Title
Create new category
Edit page index title
Edit category
Edit link
Version 5.7.3
| Release date | Scope |
|---|---|
| July 10th, 2024 | MetaDefender Email Gateway Security 5.7.3 focuses on minor new features, improvements and bug fixes. |
New & improved
Add to trusted senders from Quarantine
Email Gateway Security now supports administrators to add the sender of an email to the Settings > Trusted senders list directly from the Email information view of Audit > Quarantine.
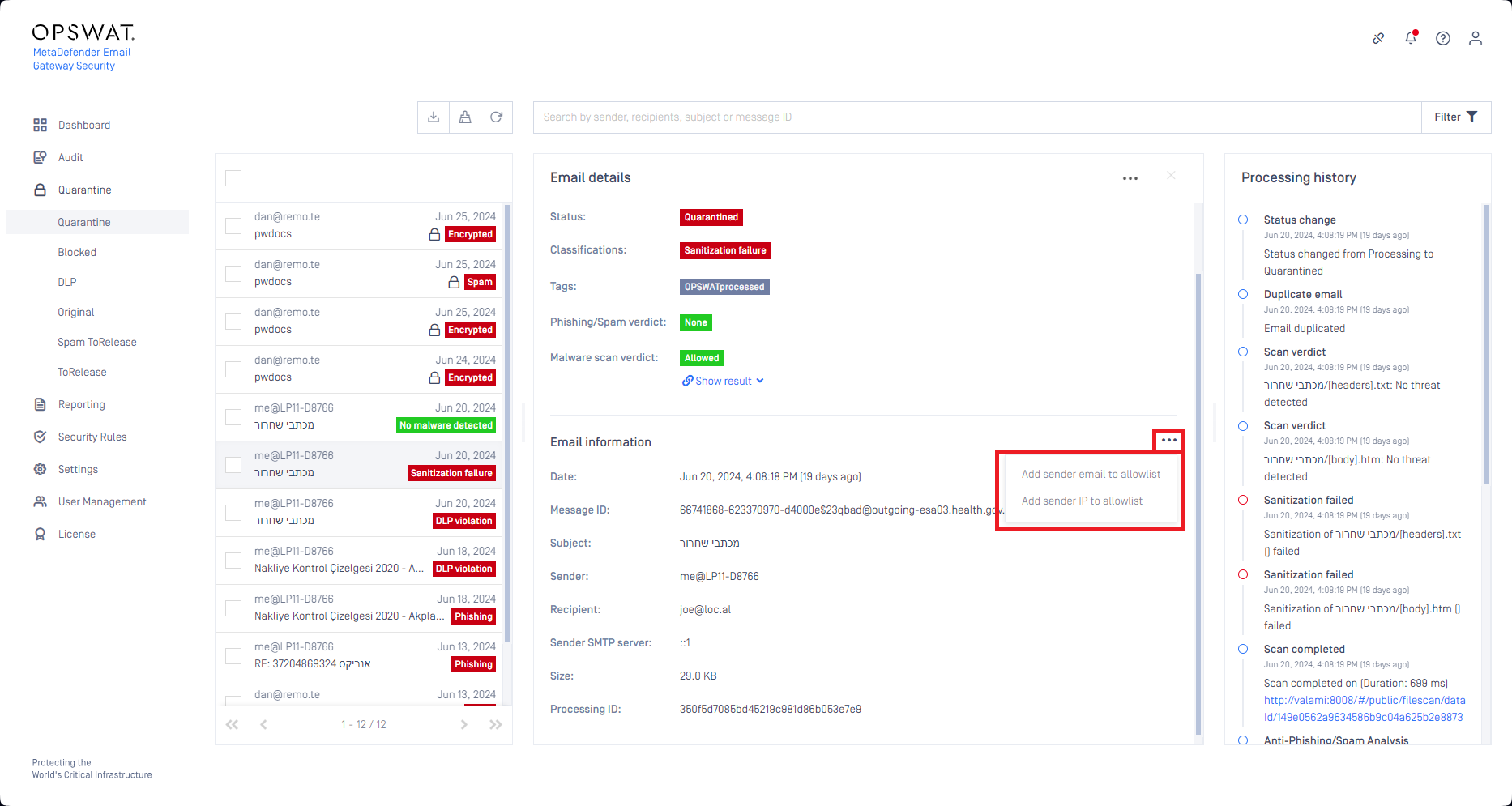
For details see Quarantine and Trusted senders.
Non-Delivery Reports (NDRs)
Email Gateway Security now supports non-delivery reports when it is unable to deliver emails -due to SMTP permanent failures of the receiving SMTP relay- according to the section 6.1. Reliable Delivery and Replies by Email of RFC 5321.
