Title
Create new category
Edit page index title
Edit category
Edit link
Version 5.6.0
| Release date | Scope |
|---|---|
| April 19th, 2022 | MetaDefender Email Gateway Security 5.6.0 focuses on improved integration to MetaDefender Vault; more user friendly email disclaimers and translation support. |
New & improved
Improved usability of MetaDefender Vault integration
From Email Gateway Security v5.6.0 and MetaDefender Vault v3.0.4 the two products can be integrated so that Vault can be used:
- as a secure attachment storage
- to offload attachment processing
- and much more.
The usability of the integration of the two products have been improved to a level where it is completely transparent to email recipients, who do not need to know about the underlying MetaDefender Vault.
Disclaimers in emails are more clear and compact.
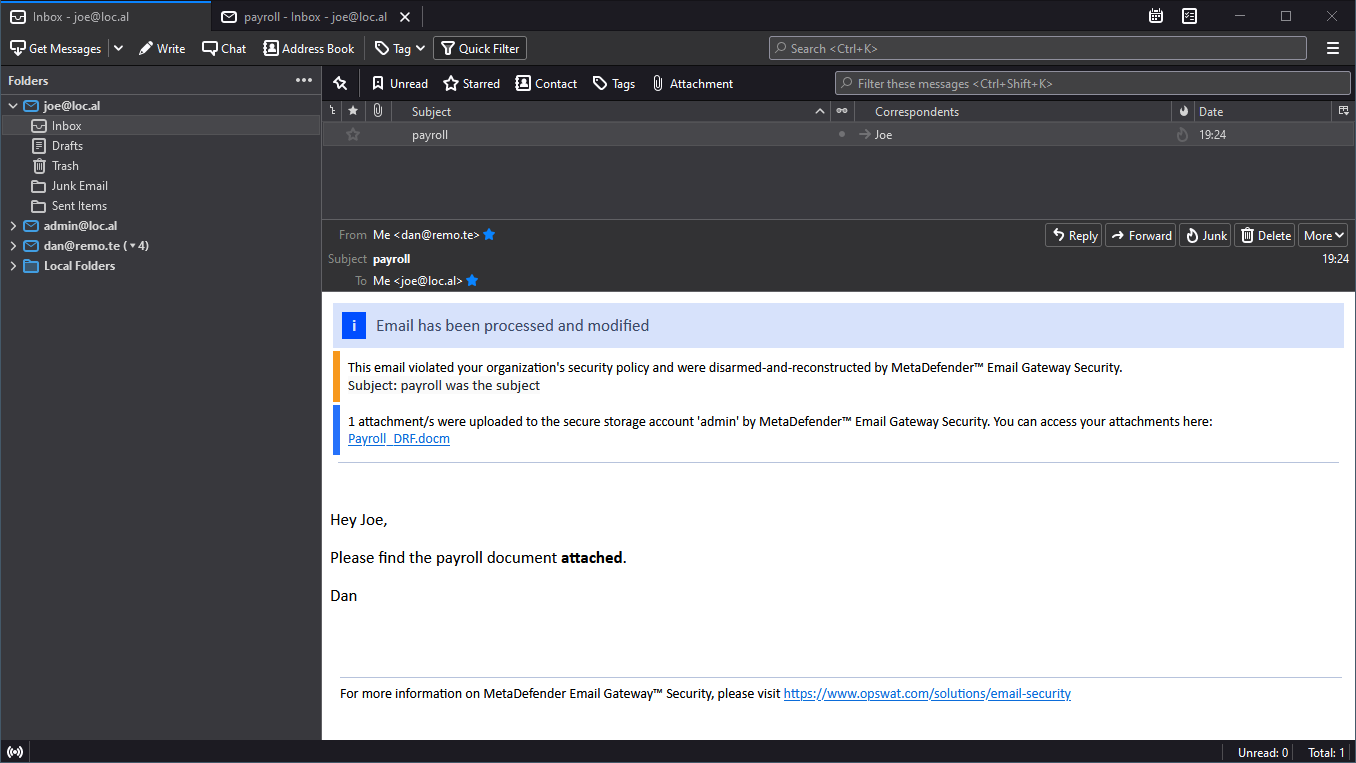
Also, there are new Dashboard widgets showing the upload statistics.
