Overview MetaDefender Sandbox API Reference Release Notes
Getting Started
Deployment & Usage
Support
Overview
3.0.0
Search this version
Overview
Overview
Overview
Zero-Day Detection Pipeline
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
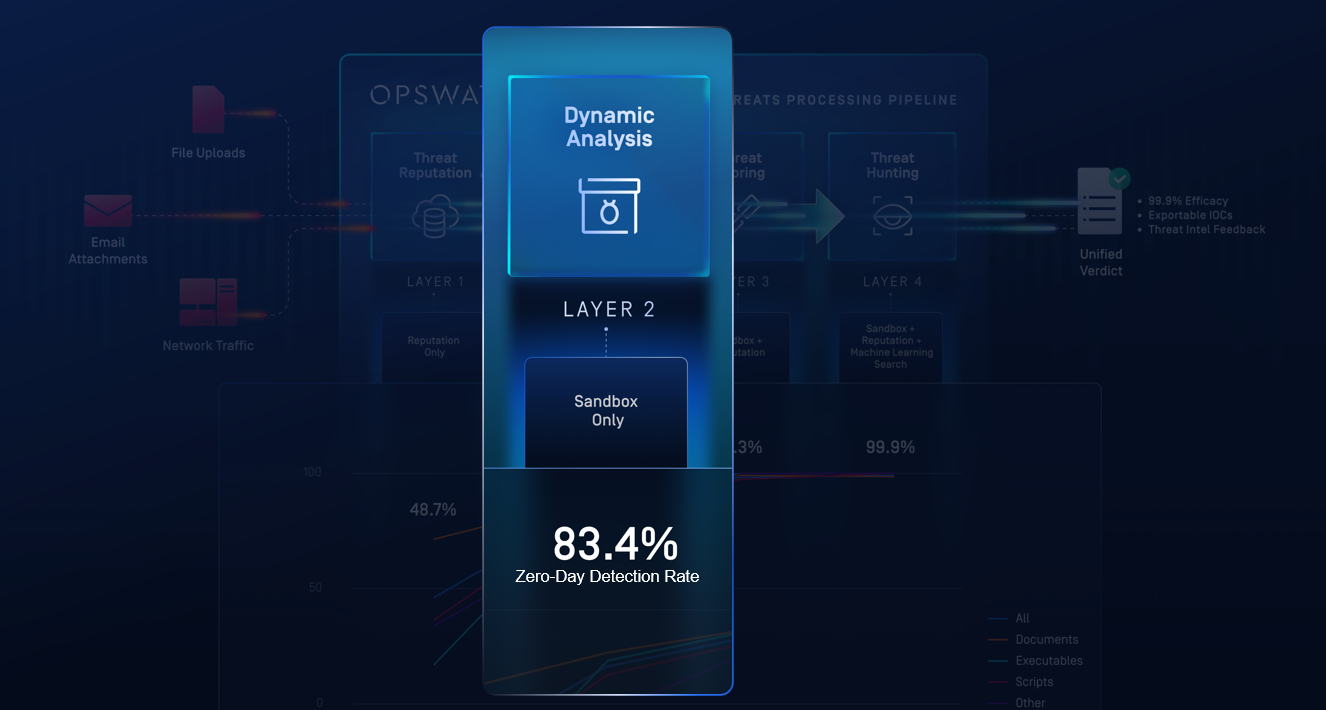
Layer 2 - Dynamic Analysis
Copy Markdown
Open in ChatGPT
Open in Claude
Unknown and suspicious files are executed in an emulation-based sandbox that bypasses anti-VM and timing-based evasion. Runtime behaviors, loader chains, scripts, and artifacts are exposed even when malware tries to stay dormant.
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
Was this page helpful?
Next to read:
Sandbox Engine FeaturesSee the "Technical Datasheet" for a complete list of features: https://docs.opswat.com/filescan/datasheet/technical-datasheet
Discard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message

