Configuration
3.4.4
Search this version
Configuration
Configuration
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
AD FS Specific Configuration
Copy Markdown
Open in ChatGPT
Open in Claude
To properly access MDSS, the following AD Security Groups are required:
- SsoAdministrator - the equivalent of local MetaDefender Storage Security administrator role
- SsoReadOnlyAdministrator - the equivalent of local MetaDefender Storage Security read-only role
It is also necessary for the AD user to have an email address set up, so that it is set as the MetaDefender Storage Security's user email
To set up AD FS SSO for MDSS, follow these steps:
- Within the AD FS settings, navigate to the "Scope Descriptions" directory and click "Add Scope Description"
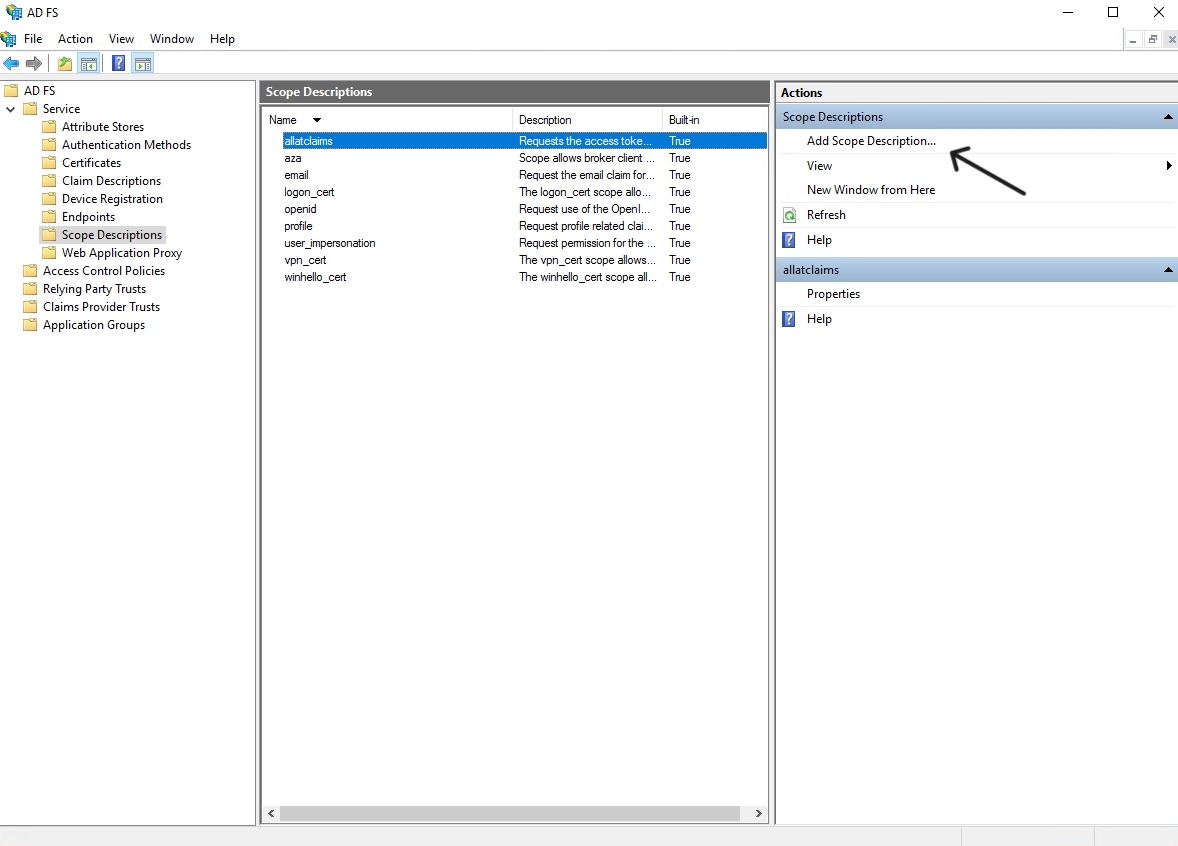
- Create a scope with the name "offline_access"
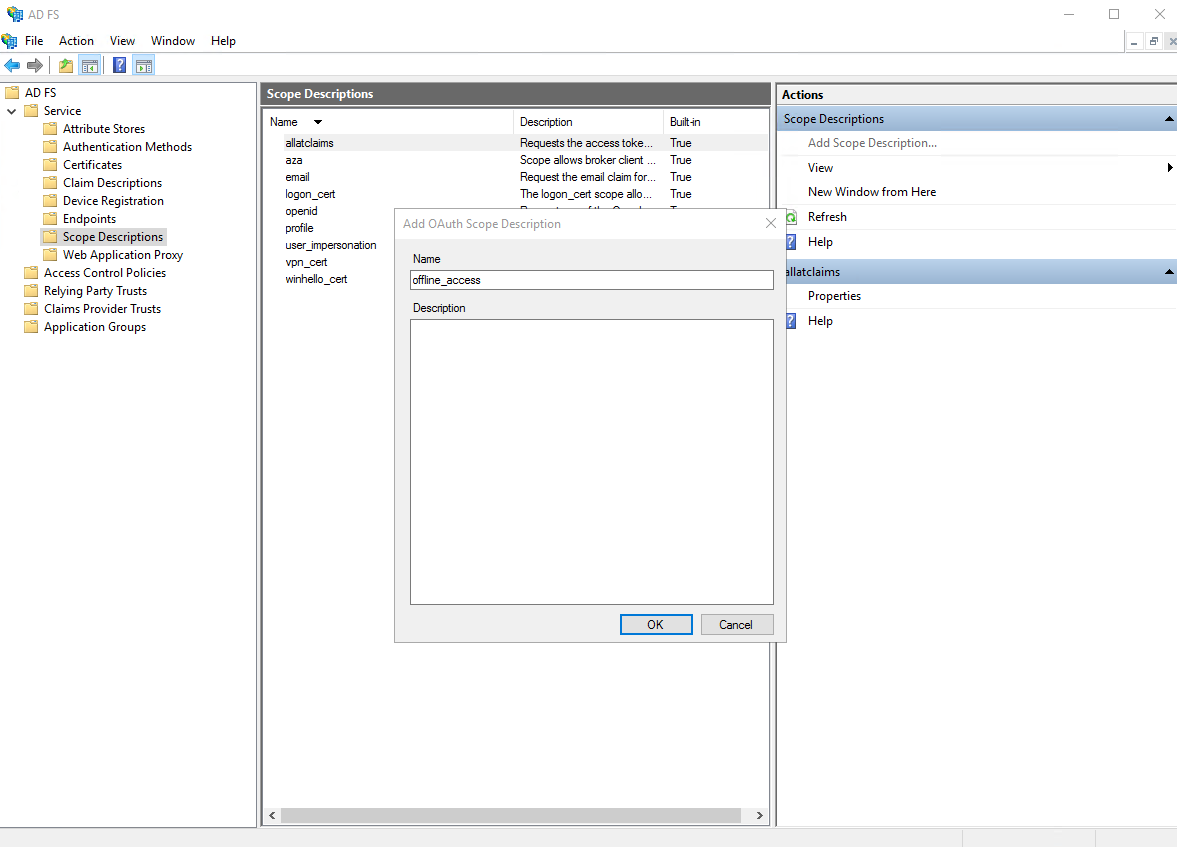
- Navigate to the "Application groups" directory and click "Add Application Group"
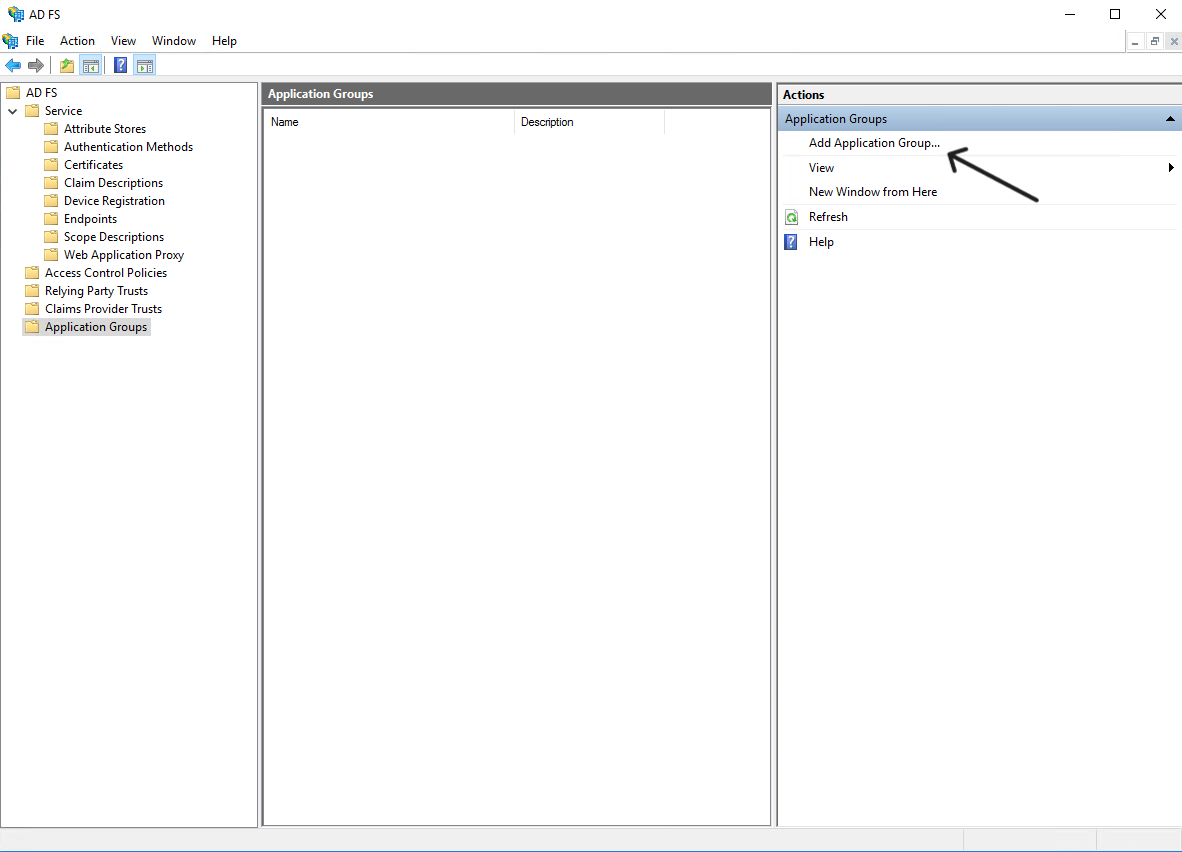
- Give your application any name you like and for the template, select "Server application accessing a web API"

- Give the server app a name, save the generated Client Identifier somewhere, and as the "Redirect URI", write the the base URL of the MDSS deployment, followed by the "/callback" suffix.
