| Version | 5.13.2 |
|---|---|
| Release date | 21 January 2025 |
| Scope | This minor version includes stability fixes and enhancements on top of version 5.13.1 which mainly focused on enhancements, bug fixes and newly introduced technology "InSights Threat Intelligence". |
Making sure to check out the Known Limitations
OPSWAT has discontinued support for CentOS 7 and RHEL 7 since December 2024 in MetaDefender Core and its associated engines.
If you need some more time to transition from legacy OS, refer to this instruction Lock Your Engine and Plan for Migration.
New Features, Improvements and Enhancements
| Details | |
|---|---|
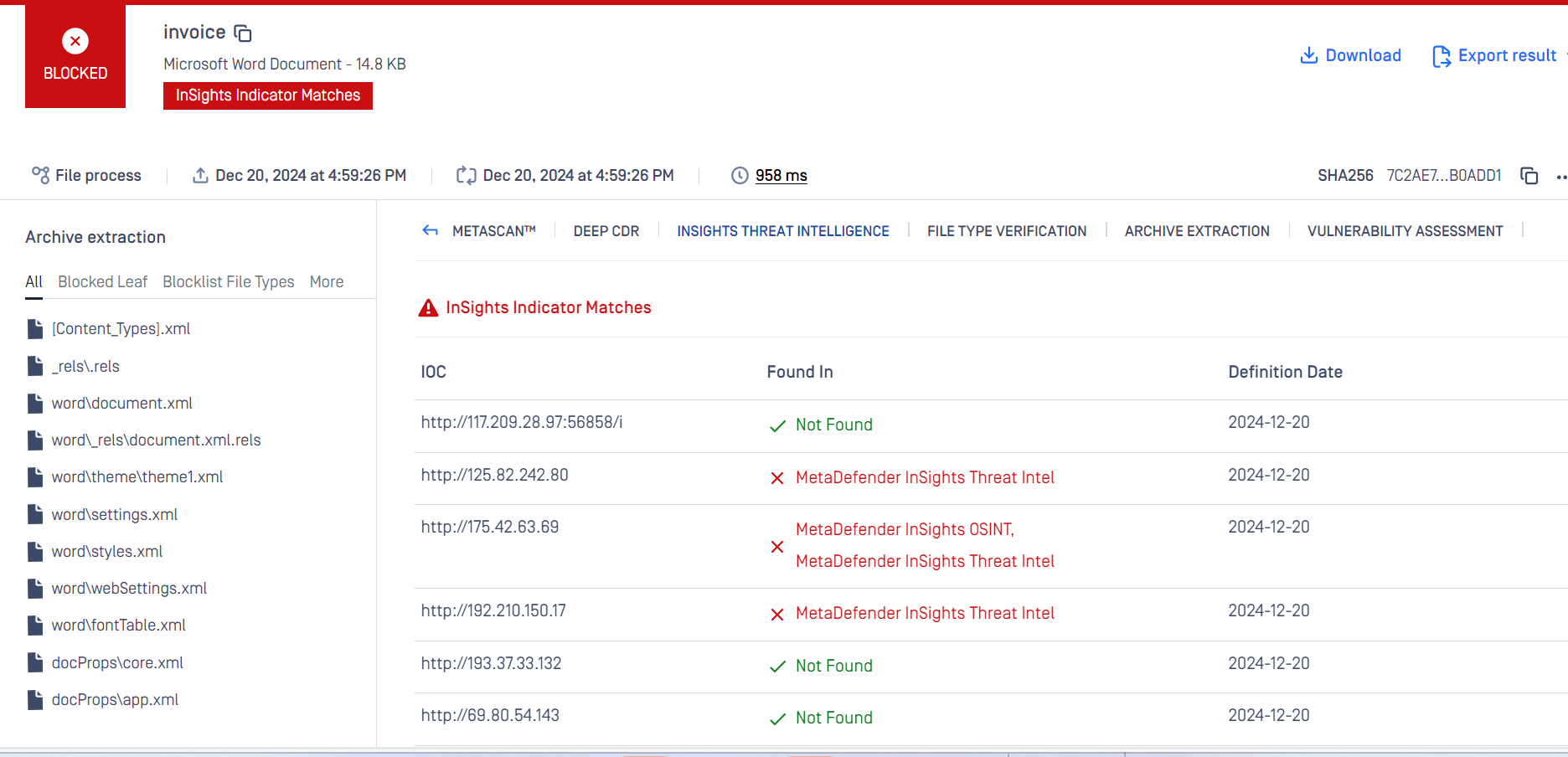
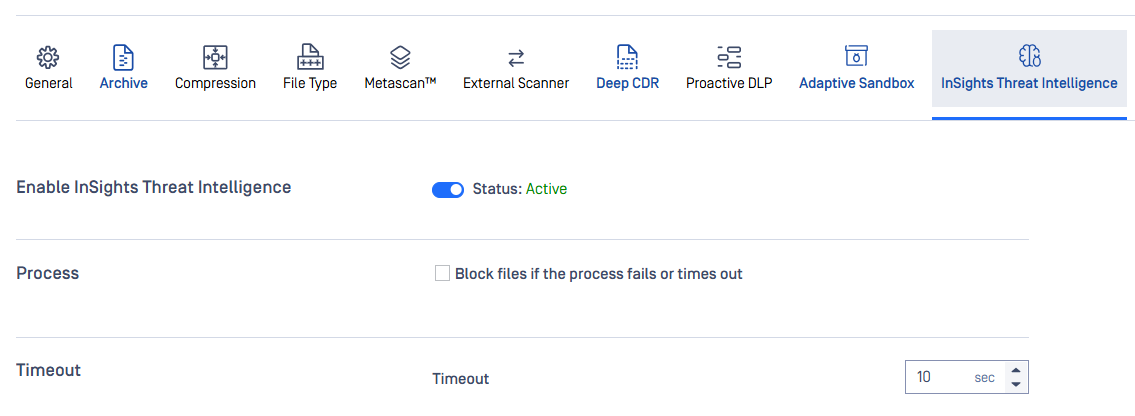
| New technology: MetaDefender InSights Threat Intelligence | This technology can detect known malicious IP addresses and domains inside document files.
