Title
Create new category
Edit page index title
Edit category
Edit link
Version 5.5.0
| Release date | Scope |
|---|---|
| Dcember 13th, 2021 | MetaDefender Email Gateway Security 5.5.0 is a feature release focusing on the new GUI. |
New & improved
Redesigned GUI & Dashboard
Email Gateway Security has got a new graphical user interface and a better focused Dashboard.
For details see Dashboard.
PGP encrypted attachments
Attachments with OpenPGP symmetric encryption can be rescanned on the public rescan page just like password protected zip files, Microsoft Office documents and pdf documents.
For details see Password protected attachments.
Redaction in email headers
Redacting sensitive data is now supported in email headers that are displayed by email clients.
The supported headers are:
- From (sender),
- To (recipient(s)),
- Cc (carbon copy recipient(s)),
- Bcc (blind carbon copy recipient(s)),
- Subject.
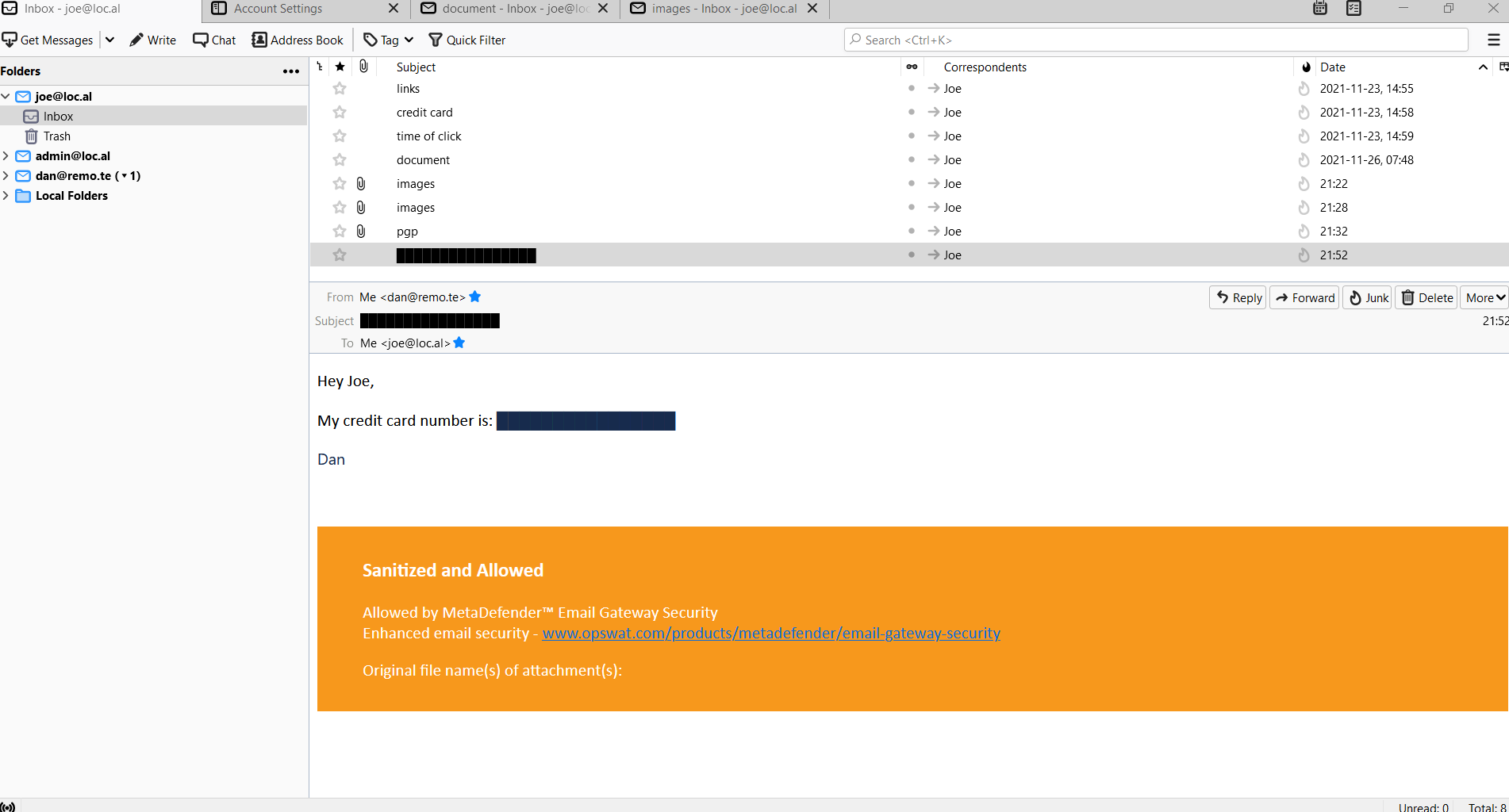
Encrypt quarantine downloads
Emails downloaded from the quarantine are saved as zip archive files (even if there is only one email downloaded). These archives can now be encrypted using a password at the time of downloading.
