This feature allows the sandbox to reveal hidden artifacts embedded within PE files. Malicious artifacts are often encoded and/or encrypted to evade detection and obscure the sample's true intent. Uncovering these artifacts is essential, as they typically contain critical data, such as C2 information or payloads. By extracting them, the sandbox can perform a deeper scan, increasing the likelihood of identifying valuable IOCs.
PE Resource XOR Decryption
Storing payloads in PE resources helps malware evade detection by static analysis tools. Many security tools focus on analyzing the executable’s main code section, while resources are often overlooked, making it easier to hide malicious content.
Why XOR encryption? It is widely used for its simplicity and efficiency in evading detection, but one key property of XOR is that when a bit is XORed with 0, the original bit remains unchanged. This characteristic makes XOR encryption particularly "weak" when applied to data with a large number of null bytes, such as those often found in PE files. By analyzing patterns in the encrypted data, especially in areas with many null bytes, the encryption key can be revealed, allowing to decrypt the hidden.
This sample is a malware loader that contains a encrypted payload in a resource.
On the following link you can find the sample from the screenshot below:
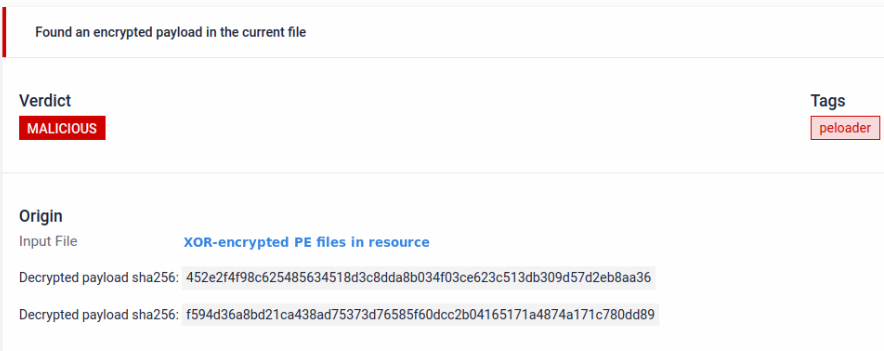
Hidden payload in PE resource
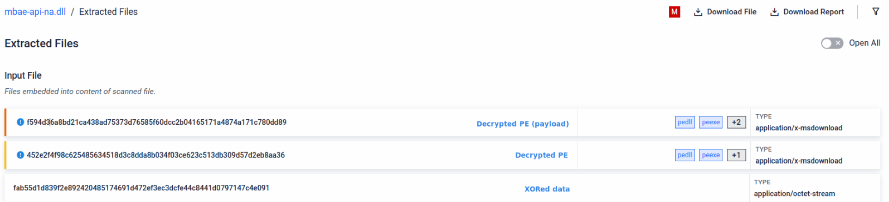
Payload extracted after XOR decryption
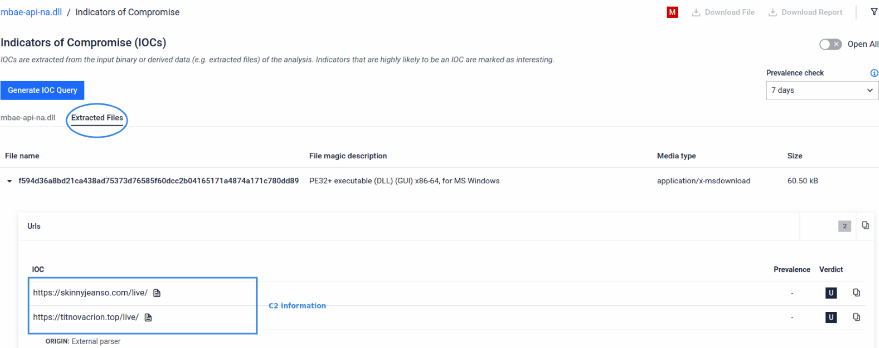
C2 information identified from the payload
Base64-encoded embedded files
Malicious actors embed base64-encoded content, such as executables, archives, or documents within seemingly benign text-based or document files, using them as decoys to evade detection. A more advanced observed evasion technique involves reversing base64-encoded content to bypass detection mechanisms.
MetaDefender Sandbox identifies these potentially malicious embedded files, extracts them, and analyzes their true functionality.
