Title
Create new category
Edit page index title
Edit category
Edit link
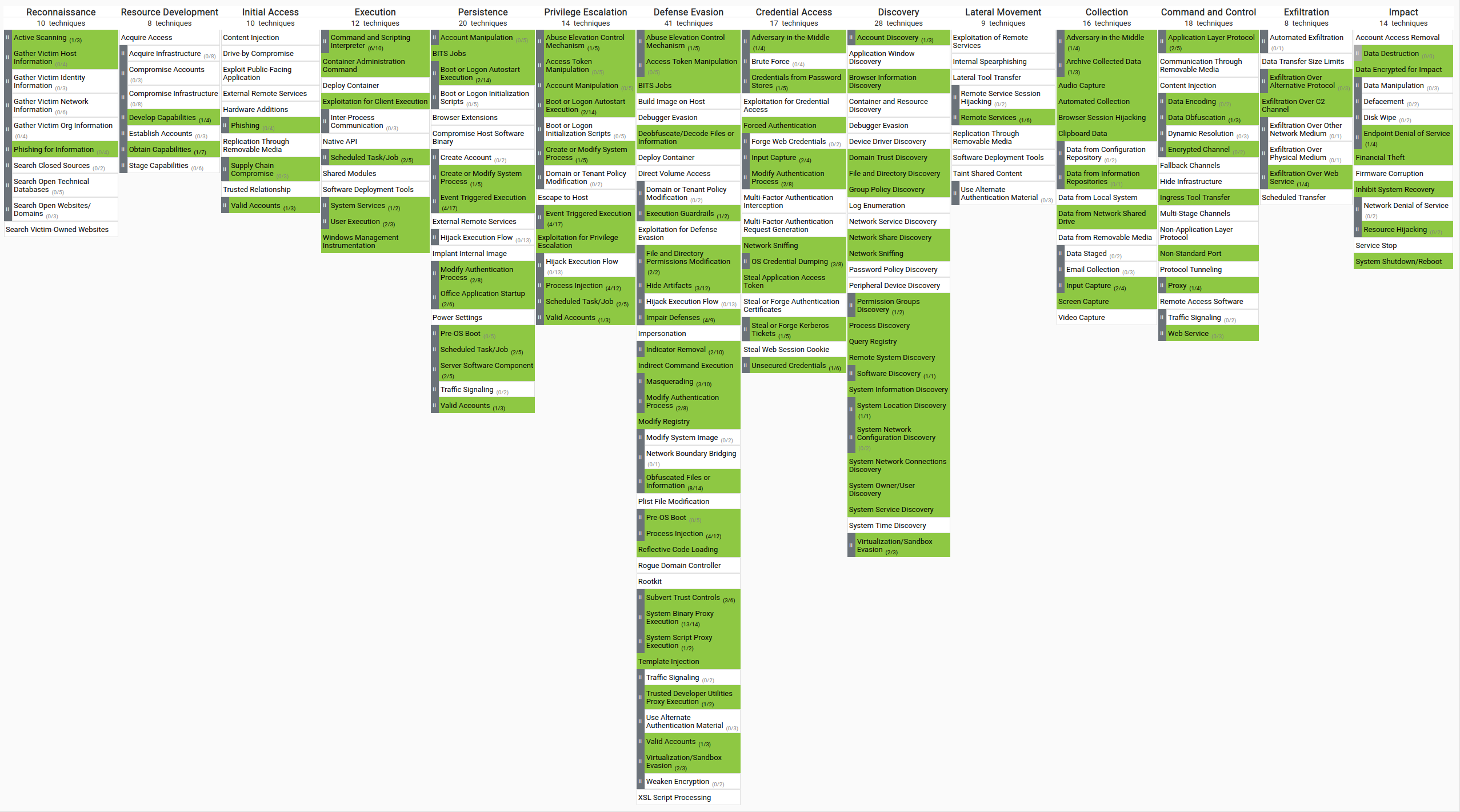
MITRE ATT&CK Coverage
MITRE ATT&CK Coverage in Our MetaDefender Aether Solution
Our solution is designed to detect and analyze malicious behaviors, focusing on key tactics within the MITRE ATT&CK framework. While we provide comprehensive coverage for techniques related to file-based threats, such as:
- Initial Access (e.g., phishing attachments, exploit delivery)
- Execution (e.g., script execution, user-initiated actions)
- Persistence & Defense Evasion (e.g., malicious service creation, obfuscation)
- Credential Access & Collection (e.g., keylogging, credential dumping)
Complete coverage of the entire MITRE framework is not the goal of sandbox technology. Techniques involving live network activity, user behavior manipulation, or system-wide lateral movement require continuous monitoring tools like EDR, SIEM, or endpoint agents. Our current MITRE framework coverage is 37%, rising to 54% when considering only the high-impact tactics mentioned above.
Our sandbox excels in detecting evasive malware and zero-day threats within isolated environments. For holistic threat detection, it complements broader security ecosystems through API integrations with other defense technologies.
MITRE Enterprise Matrix
MITRE Mobile Matrix
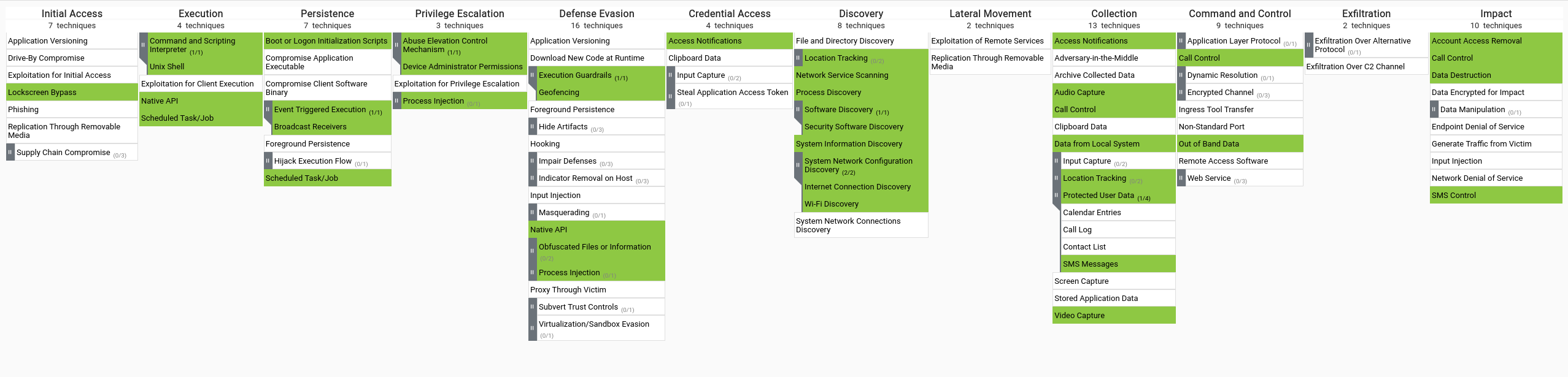
You can check the full resolution image by clicking in the links below:
See the "Technical Datasheet" for a complete list of features: https://docs.opswat.com/filescan/datasheet/technical-datasheet