For details see Operations.
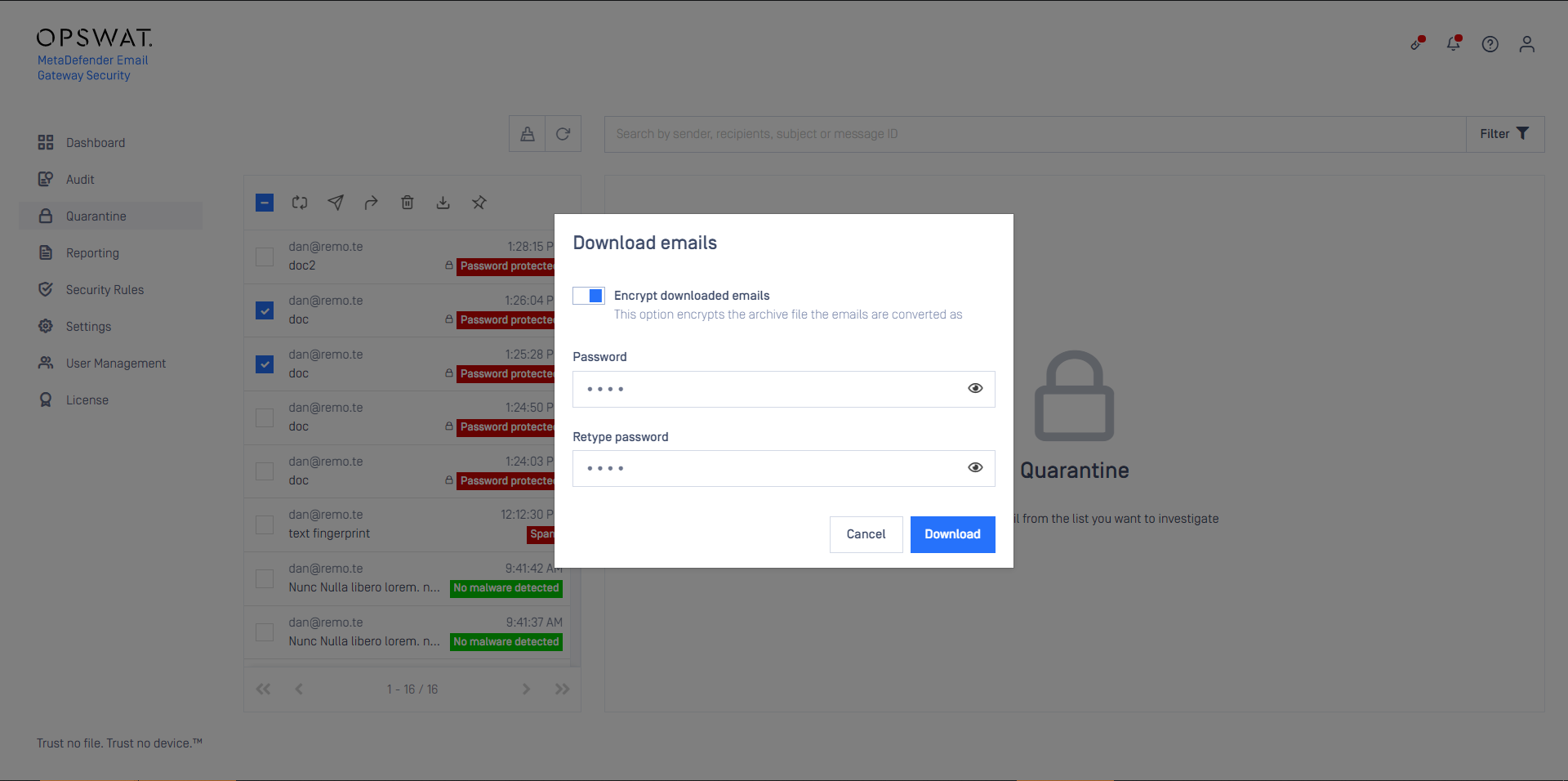
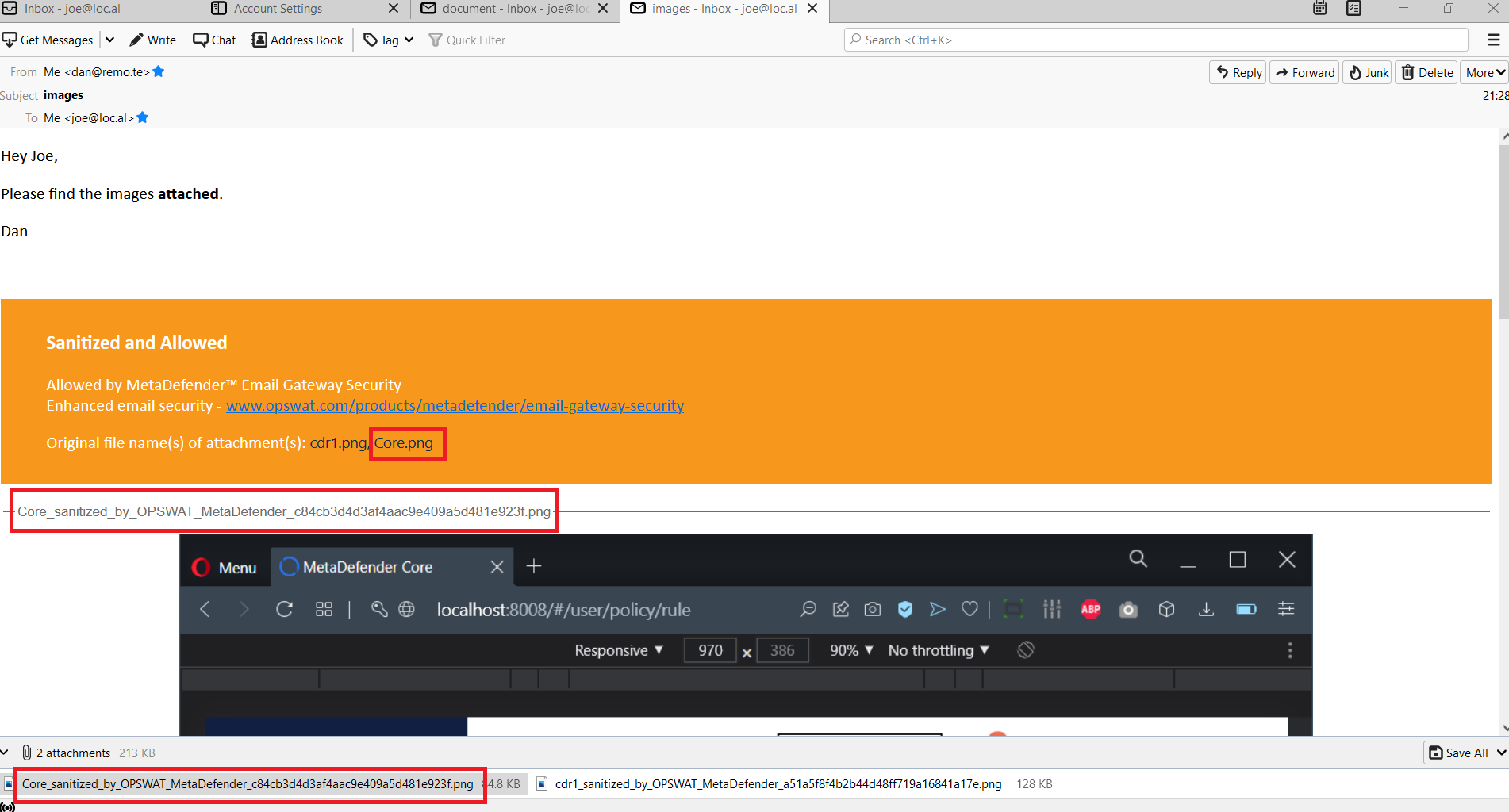
Original attachment file names
A new disclaimer variable is supported now that can list the original file names of the attachments, even if the attachment file name was changed by the Deep CDR or Proactive DLP processing.
For details see Generally available variables.
Webhook callback log entries
Email Gateway Security is now much more verbose in the logs about MetaDefender Core webhook callbacks.