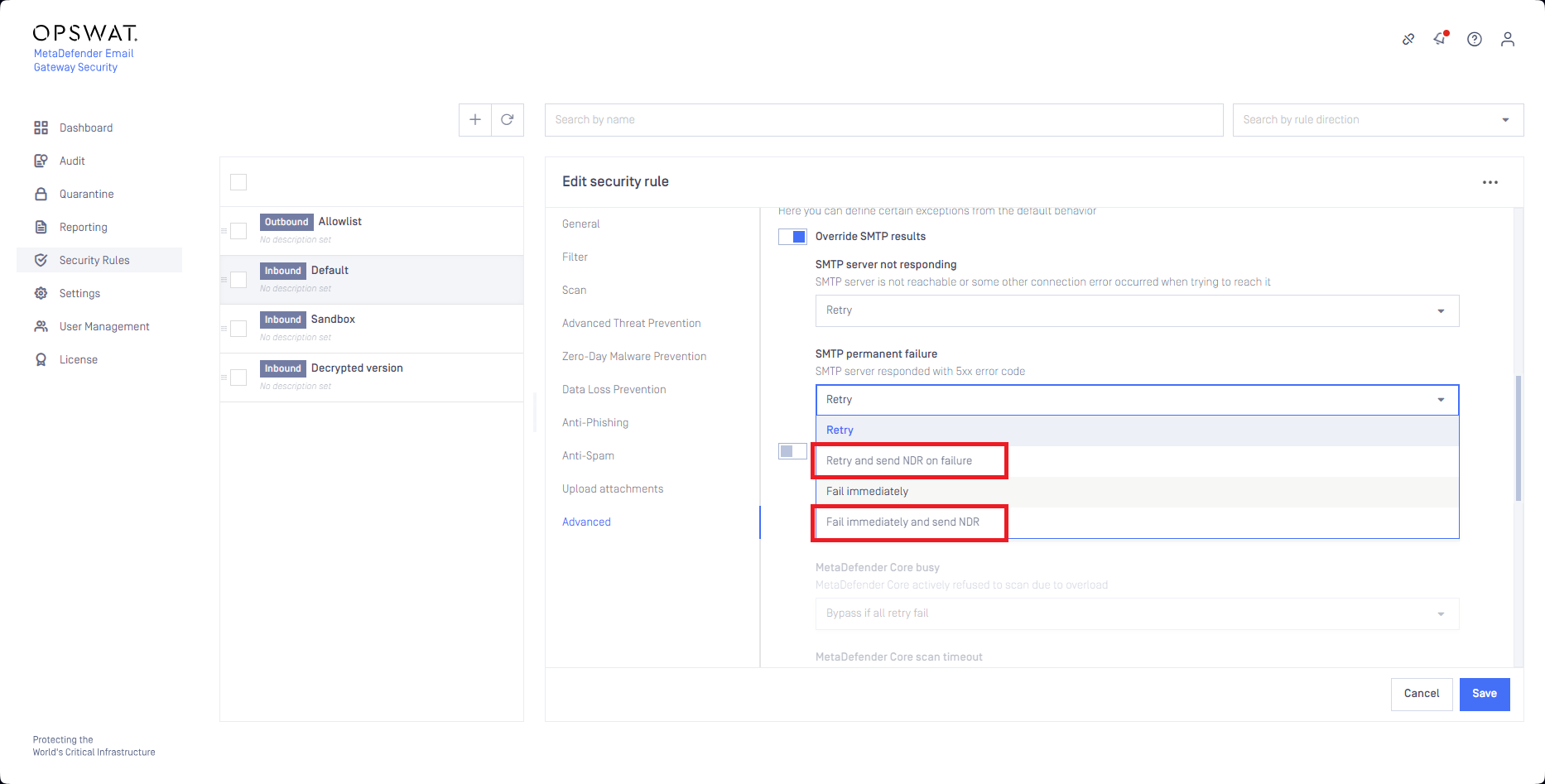
For details see the Advanced section in Policy.
ESMTP Chunking (BDAT) support
Email Gateway Security's SMTP server from now on supports the SMTP data chunking as defined by the RFC 3030. Using the chunking, SMTP clients can send large amounts of data to Email Gateway Security in smaller chunks.
For details see the enable_chunking_support entry in Registry configuration.