The following sample shows a malicious .NET DLL embedded as a base64-encoded string within an image file
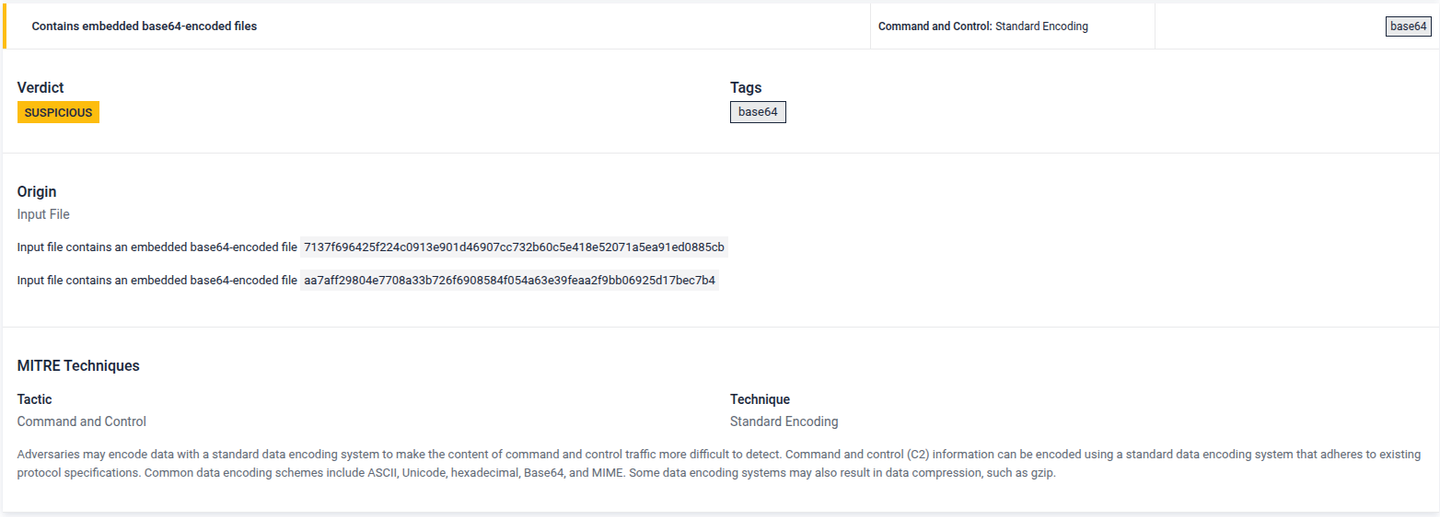
Detected embedded base64-encoded files
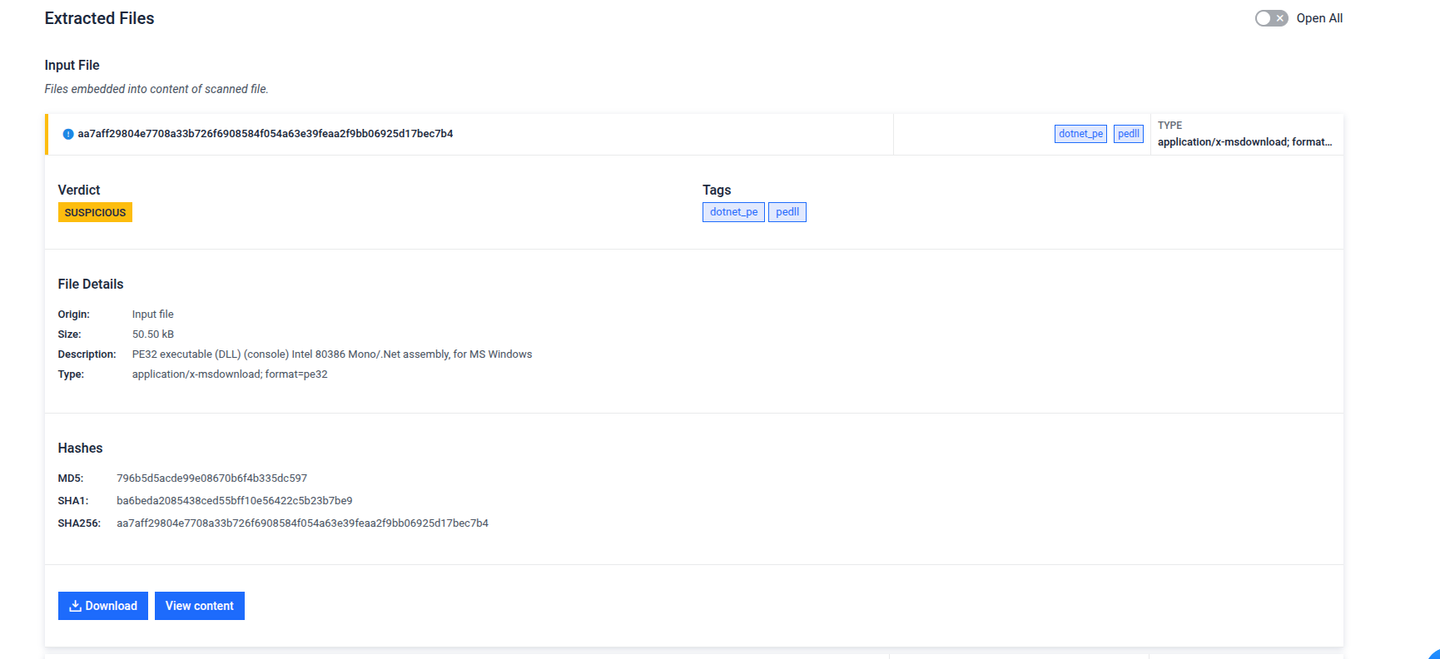
The extracted .NET dll file that triggers threat indicators

