Integrate with Microsoft Azure Active Directory
Below you can find a step by step tutorial on how to integrate Microsoft Azure Active Directory with MetaDefender Vault using the OpenID Connect protocol.
Prerequisites: An Azure Active Directory Tenant (quick guide: https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-create-new-tenant)
Note: AD Credentials used in this example are blurred for security purposes
- Sign into Microsoft Azure Active Directory and navigate to admin dashboard
- Go to App registrations and select New registration

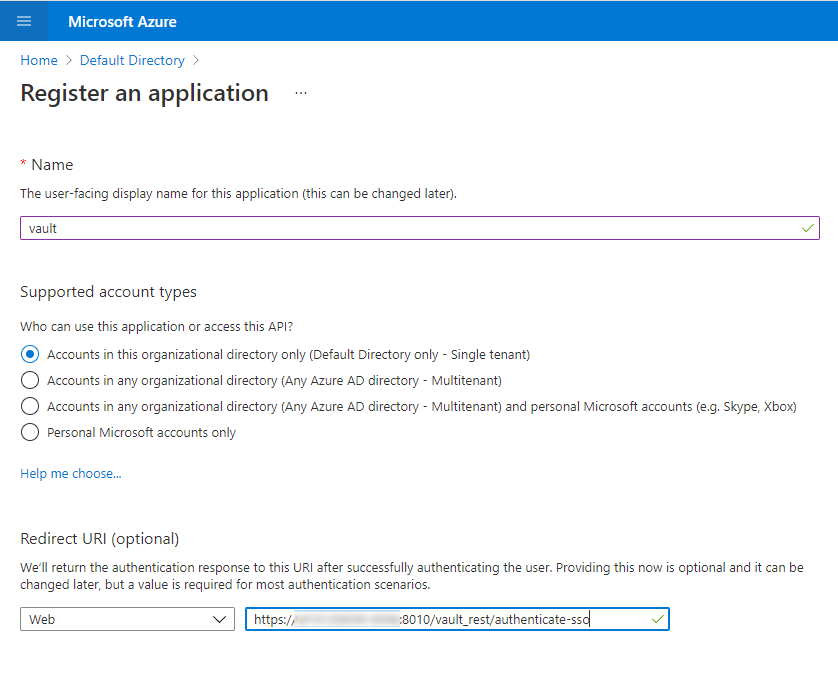
- Let’s configure the application settings.
- Give the application a name like for example “Vault App”.
- Configure the Redirect URL (https://host:port/vault_rest/authenticate-sso) - this can also be found in Metadefender Vault → Settings → Single Sign-On after you fill in IP Address Or Domain
- Note: Azure AD supports only HTTPS protocol for redirect URI
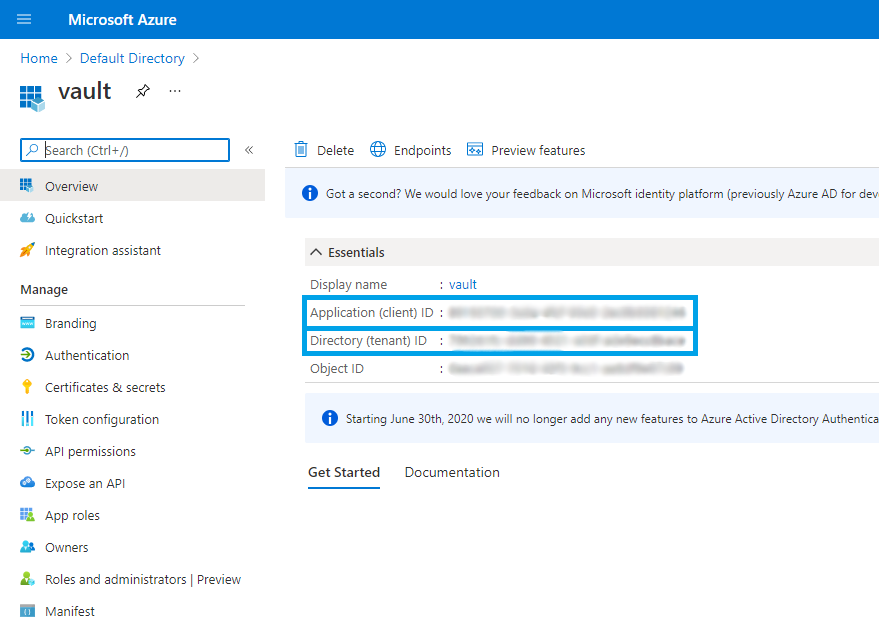
- Record Application (client) ID and Directory (tenant) ID
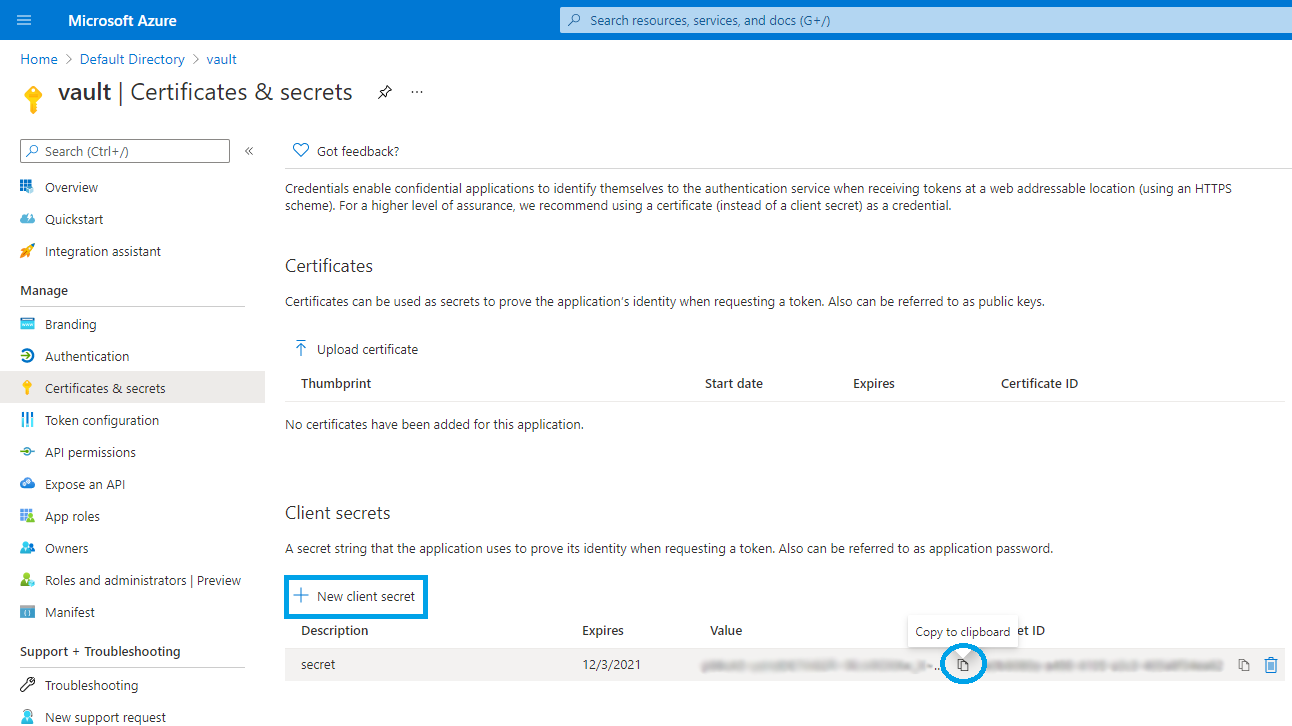
- Go to Certificates & Secrets and generate a new client secret string (also referred to as an application password). Record the client secret.