For details see MetaDefender Core server webhook callbacks.
Changed
Email body CDR conversion
By the standards, the allowed file format of email bodies can be:
- plain text,
- Hypertext Markup Language (HTML) or
- Rich Text Format (RTF).
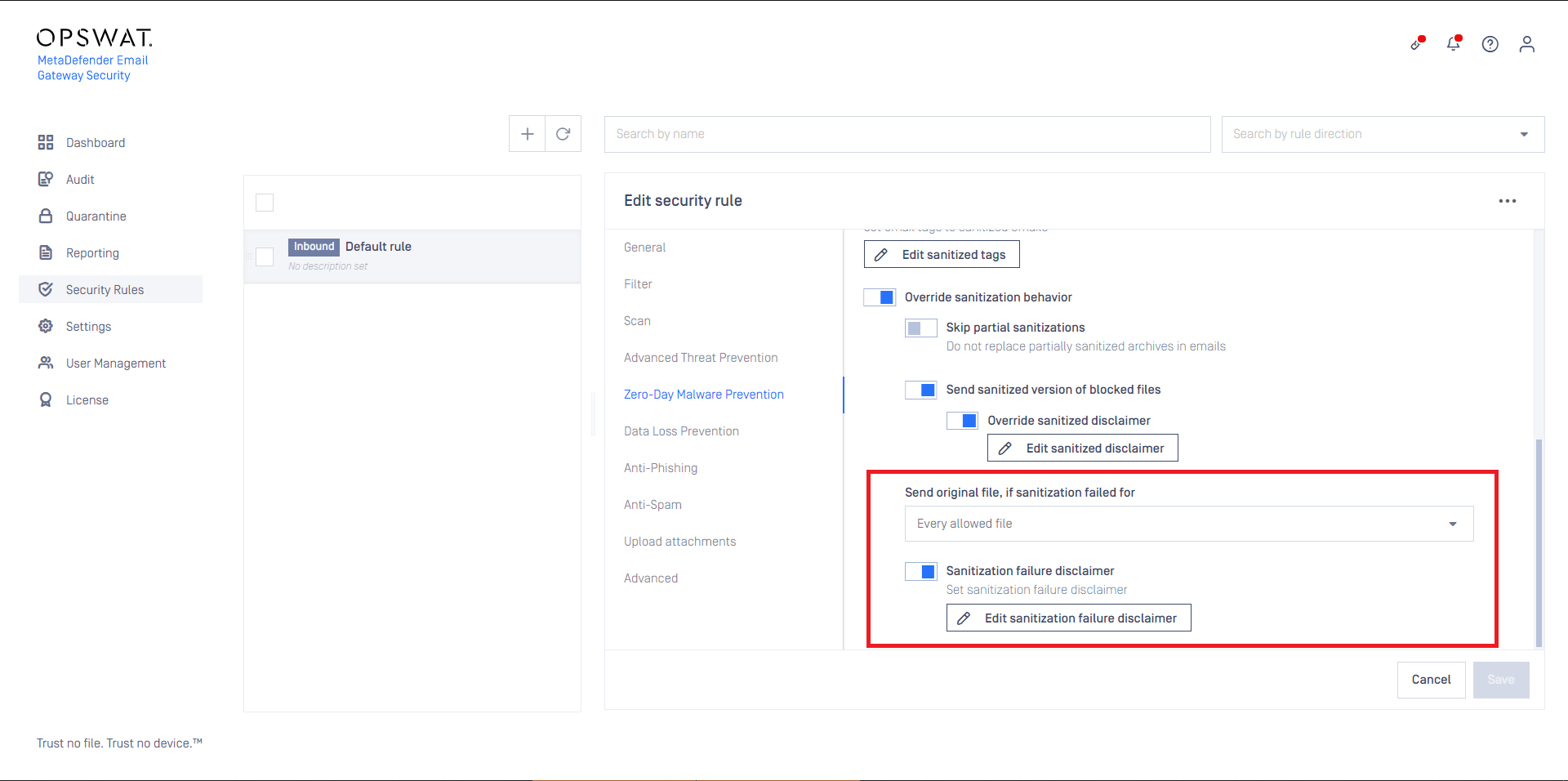
CDR in Email Gateway Security may be configured to convert text, HTML and RTF to a file format that is not supported as an email body (for example PDF). In such a case the resulted file of the CDR processing can not be used as the email body.
