Proactive DLP
v5.17.1
Search this version
Proactive DLP
Proactive DLP
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
Detect intentional data leakage
Copy Markdown
Open in ChatGPT
Open in Claude
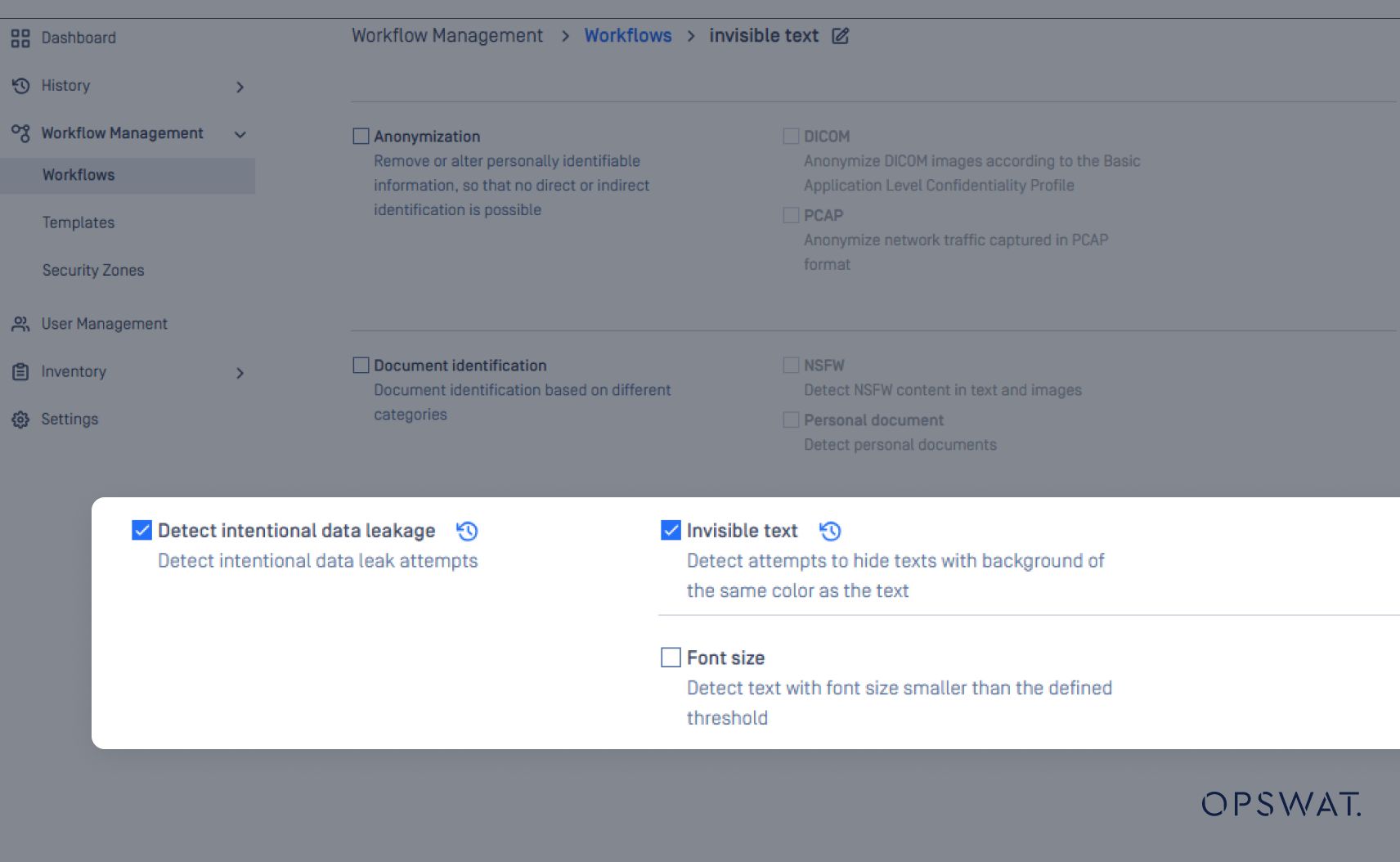
Malicious insiders often employ subtle techniques to evade DLP controls and conceal sensitive information within files or documents. Two common evasion methods include invisible text and small font manipulation, both of which are now detectable through OPSWAT Proactive DLP’s advanced content inspection.
