Title
Create new category
Edit page index title
Edit category
Edit link
Adaptive Sandbox Full Report Overview
This is an introduction to the MetaDefender Sandbox Full Report (Remote module).
Overview
Provides an overview of recent analysis activities and user statistics.
Link to report: Filescan.IO - Analysis Report for 9e7d694ed87ae95f9c25af5f3a5cea76188cd7c1c91ce49c92e25585f232d98e - Overview
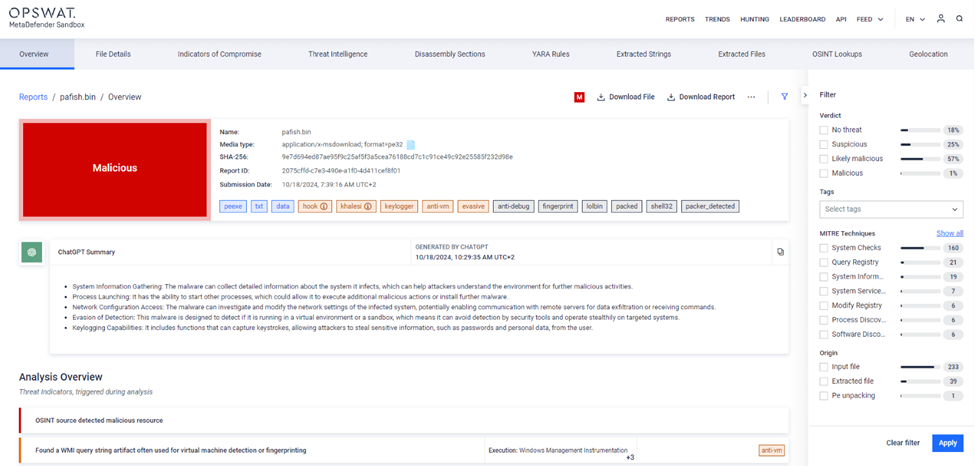
Overview includes the following
Submission Info
Including the Name: File Name
Mediatype: Type or format of a file being analyzed
Hash: The unique ID of the file hashing calculation
Report ID: The unique ID for the Report
Submission Date: The timestamp of the scan
Tags
- Tags are used to categorize or label files based on specific attributes, behaviors, or detected threats. These tags help users to highlight important information like file origin, vulnerability types, or known malware families.
ChatGPT
- To help get summary using the ChatGPT integration.
Analysis Overview
The analysis overview includes all malicious results the Sandbox detected, for all verdicts, please see: https://docs.opswat.com/filescan/datasheet/verdict
- Threat Indicators: They highlight potential malicious activities, suspicious behaviors or benign activities in files.
- E.g. OSINT source detected malicious resource: Indicates a file or URL linked to a known malicious source based on Open Source Intelligence (OSINT).
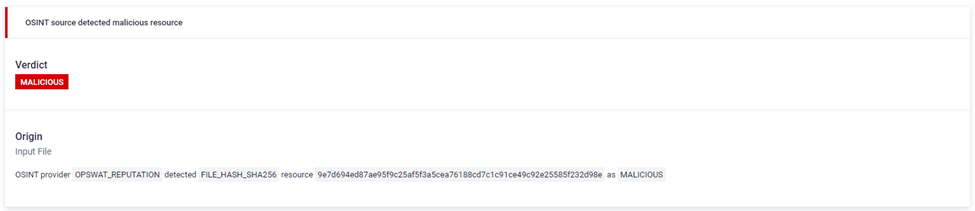
Filters
With the help of the side panel, the user can filter down for verdict, tags, MITRE Techniques and Origin
- MITRE Techniques
- It allows users to identify and categorize specific techniques used by malware or attackers, as defined by the MITRE ATT&CK framework
File Details
It is comprehensive information about a specific file, including its hash, file type, size, and origin. This may also include metadata like version information, or the software used to create it. This feature is useful for analyzing potentially malicious files and understanding their characteristics.