Note that you won’t be able to retrieve it at a later time because it will be hidden. You will need to generate a new secret in this case.
- Let’s configure Metadefender Vault SSO settings using the information collected above
- Go to MetaDefender Vault web console and navigate to Settings → Single Sign-On
- Turn on Enable Single Sign-On
- Don’t turn on Ignore Certificate Issues as Azure AD will provide a trusted certificate
-
Turn on Load User Profile such that MetaDefender Vault can acquire the following claims:
- name
- preferred_username
- given_name
- family_name
- Authority should point to your Microsoft Azure AD URL. You can find this URL in the Azure AD dashboard under your application endpoints. The format is:
- IP Address or Domain should point to the location of your Vault instance. Once you fill this information, Vault will automatically generate the Redirect URI
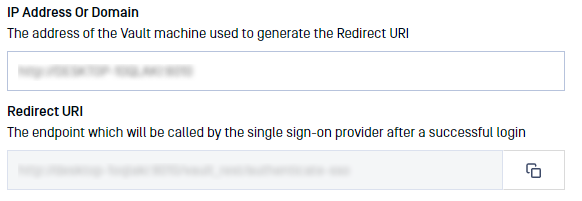
- This Redirect URI should be used in Azure AD Application Settings (step 3)
- Copy the Application (client) ID (step 4) and Client secret (step 5) so we can enter them in MetaDefender Vault SSO configuration.
