Title
Create new category
Edit page index title
Edit category
Edit link
Supply Chain Threats
#1 Supply Chain Attack
Detection Spotlight:
The SolarWinds supply chain attack exemplifies how minimal code changes in trusted software can enable massive breaches while bypassing traditional security defenses. Threat actors injected a stealthy backdoor into a legitimate DLL, embedding malicious logic while preserving original functionality. The payload ran silently in a parallel thread mimicking legitimate components. With a valid digital signature and seamless behavior, the DLL evaded detection and granted covert access to thousands of high-profile victims. The compromise of the build pipeline turned trusted updates into a vehicle for global intrusion.
While a 4,000-line backdoor might seem significant, in the context of a large enterprise source code, it’s easily overlooked. This is where MetaDefender Aether excels: it doesn’t just inspect the code, it observes what the software does. It flags deviations from normal behavior, guiding analysts to what really matters—cutting through the noise to spotlight threats that traditional reviews would likely miss.
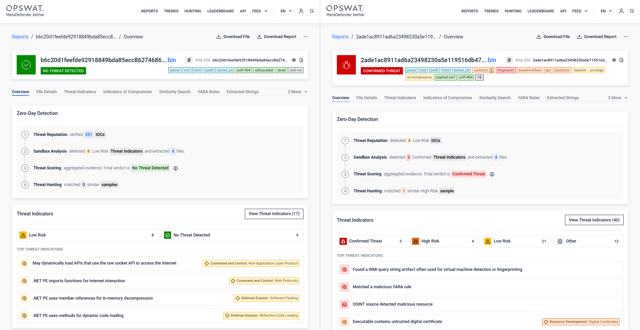
On the left, we see the legitimate DLL file. On the right is the trojanized version responsible for the infamous SolarWinds incident.
Let’s walk through the key findings as revealed by the sandbox analysis:
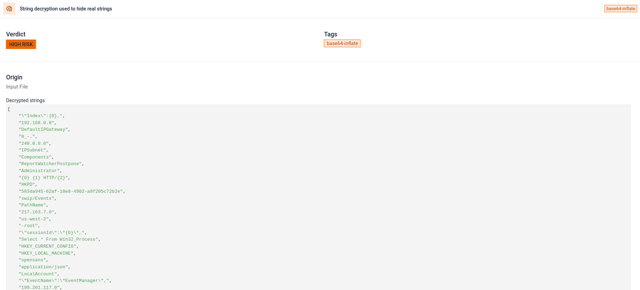
String encryption: the code employs a typical obfuscation technique found in various malware: compression followed by base64 encoding.
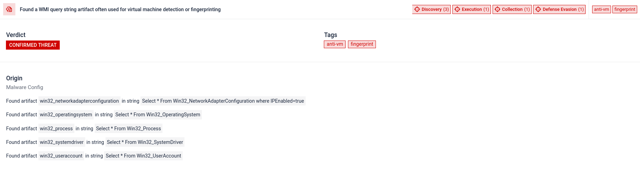
WMI queries commonly associated with system fingerprinting. In this case, the related strings were encrypted to avoid detection.
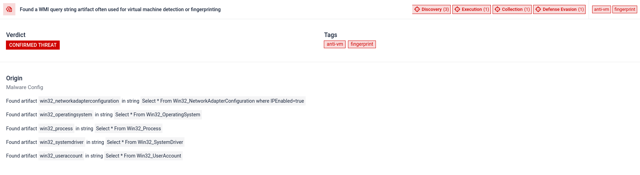
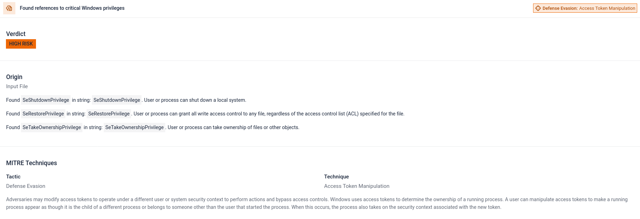
Multiple indicators tied to privilege escalation, user identity spoofing, and access control tampering.
#2 Detect malicious Pickle within AI model
Detection Spotlight:
AI is powering everything from chatbots to business tools. To move faster, companies often use pre-trained AI models shared online through open source platforms like Hugging face. These models are saved in complex formats such as Pickle and PyTorch.
While it is convenience, this usage opens a new risk. Attackers can hide malware inside AI models, especially in Pickle files. Because Pickle can store both data and executable code, it has become a common vehicle for supply chain attacks. A model downloaded from a public repository may look safe but could trigger hidden instructions the moment it is loaded.
A recent case showed how attackers abused the reputation of Alibaba AI brand as a lure to publish fake PyPI packages containing a malicious AI model. These packages seem legitimate but contained hidden code to steal user's data and send it to the attacker. Although the packages were available for less than 24 hours on May 19, they were downloaded about 1,600 times. This shows how quickly malicious software can spread through a supply chain attack.
MetaDefender Aether uncovers these threats through dedicated Pickle and PyTorch scanning capabilities.
Multiple Pickle scanning methods from Third-party tools to Deep Static Analysis
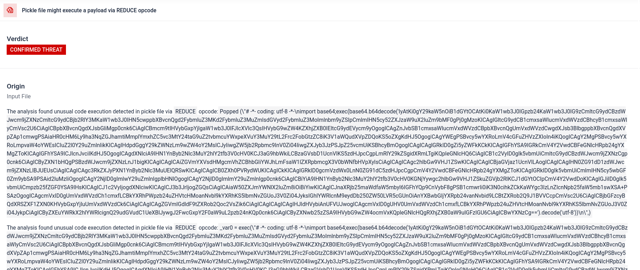
REDUCE may be abused for arbitrary code execution and to embed malware in Pickle
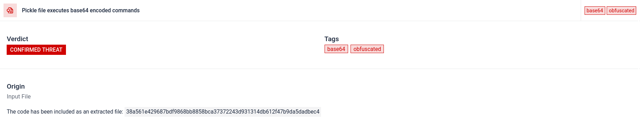
Uncovering encoded payload
See the "Technical Datasheet" for a complete list of features: https://docs.opswat.com/filescan/datasheet/technical-datasheet