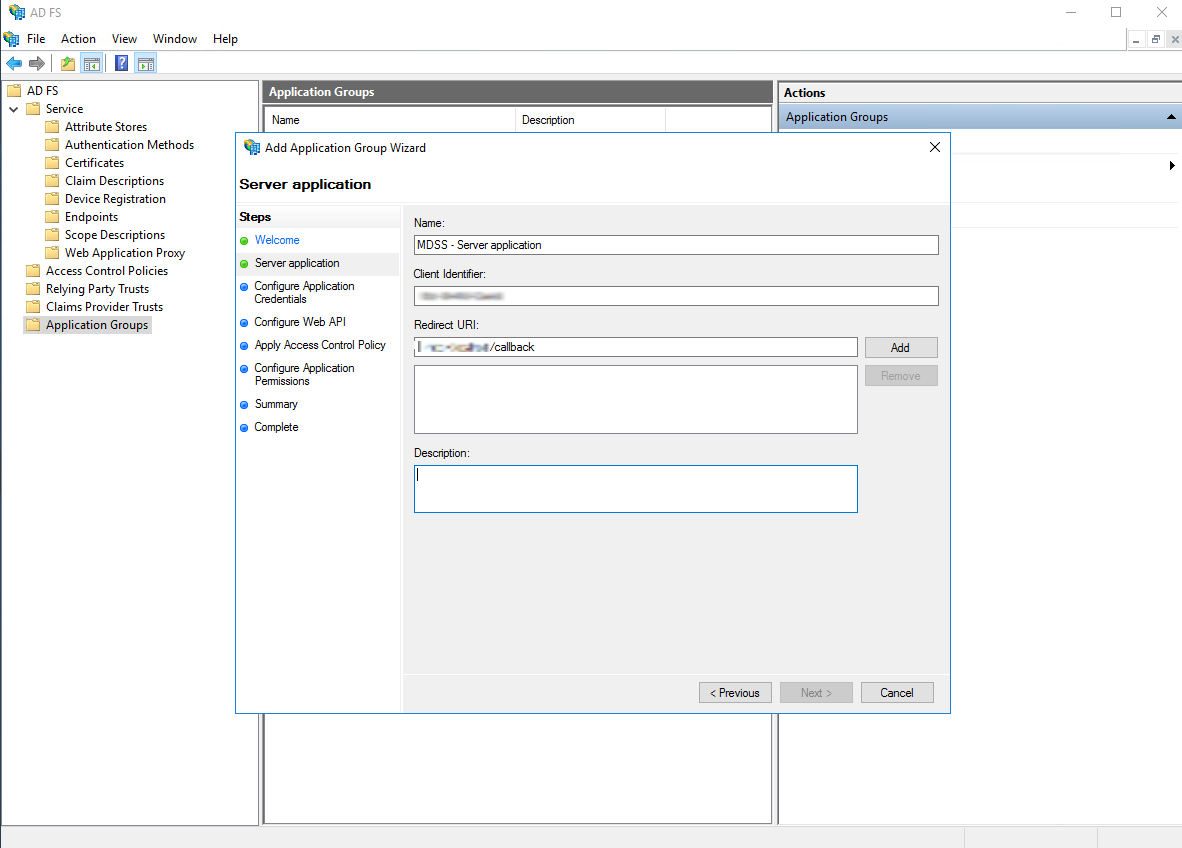
- Select "Generate a shared secret" and store the secret somewhere
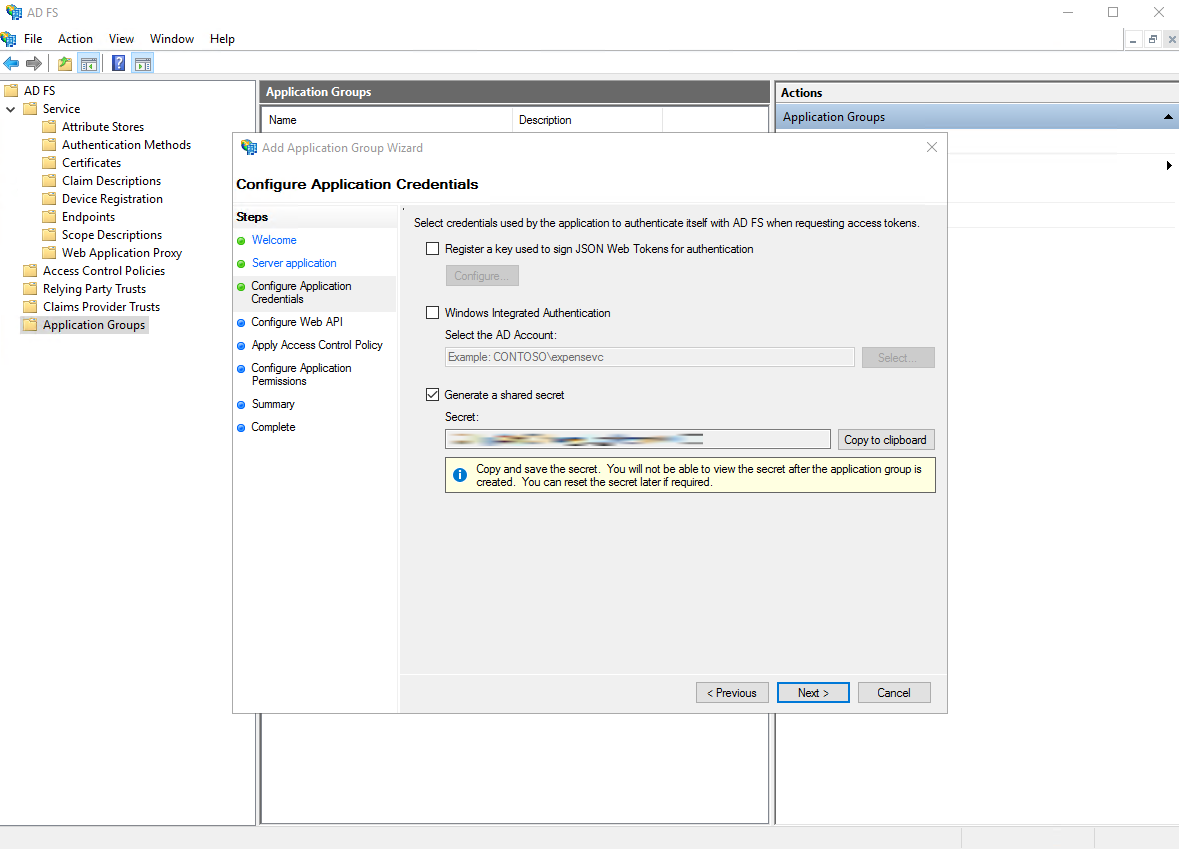
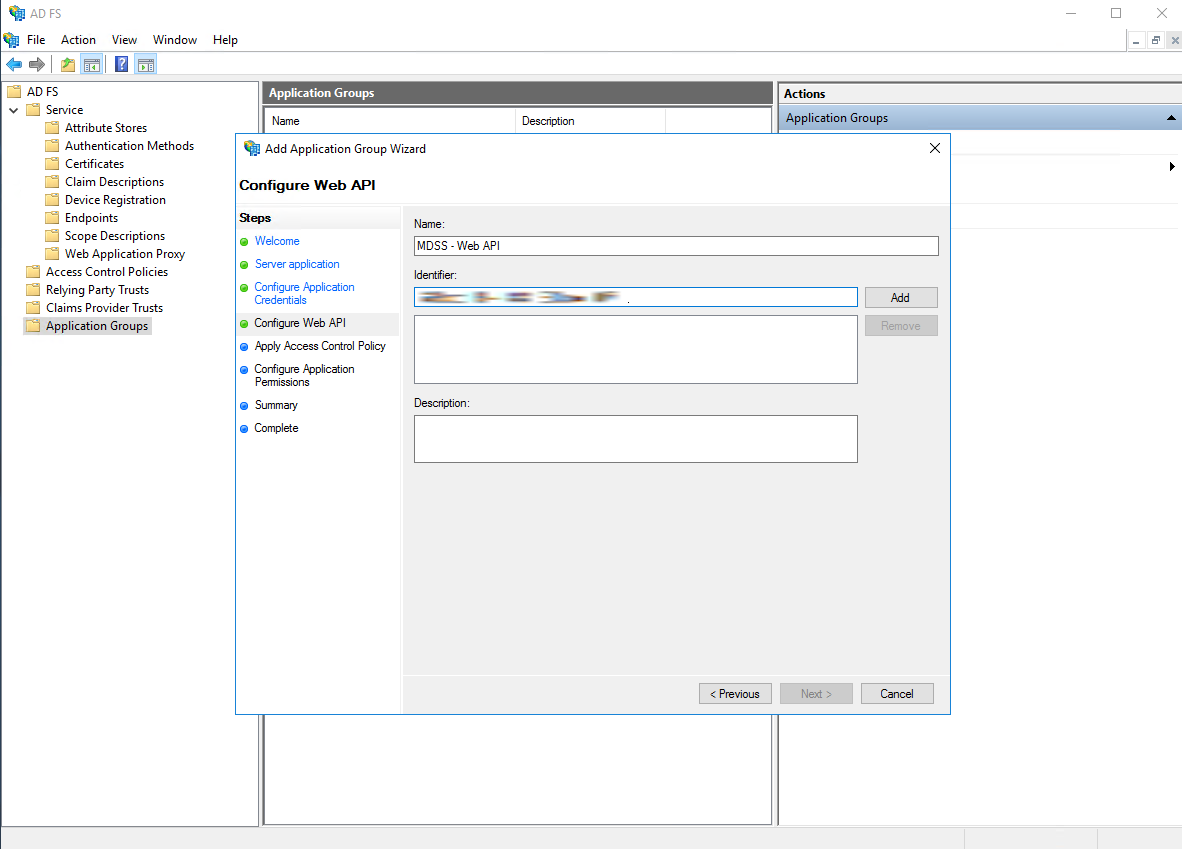
- For the "Identifier" field, put the