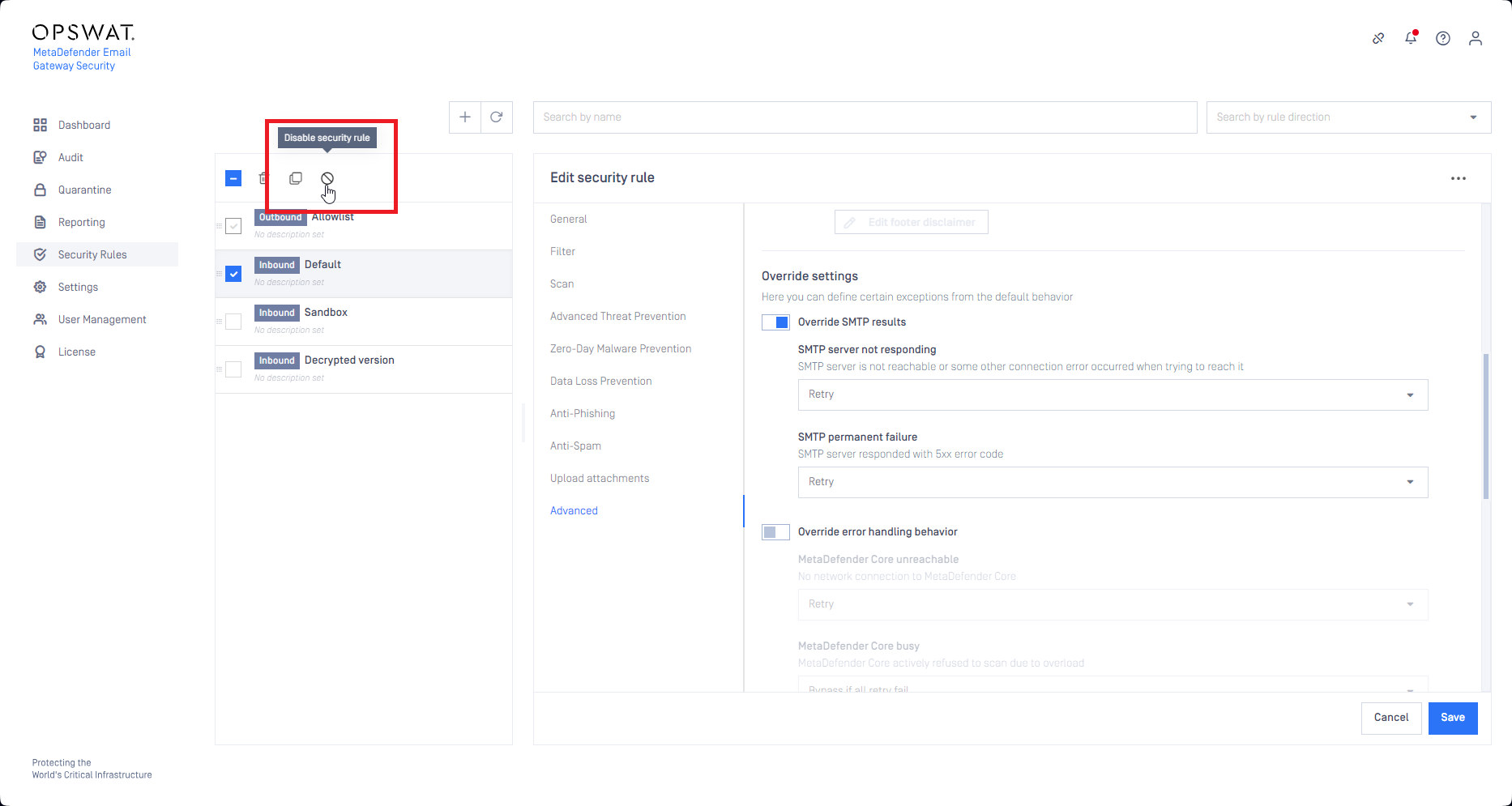
Disable security rules
Email Gateway Security now supports disabling security rules. When a security rule is disabled, it won't match and process any emails.
Anti-malware rescan action
Email Gateway Security has introduced a new rescan action: anti-malware rescan. This action skips anti-spam checks making it an ideal action for spam false positive rescans.
For details see Handling spam false positives and Supported functions.
Other
Improved Core scanning performance
Email Gateway Security now utilizes the size=1 parameter of the GET /file MetaDefender Core API call to improve the Core performance.
Prioritize HTML header charset
Prioritizing the HTML header charset is now supported as a GUI option.