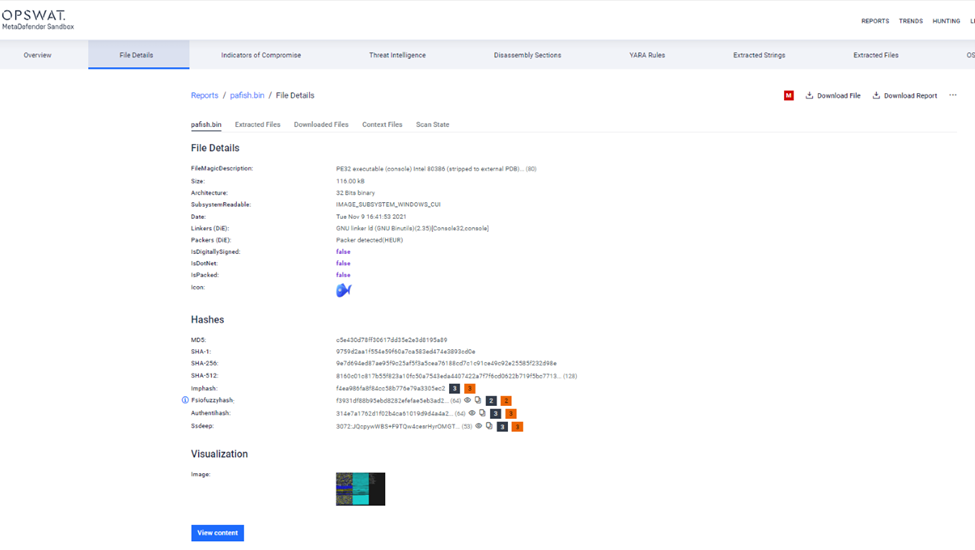
Extended Details
This section dives deeper into the file's characteristics, possibly including information about its compilation, digital signatures, and other technical details.
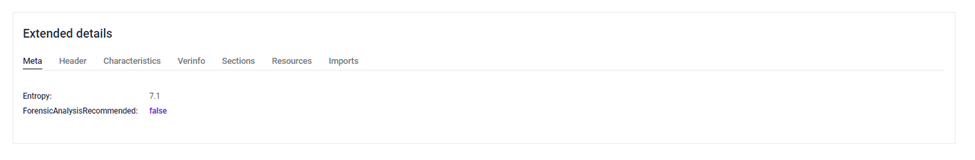
- Entropy: 7.1: This suggests a moderate level of randomness in the file, which can indicate potential encryption or obfuscation. Higher entropy values often raise red flags as they might signal that the file is hiding something.
- ForensicAnalysisRecommended: false: This means that, based on the analysis, there’s no immediate need for a deeper forensic examination, which could imply that the file doesn't exhibit known signs of being malicious.
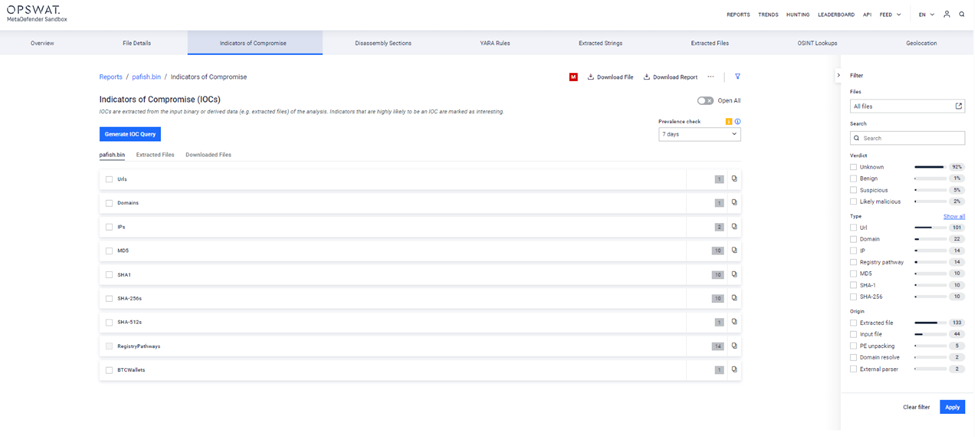
Indicators of Compromise (IOCs)
IOCs are extracted from the input binary or derived data (e.g. extracted files) of the analysis. Indicators that are highly likely to be an IOC are marked as interesting.
Threat Intelligence
Scan and analyze files with more than 300 features and match complex patterns in known malicious files to hunt threats and identify new and unknown malware. During the similarity search, files undergo a rigorous scanning procedure using the MetaDefender Sandbox static and file emulation technologies. This advanced technology extracts the most relevant and useful information from a given file.