To enable the technology, you need to contact OPSWAT to update your license. Then you can just go to Workflow Rule, turn the switch on and explore its capability.
For more details, please refer to InSights Threat Intelligence. |
| New OS support: Debian 12 | Since v5.13.1, we also replace base image Debian 11 with Debian 12 minimal base image. |
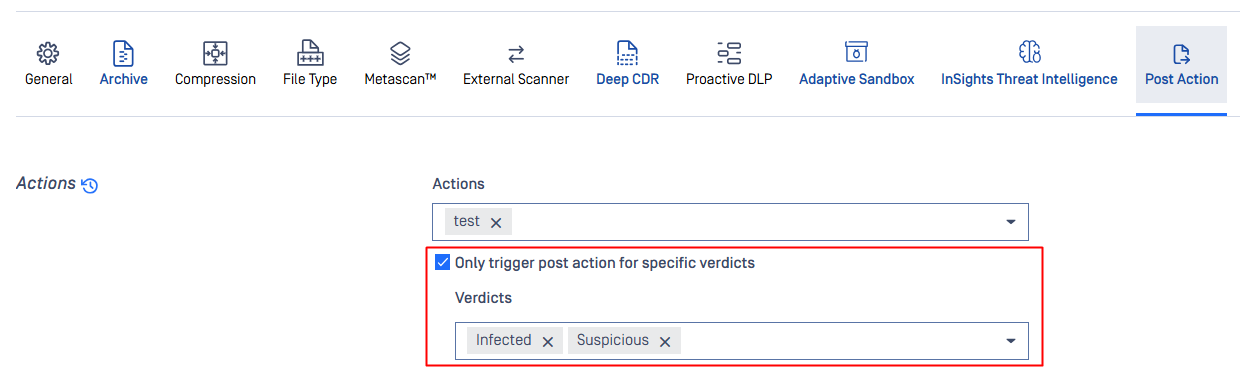
| Introduce triggering condition for Post Action | To focus needed requests and save up resources, it is necessary to introduce a triggering condition for Post Action where Administrators can select and filter what verdicts to trigger the actions only.
|
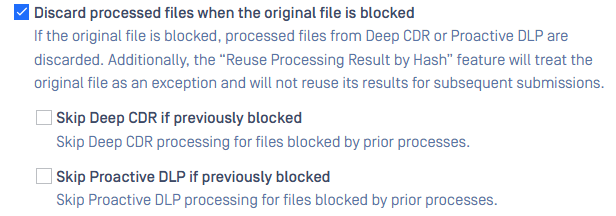
| Prohibited from downloading produced files when original file is flagged as Blocked | Introduced a setting to add an extra layer of security that makes files produced by Deep CDR or Proactive DLP unavailable for download when original file's result is flagged as Blocked for any reasons. This setting is off by default and can be found under tab General in workflow rule.
|
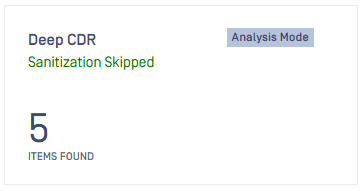
| Deep CDR analysis mode | When analysis mode is turned on in workflow rule, Deep CDR no longer sanitize file, remove object and generate a new file. Instead, the technology will report objects inside the file for analysis purpose. Under this mode, you can see a tag flagging the mode on, number of detected objects and a neutral green message.