In case of such a CDR configuration, previous versions (5.4.2 or earlier) of Email Gateway Security fall back to the original, unprocessed version of the email body.
Email Gateway Security version 5.5.0 will handle such CDR configurations as sanitization failure and handle the email body according to the sanitization failure settings.
For details see Zero-Day Malware Prevention.
Phishing not marked as spam
In previous versions (up to version 5.4.2), emails classified as phishing were always classified as spam, too.
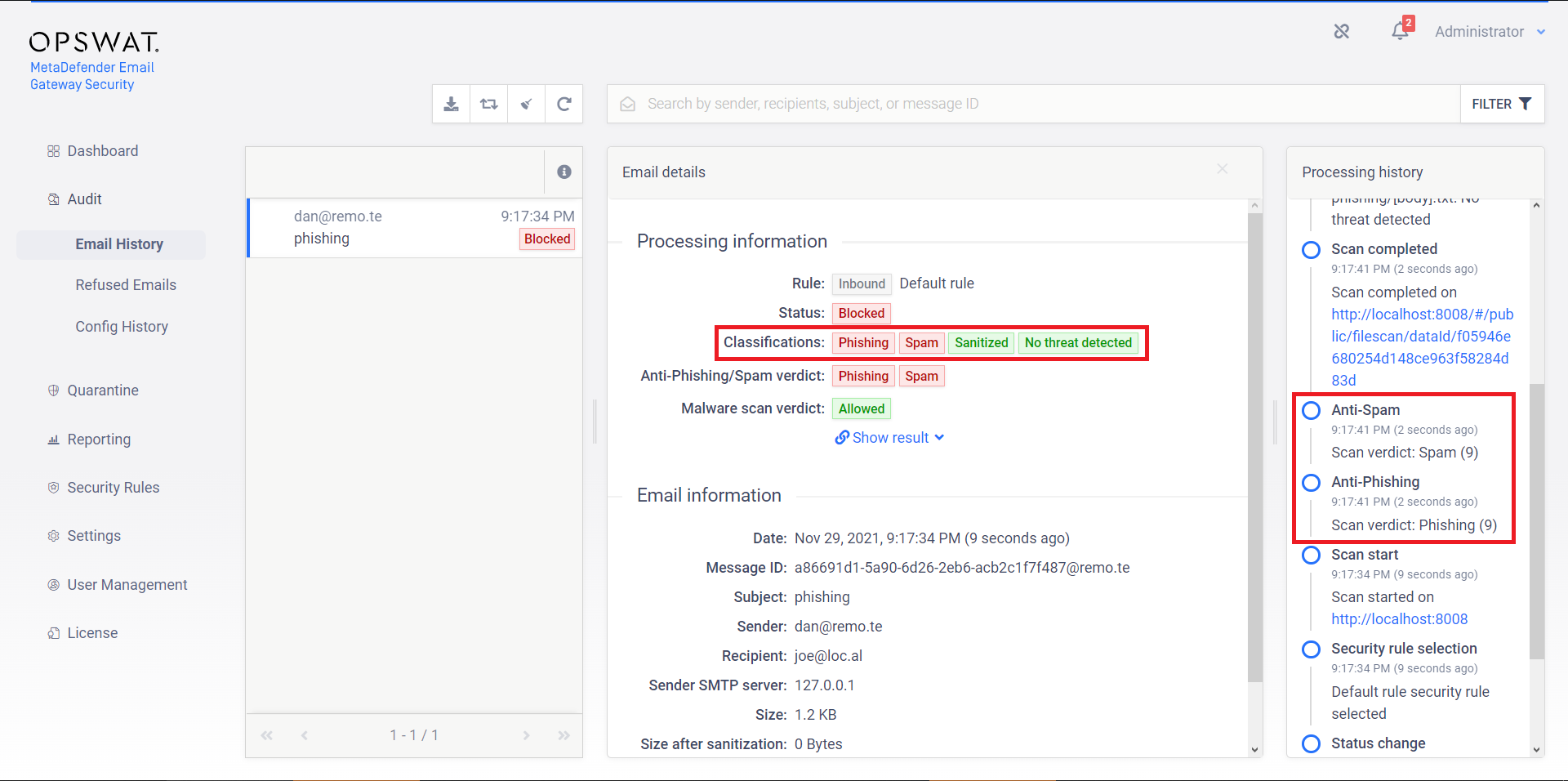
Email Gateway Security 5.4.2 phishing (and spam) classification
From version 5.5.0, if an email is classified as phishing, then it won't be classified as spam any more.