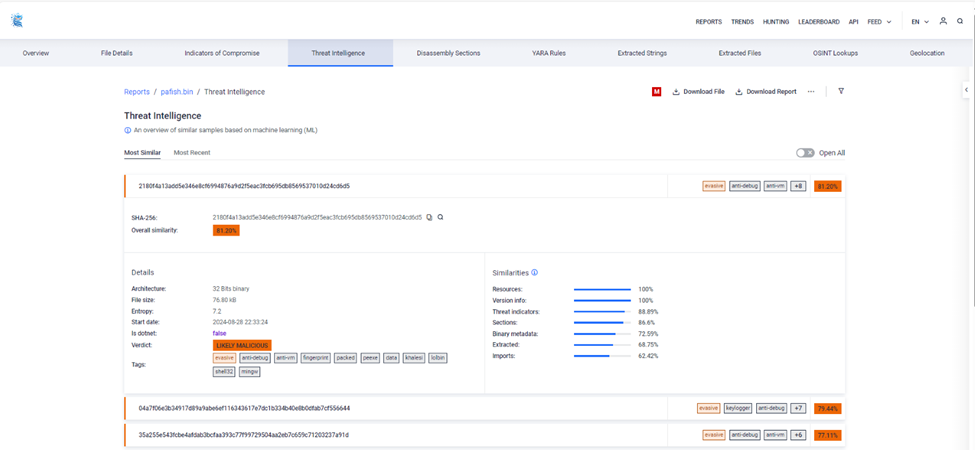
Learn more about Threat Intelligence here: https://docs.opswat.com/filescan/operationalguide/similarity-search
Disassembly Section
This can be particularly useful for reverse engineering, malware analysis, or debugging purposes. In this section, you can see how the code is structured, which instructions are executed, and how different components of the file interact with each other.
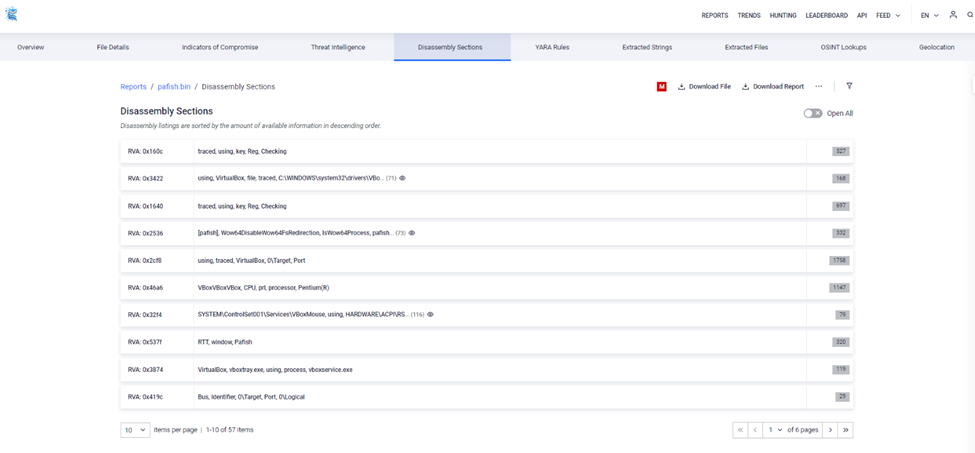
Learn more about Disassembly here: https://docs.opswat.com/filescan/datasheet/showcase-reports#6-finding-interesting-things-via-disassembly
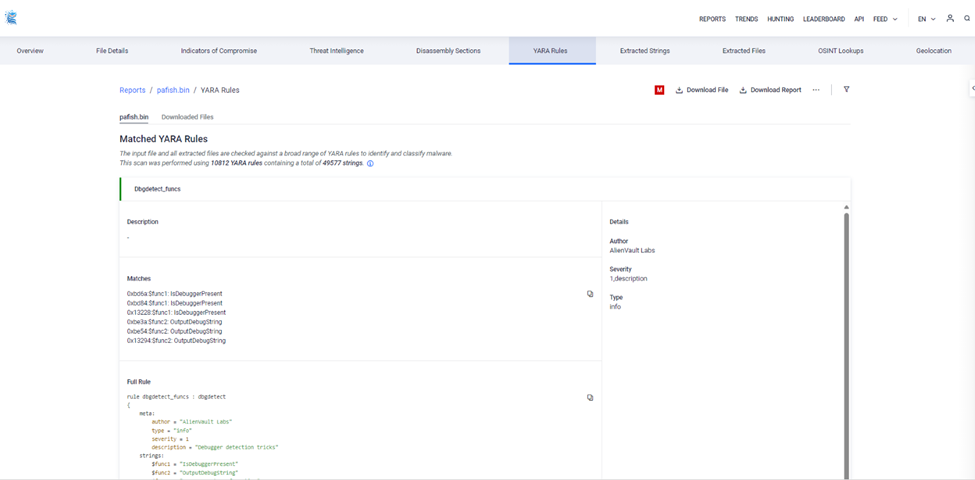
YARA Rules
It is used for identifying and classifying malware or suspicious files based on specific patterns. YARA, which stands for "Yet Another Recursive Acronym," allows users to create rules that can match certain characteristics within files, such as strings or byte sequences.