previously generated Client Identifier that you saved
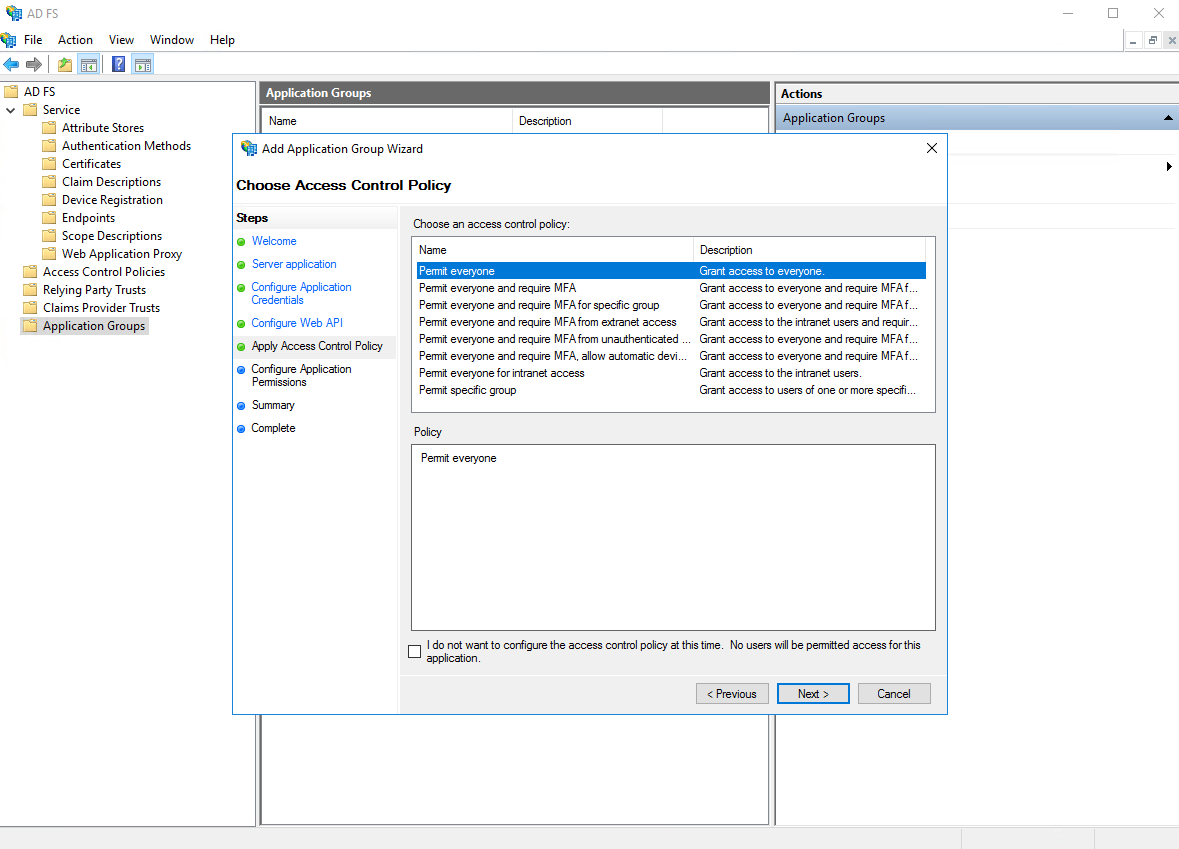
- For the access control policy, select "Permit everyone"
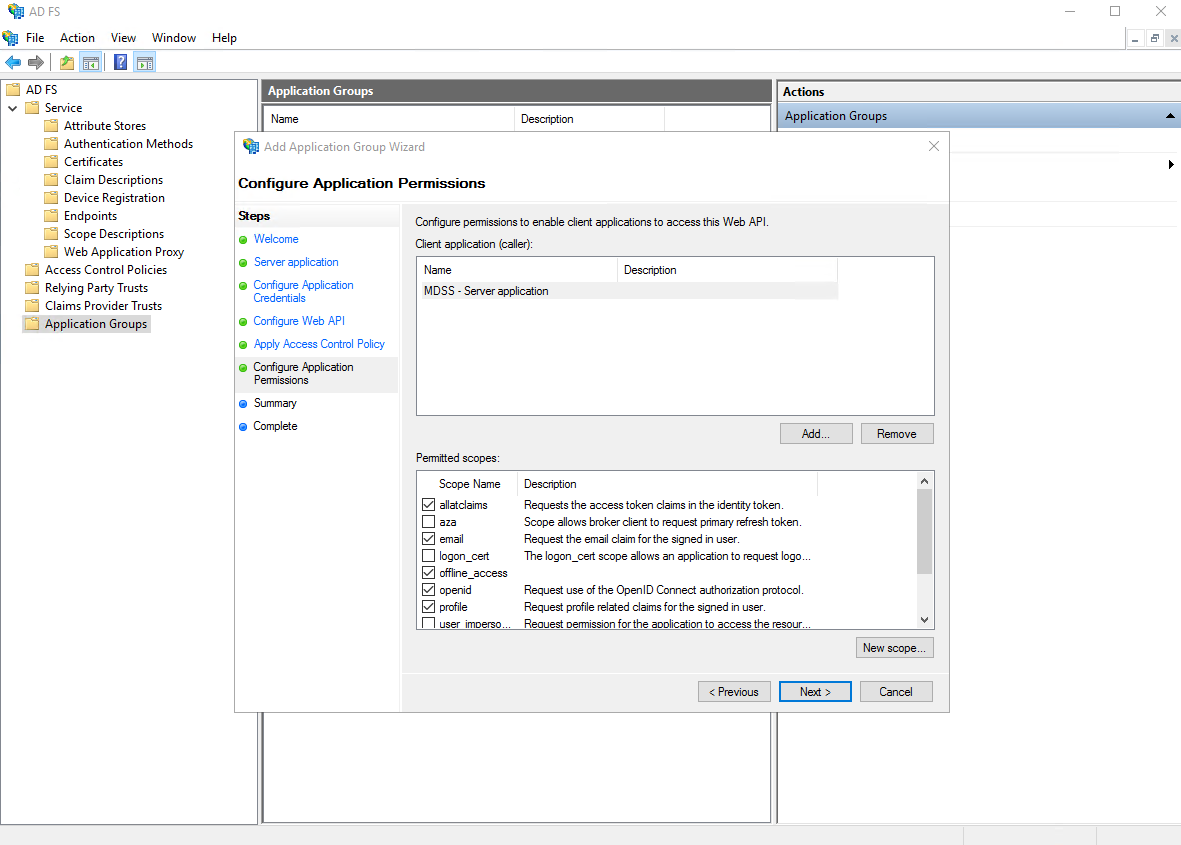
- For the permitted scopes, select the