|
| Usability enhancements / changes | Precisely calculate "hash time" of nested files to have more relevant "Child files hashing" time. Users now can granularly customize time period in Data Retention settings. Moderate UI changes to display hash values in full text as well as make other metadata result shown more clearly. Enabled verdict searching in Advanced filter of Processing History. New option to block files whose size is larger than file size threshold of Adaptive Sandbox. Users now can download list of IoCs detected by Adaptive Sandbox from the web console. In Linux non-persistent mode and local scan method, webhook callback is enhanced to ensure responses eventually to be sent even if there is permission issue or else with scanned local files. |
| Security enhancements | Upgrade OpenSSL to v3.4.0 for vulnerability fix. Upgrade protobuf to v3.21.12 for vulnerability fixes. |
| Docker enhancements | Modify Docker setup for Rocky Linux to ensure proper dependency checking for Proactive DLP. |
| UI updates | Minor cosmetic UI changes. |
Bug Fixes
| Details | |
|---|---|
| Fixes on product stability issues |
|
| Other UI bug fixes |
|
Known Limitations
| Details | |
|---|---|
| Database connection failure occurred in a specific circumstance after upgrading to version 5.11.0 | This issue has been resolved in version 5.11.1. This issue does not affect all cases when upgrading to version 5.11.0. After applying the authentication method
We prepare a Knowledge Base (KB) for troubleshooting the issue and bringing the system back online: How to Troubleshoot an Error related to Connection to Database Failing after an Upgrade to v5.11.0? The issue will not occur in the following scenarios:
|
| Reuse processing result by hash might be slow in high-load situations | This issue has been resolved in version 5.10.1. Since its introduction in version 5.8.0, this feature has helped improve overall performance and reduce significant load when processing similar files. However, we have realized this feature might run slowly in high-load scenarios against large database sizes. |
| Temporary files in the resource folder may not be properly cleaned up if the Archive Extraction engine crashes | Starting from MetaDefender Core version 5.10.1, if the Archive Extraction engine crashes, temporary files from specific extraction transactions may not be properly cleaned up. However, this issue is relatively rare. |
| Reject importing non-empty required_engines setting in containerized environments | This issue occurs only in containerized environments. If the config zip file includes non-empty required_engines setting, MetaDefender Core will reject the import. Workaround:
|
| Button "Revert to Default" in Workflow Rule might not work as expected | This issue has been resolved in version 5.6.0. When modifying settings in Workflow Rule, the ' |
| The Engine Update feature may not work as expected in certain environments | We have observed that the Engine Update feature may not work properly in an environment protected by a [Palo Alto firewall](Palo Alto firewall). In the log file, you might find the error message ' If upgrading to the latest version of MetaDefender Core does not solve the issue, please consider setting up MetaDefender Update Downloader product. This product is responsible for downloading engines, and MetaDefender Core will retrieve and update its engines from there. |
| UI inconvenience on small resolution screens | This issue has been resolved in version 5.5.1. MetaDefender Core version 5.5.0 introduces significant changes to support UI accessibility. However, this leads to an inconvenient issue when displaying Workflow Rule on small or zoomed-in resolution screens. Some tabs at the bottom of the list may not be displayed properly. Workaround: Try zooming out a little bit on the browser. |
| Performance degradation when processing large archive files | This issue has been resolved in MetaDefender Core version 5.5.0 and the Archive Extraction engine version 6.2.1.
|
| Stability issue when encountering malformed data created by the FileType engine | This issue has been resolved in version 5.4.1. The FileType engine version 6.0.2 may generate malformed data, which can negatively impact MetaDefender Core version 5.4.0 or older when written to the PostgreSQL database:
If you experience similar issues, follow these troubleshooting steps to resolve the problem: Rectify malformed FileType data in PostgreSQL database |
| Stability issues on Red Hat / CentOS systems with kernel version 372.13 | MetaDefender Core version 5.2.1 or later may not function correctly with Red Hat or CentOS operating systems that use kernel 372.13. Red Hat is addressing the kernel issues. Please try upgrading to kernel version 372.26. |
| PostgreSQL and MetaDefender Core services cannot initialize in certain containerized environments | This issue was addressed in MetaDefender Core v5.11.1 In a containerized environment, MetaDefender Core version 5.2.0 or newer may work properly when:
Workarounds for older versions:
|
| MetaDefender Core's NGINX web server will not start if weak cipher suites are used for HTTPS | On MetaDefender Core version 5.2.0 and later, OpenSSL 1.x has been replaced by OpenSSL 3.x within the product and its dependencies, including PostgreSQL and NGINX, to enhance security and address known vulnerabilities in OpenSSL 1.x. However, NGINX's implementation of OpenSSL 3.x in MetaDefender Core enforces strong encryption by rejecting all weak cipher suites. It only accepts "HIGH" encryption cipher suites as defined by OpenSSL https://www.openssl.org/docs/man1.1.1/man1/ciphers.html. This means ciphers based on MD5 and SHA1 hashing are no longer supported. Consequently, if you previously configured MetaDefender Core for HTTPS connections using a weak SSL cipher with your certificate, the service will not start due to NGINX's OpenSSL 3.x security enforcement. To prevent and remediate the issue before upgrading MetaDefender Core, please refer to the following resources: HTTPS Failure on MetaDefender Core 5.2.0 (or newer) |
| Archive compression may fail with very large archive files that contain a large number of subfiles | MetaDefender Core has a limitation when compressing very large archive files that contain a high number of subfiles. In our test scenario, it failed when processing an archive with 300,000 or more subfiles. This matter is being researched actively. |