Title
Create new category
Edit page index title
Edit category
Edit link
EKS Cluster
This guide explains how to use the provisioning script provided by OPSWAT to create an AWS EKS and generate all the Kubernetes components needed to run MetaDefender Core.
Deploy using Terraform
- Locally clone the metadefender-k8s repository and go to terraform folder
git clone git@github.com:OPSWAT/metadefender-k8s.gitcd terraform/aws/Modify variables/variables.tfvars file
- PERSISTENT_DEPLOYMENT=true -> To create K8S cluster with EC2 Worker Nodes
- DEPLOY_FARGATE_NODES=false -> To true if wanted to create a Fargate profile
- DEPLOY_RDS_POSTGRES_DB=true -> To create RDS instance for PostgreSQL server
- POSTGRES_USERNAME -> if DEPLOY_RDS_POSTGRES_DB=true, set up admin database username
- POSTGRES_PASSWORD -> if DEPLOY_RDS_POSTGRES_DB=true, set up admin database password
MD_CLUSTER_NAME = "md-k8s"MD_CLUSTER_REGION = "eu-central-1"ACCESS_KEY_ID = "<ACCESS_KEY_ID>"SECRET_ACCESS_KEY = "<SECRET_ACCESS_KEY>"PERSISTENT_DEPLOYMENT = trueDEPLOY_FARGATE_NODES = falseDEPLOY_RDS_POSTGRES_DB = truePOSTGRES_USERNAME = "<POSTGRES_USERNAME>"POSTGRES_PASSWORD = "<POSTGRES_PASSWORD>"- Run terraform init and apply. Check the resource to be created, after that enter "y"
terraform initterraform applyMetaDefenderK8S script details
Script path: https://github.com/OPSWAT/metadefender-k8s/blob/main/metadefenderk8s.sh
Programming Language: Bash
Installation Pre-requisites for provisioning:
AWS Credentials
- Set in your local environment credentials the IAM user credentials under AWS_ACCESS_KEY_ID& AWS_SECRET_ACCESS_KEY
MetaDefender Core License Key (Required with --mdcore parameter)
- Set it in your local environment credentials under MDCORE_LICENSE_KEY
As security measure do not use the root user for any deployment or operation. Follow the principle of least privilege for all access granted. Keep in mind the resources listed in this page for your option selected: EKS Cluster Architecture
How to run the script
./metadefenderk8s.sh provision -l AWS --mdcoreScript Parameters
| Parameter | Flags | Options | Default | Description | Required/Optional |
|---|---|---|---|---|---|
| Action |
| Action to indicate the script if we want to provision (Create resources + install Core) or install (Install Core) | Required | ||
| Location | -l or --location |
| Where is going to be the K8S cluster | Required | |
| MetaDefender Flag Installation | Combination of
| - | Install MetaDefender Core in the cluster provisioned | Required | |
| Image Version | --image |
| latest | MetaDefender Core image version to install | Optional |
| Region | --region | AWS Regions | eu-central-1 | AWS region where all the resources will be provisioned | Optional |
| Cluster Name | --name | Not uppercase allowed | md-k8s | Name of the cluster that will be used for naming all the resources | Optional |
| Number of Replicas | --replicas | [0-9]* | 1 | Number of replicas for MetaDefender Core service | Optional |
| Namespace | --namespace | [A-Za-z]{1,10} | Namespace where MetaDefender products will be installed in the K8S Cluster | Optional Max Characters: 10 |
Limitations using parameters
- When using Fargate
- the pods should be installed in the default namespace.
- if using AWS Load Balancer controllers need a worker node to be installed in.
The script will deploy a single Worker Node for the cluster with enough space for 1 replica of MD Core. AWS EC2 Instance size is c5.2xlarge (8 vCPU & 16 GiB Memory). Each pod would request 7 vCPU and 8 GiB Memory. To change the request to adapt each pod to the specific case go to values.yml To change the node group go to the terraform file terraform/aws/eks_cluster_module
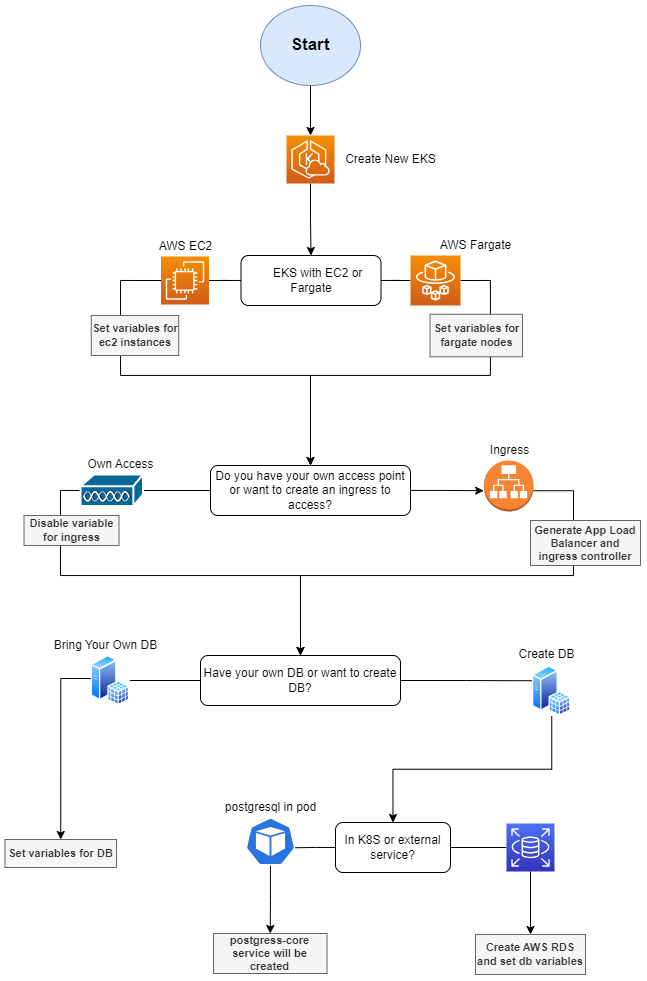
MetaDefender Core Flowchart Provisioning in AWS
The following flowchart represents how the provisioning script will configure the environment based on the options selected for provisioning AWS EKS.
Summary options to be selected
EKS with EC2 or Fargate
Access to the K8S cluster. Generate Ingress or provide own access.
- An Ingress will be create per each product flag added as parameter to the script
- Own Access, you decide how to access to the cluster so it won't generate any load balancer for accessing
Have your own database or create new database
- Own database, will be asked if you want the script to set up the credentials and database host url for you or the script will just indicate the secrets to edit, later on by you, for connecting the MetaDefender Core with your database.
- Create new DB in K8S or external DB that for AWS we will provision a RDS instance