following from the list: allatclaims, email, offline_access, openid, profile
- After saving the created application group, select it and click on Properties
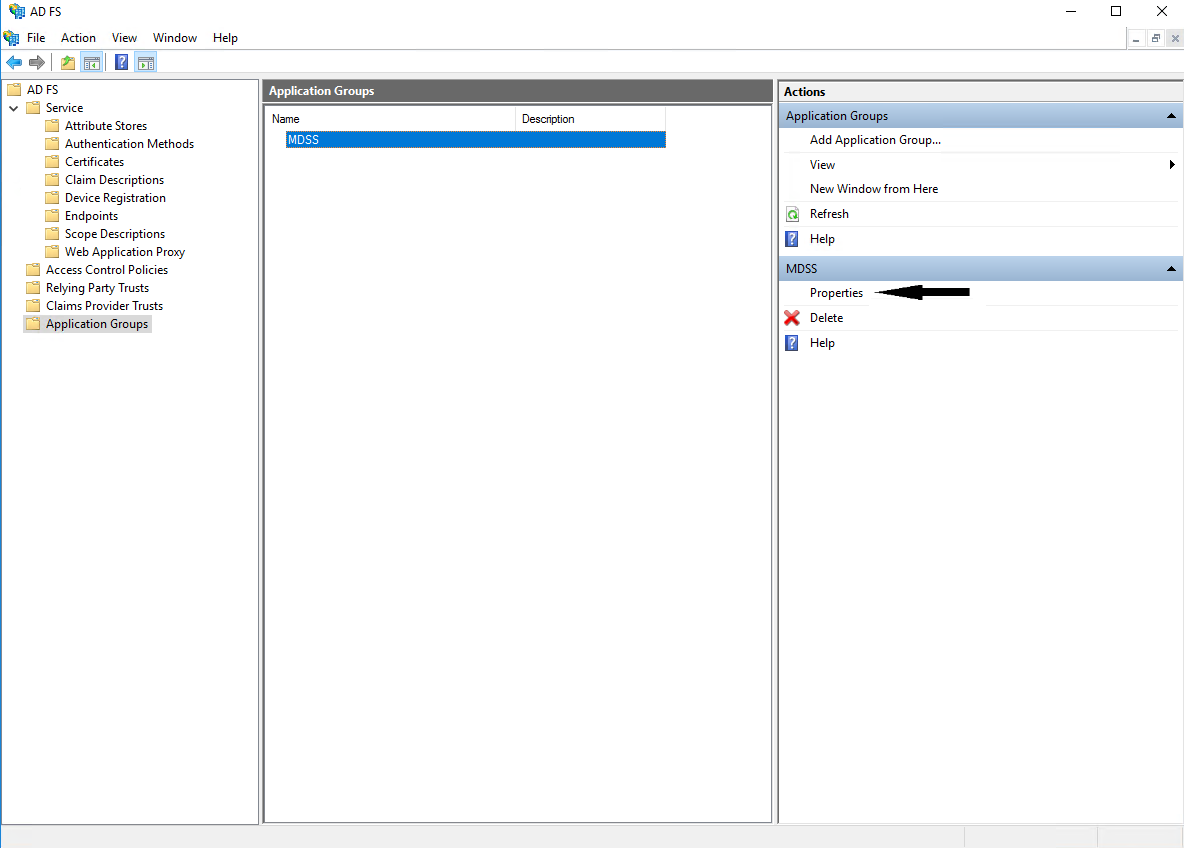
- Select the configured Web API and click on Edit