- Administrator Emails: if some of the Microsoft Azure AD users should have administrative rights in Vault, please enter a list of emails in this field. MetaDefender Vault will compare the email of users that login from Microsoft Azure AD against the provided list to determine if a user should be an administrator
- You don’t need to specify additional integration scopes
- Microsoft Azure AD requires some additional endpoints:
- Review final configuration
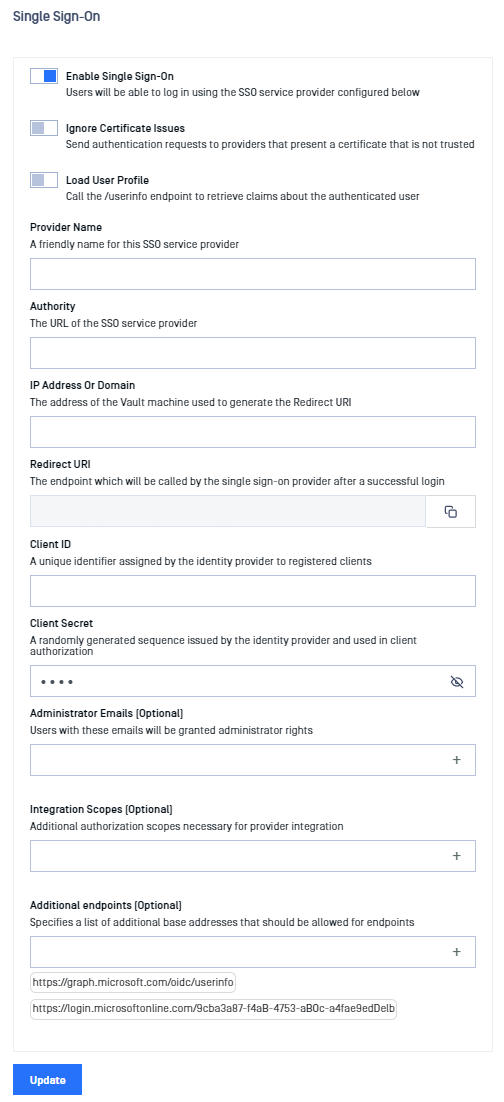
- If everything is ready, click Update.
Testing the integration
To test the integration:
- Log out of MetaDefender Vault
- You will notice that there is a new LOGIN WITH SSO button on the login page
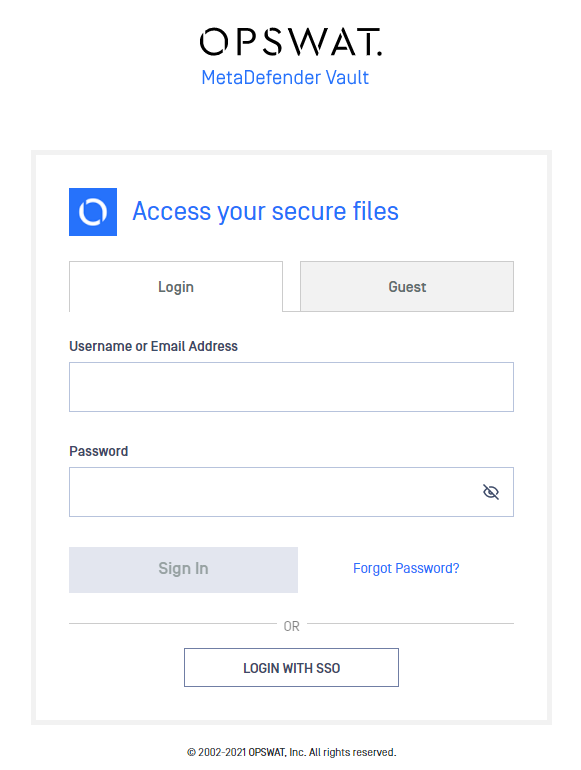
- Click LOGIN WITH SSO. You should be redirected to Microsoft Azure AD to login. Once logged in, you will be redirected back to MetaDefender Vault and automatically logged in.