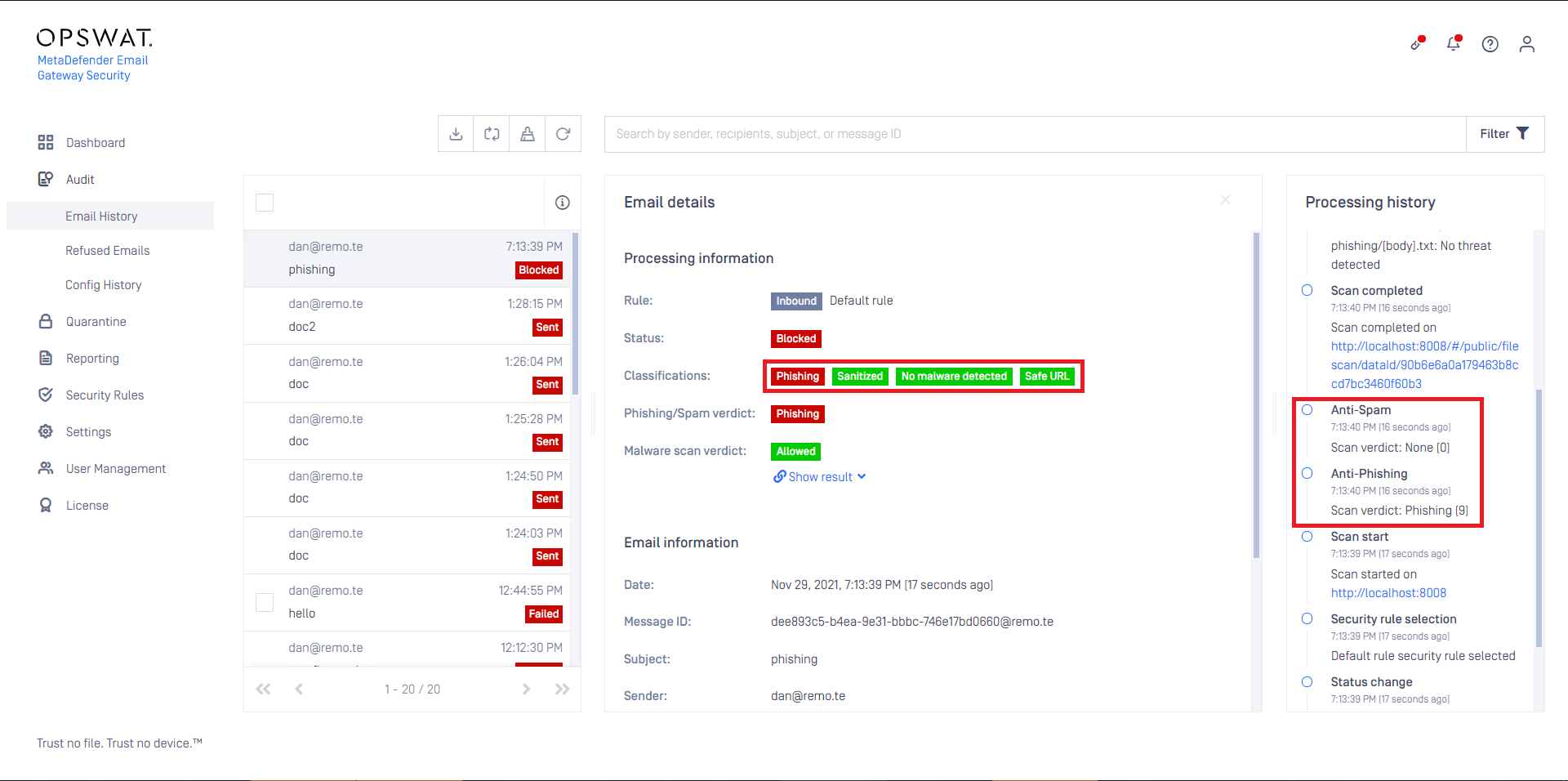
Email Gateway Security 5.5.0 phishing classification
Fixed
Modify failed on complex email
Email modification task failed in case of certain, complex emails (tens of attachments and nested emails and huge size, etc.).
The reason was that the processing of the email exceeded the email processing task's timeout. This timeout is now configurable using the processing_task_timeout Registry value.
For details see Registry configuration.