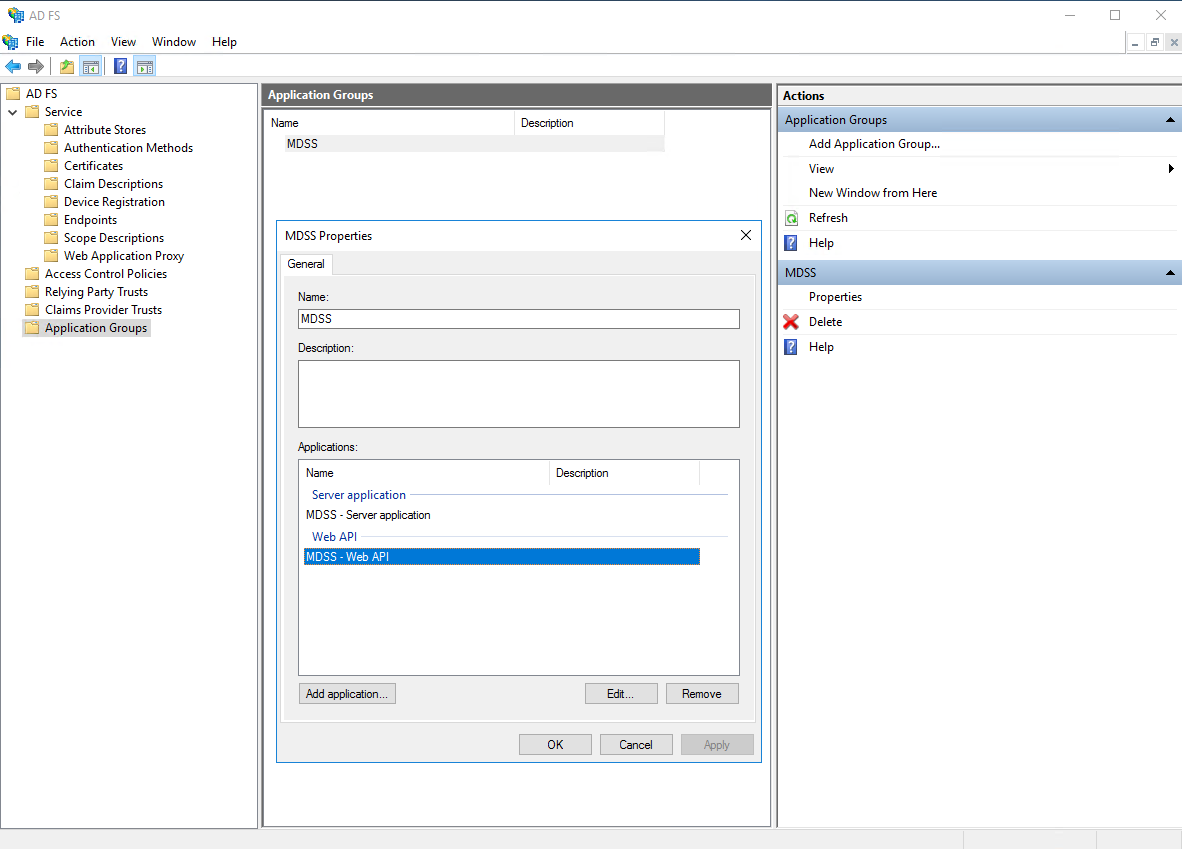
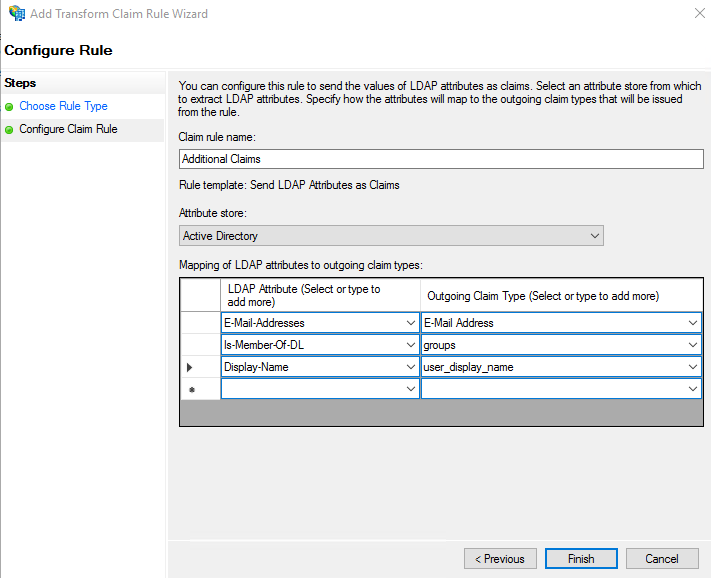
- Go to "Issuance Transform Rules" and click "Add Rule"
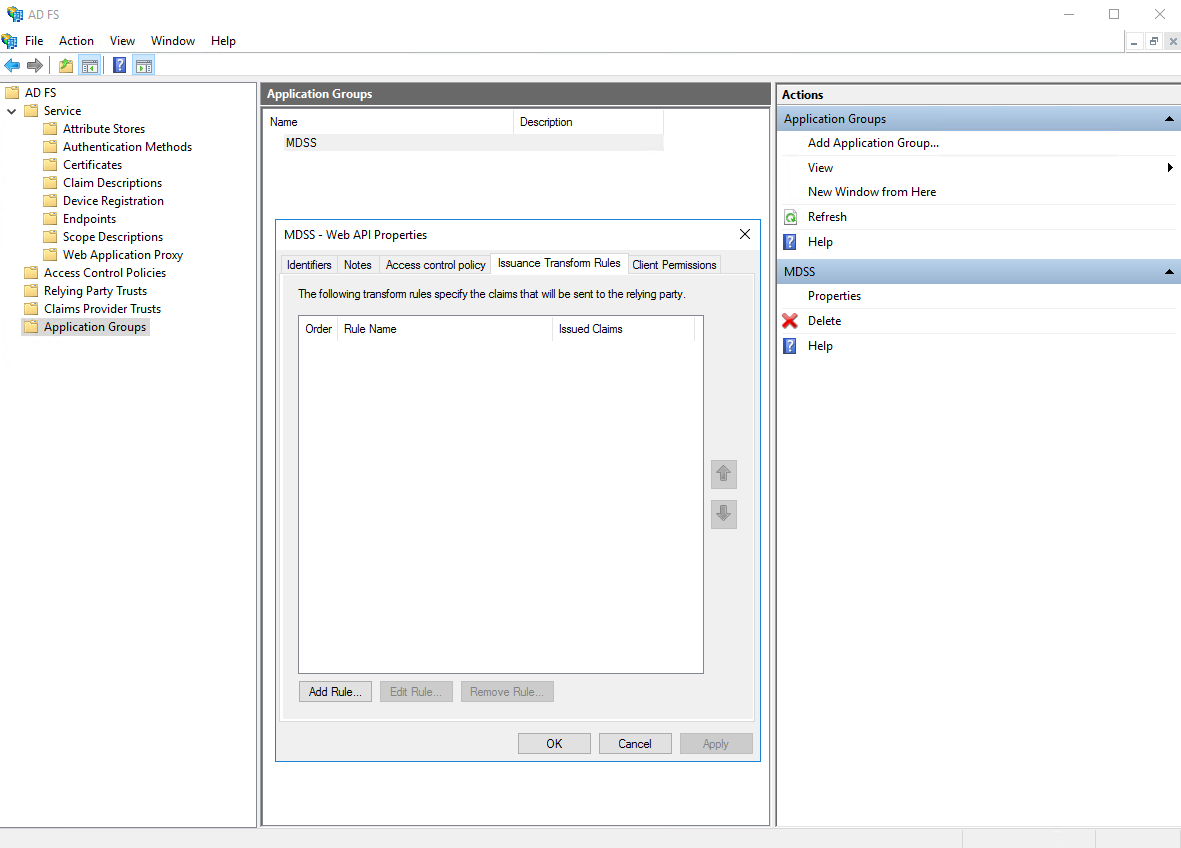
- Select "Send LDAP Attributes as Claims" as the Claim Rule Template
