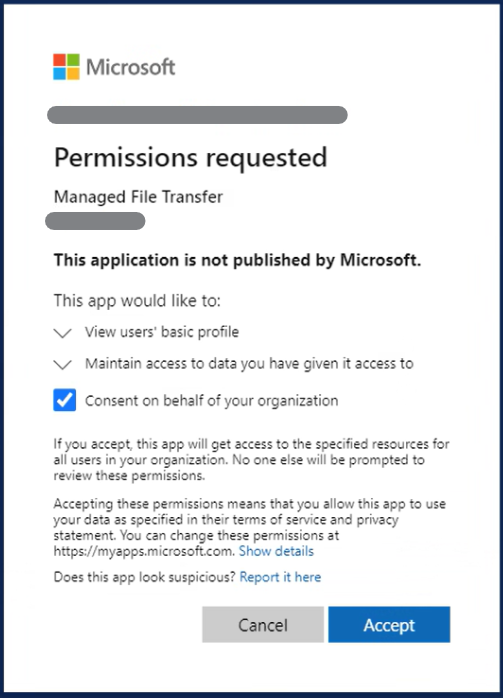
Testing the integration
- Log out of MetaDefender Managed File Transfer
- You will notice that there is a new Sign In with SSO button on the login page
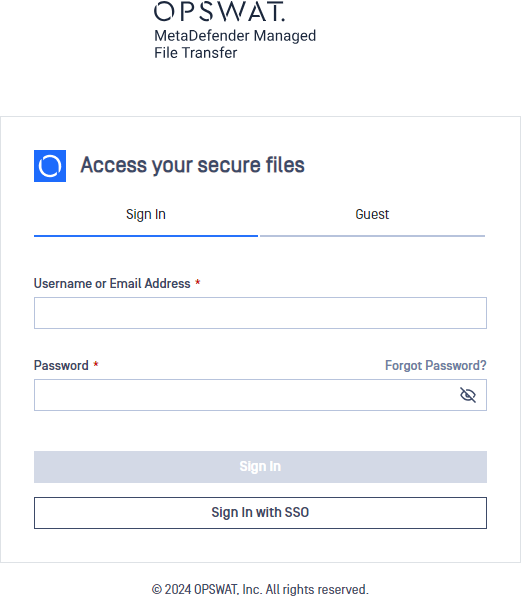
- Click Sign In with SSO. You should be redirected to Microsoft Entra ID to login. Once logged in, you will be redirected back to MetaDefender Managed File Transfer and automatically logged in.</li>