Extracted Strings
Further information that can be extracted from the file meta data.
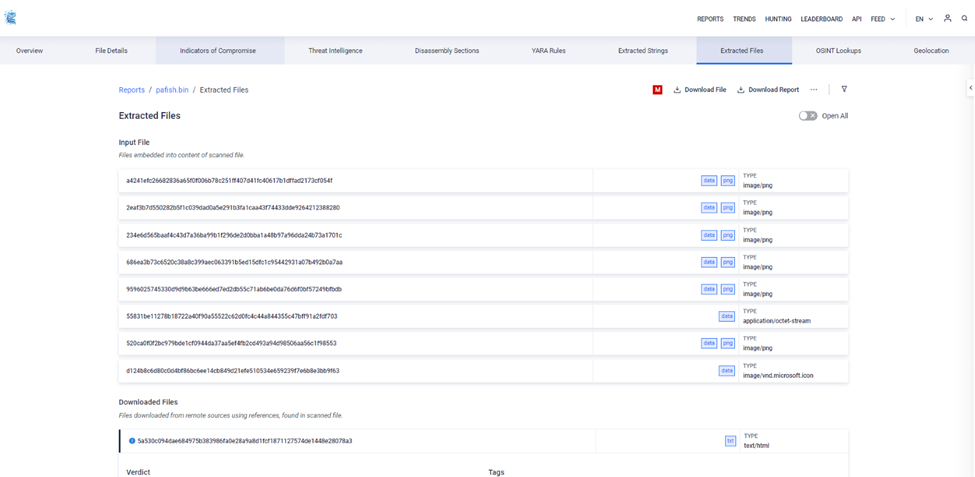
Extracted files
The list of files that have been extracted from a scanned archive or binary. This feature is useful for analyzing the contents of complex files, such as executables or compressed archives, where multiple files may be contained within.
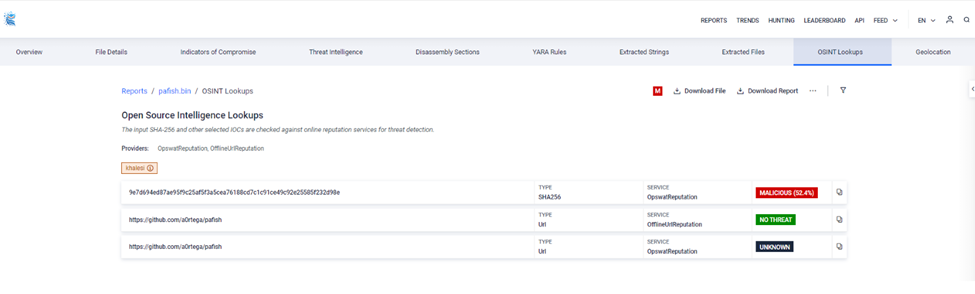
OSINT Lookups
OSINT utilizes the hash and other IOCs to check against the online reputation services to make sure that the file is safe, it also lists out the malicious components as tags for better awareness.
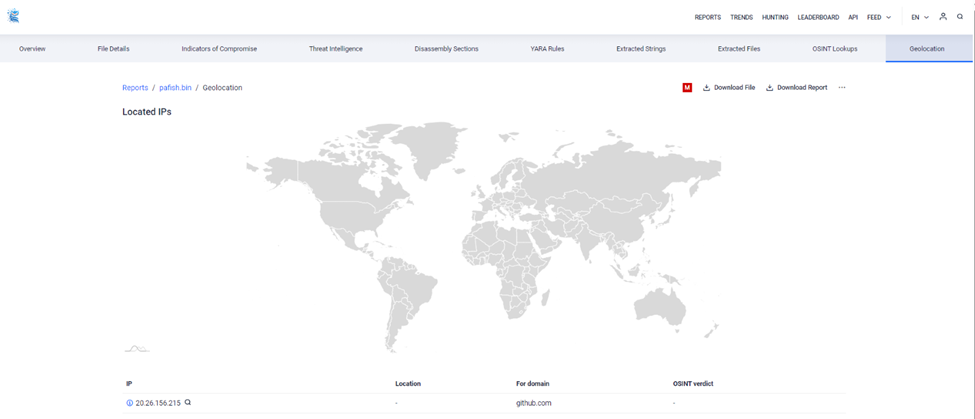
Geolocation
The geolocation feature provides information about the geographical locations associated with a file, typically based on its network activity or the IP addresses it may communicate with.
If Further Assistance is required, please proceed to log a support case or chatting with our support engineer.
See the "Technical Datasheet" for a complete list of features: https://docs.opswat.com/filescan/datasheet/technical-datasheet