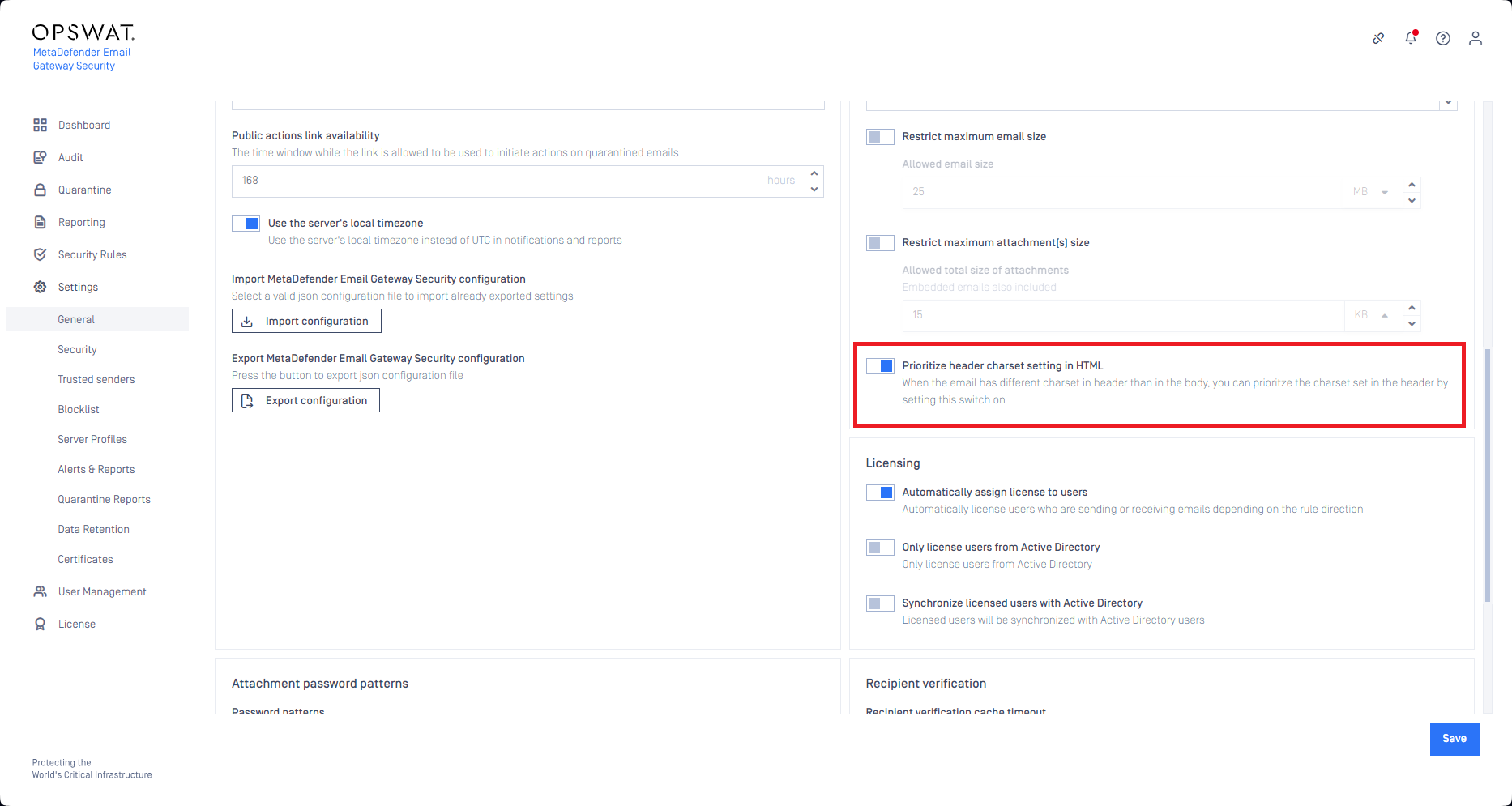
For details see the html_prioritize_header_charset entry in Registry configuration.
Bug fixes
Logging encrypted attachment rescans
The events of receiving the email, rule selection and scan results were not logged for emails that were rescanned due to encrypted attachments.
SPF verification failures
SPF verification had a conversion defect on certain servers with non-English operating system.
In certain cases Email Gateway Security took the domain of the HELO/EHLO command for SPF verification instead of the domain of the MAIL command not being able to properly check SPF records in these cases.
MX lookup stopped
The MX record lookup functionality had an architectural issue that caused the function to slow down with time, in certain cases even to stop functioning.
SMTP watchdog failed over TLS
Email Gateway Security's SMTP server watchdog always attempted the FQDN localhost to connect to its local SMTP server . When the SMTP server had TLS enabled and localhost was not among the subject alternative names, the watchdog was unable to verify the SMTP server's certificate and the connection failed. This caused false alarms and unnecessary restarts of the SMTP server.
In this version it became configurable what FQDN the watchdog should use to attempt to connect to the SMTP server.
For details see the monitor_server_name entry under the smtp_config key in Registry configuration.