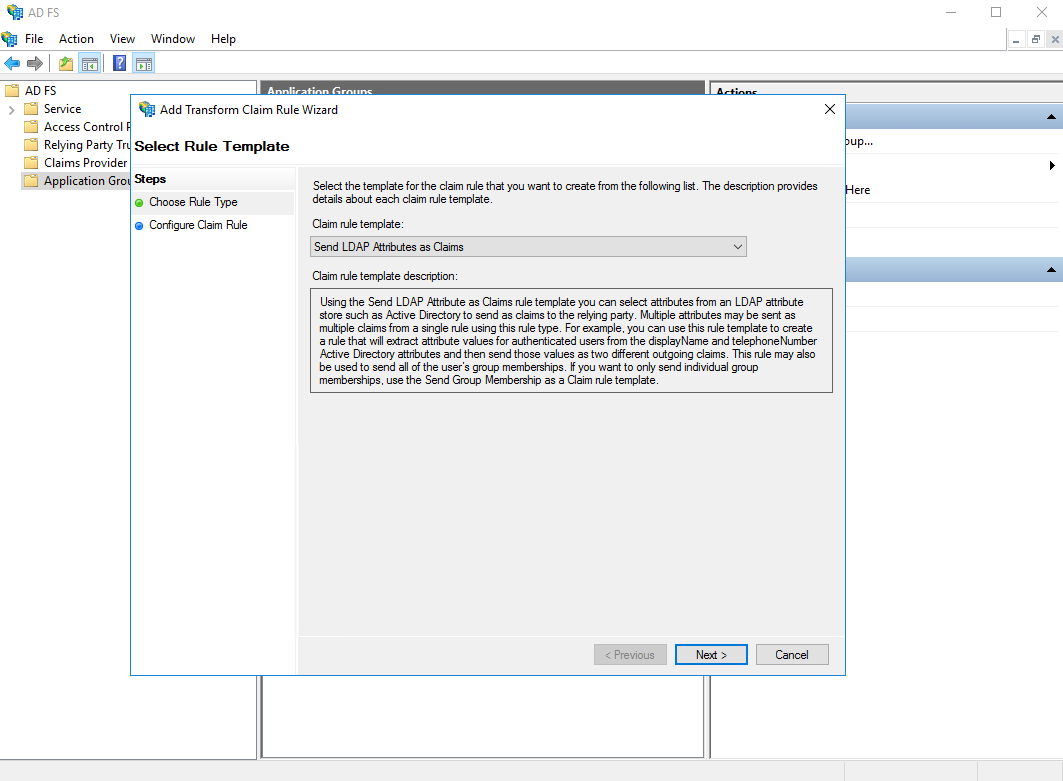
- Give the rule a name, select Active Directory as the attribute store and configure the following:
- E-Mail Address as E-mail Address
- Is-Member-Of-DL as " groups"
- Display-Name as "user_display_name"
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
Was this page helpful?
Next to read:
Okta Specific ConfigurationDiscard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message