- Invisible Text Detection: Detects hidden or white-colored text embedded within documents or images that is not visible to human reviewers but can still be processed by digital systems. This technique is often used to conceal confidential data, trigger automated workflows, or bypass keyword-based inspection mechanisms.
- Small Font Detection: Identifies attempts to hide sensitive data by using extremely small font sizes that make the content unreadable to the human eye but still machine-detectable. This approach can be used to disguise regulated information such as PII, credentials, or source code snippets within otherwise benign files.
By identifying and flagging hidden content manipulation techniques, OPSWAT Proactive DLP enhances detection accuracy and mitigates the risk of data exfiltration resulting from concealed or obfuscated information within files.
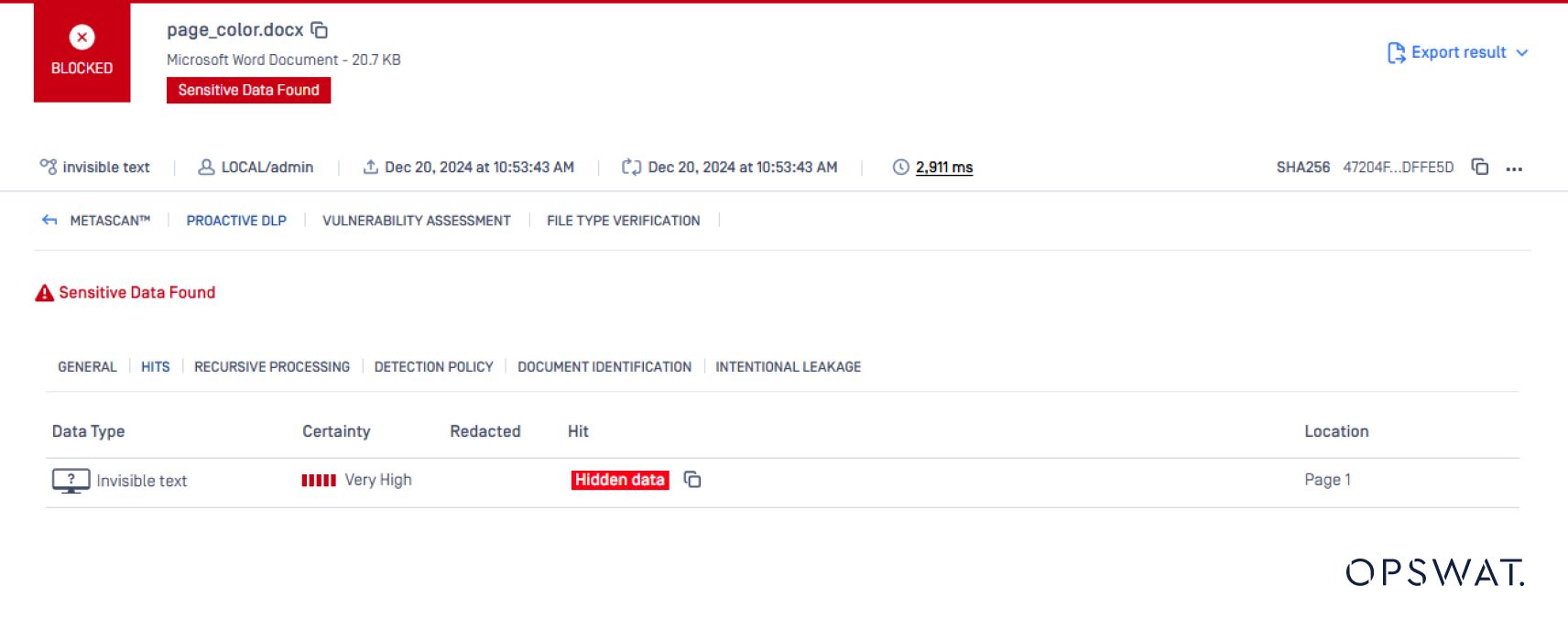
Example:


Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
Was this page helpful?
Next to read:
Performance (Throughput)Discard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message