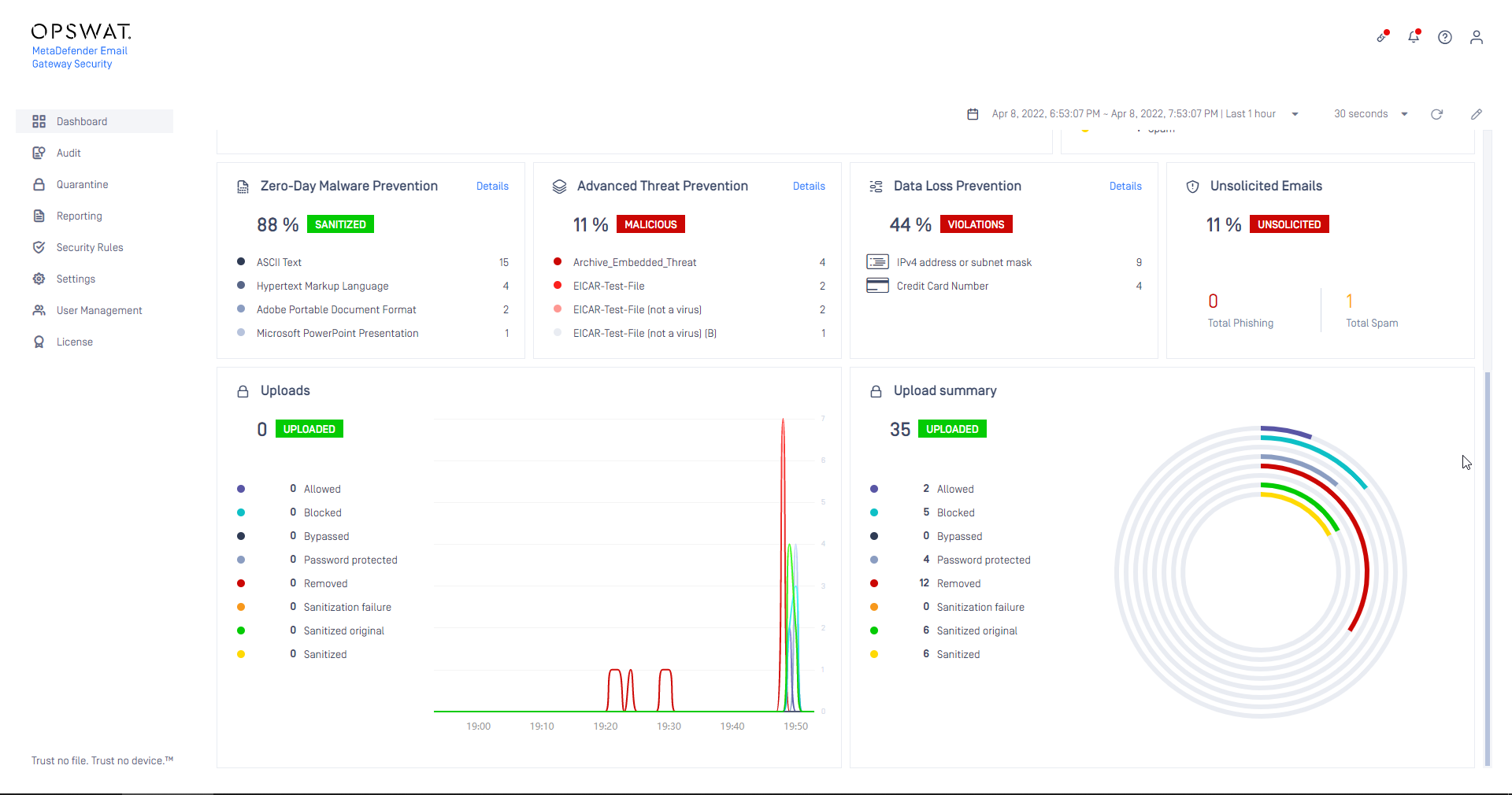
For details see Integration with MetaDefender Vault, Upload attachments and Disclaimers.
Dynamic anti-phishing won't trigger on mailto links
Dynamic Anti-phishing won't apply to mailto: links. This way email address links stay usable inside email bodies even when Dynamic Anti-phishing is otherwise in use.
Force rescan in case of useless hash lookup verdicts
Email Gateway Security will force a scan in case when hash lookup is applicable for an email component but the hash lookup result is any of the following:
FailedNot ScannedCancelledIn Progress
The results above are useless from a recipients perspective, so Email Gateway Security will go for a valid result, and initiate a scan that is expected to end up in a valid result (e.g. clean, infected, etc.).
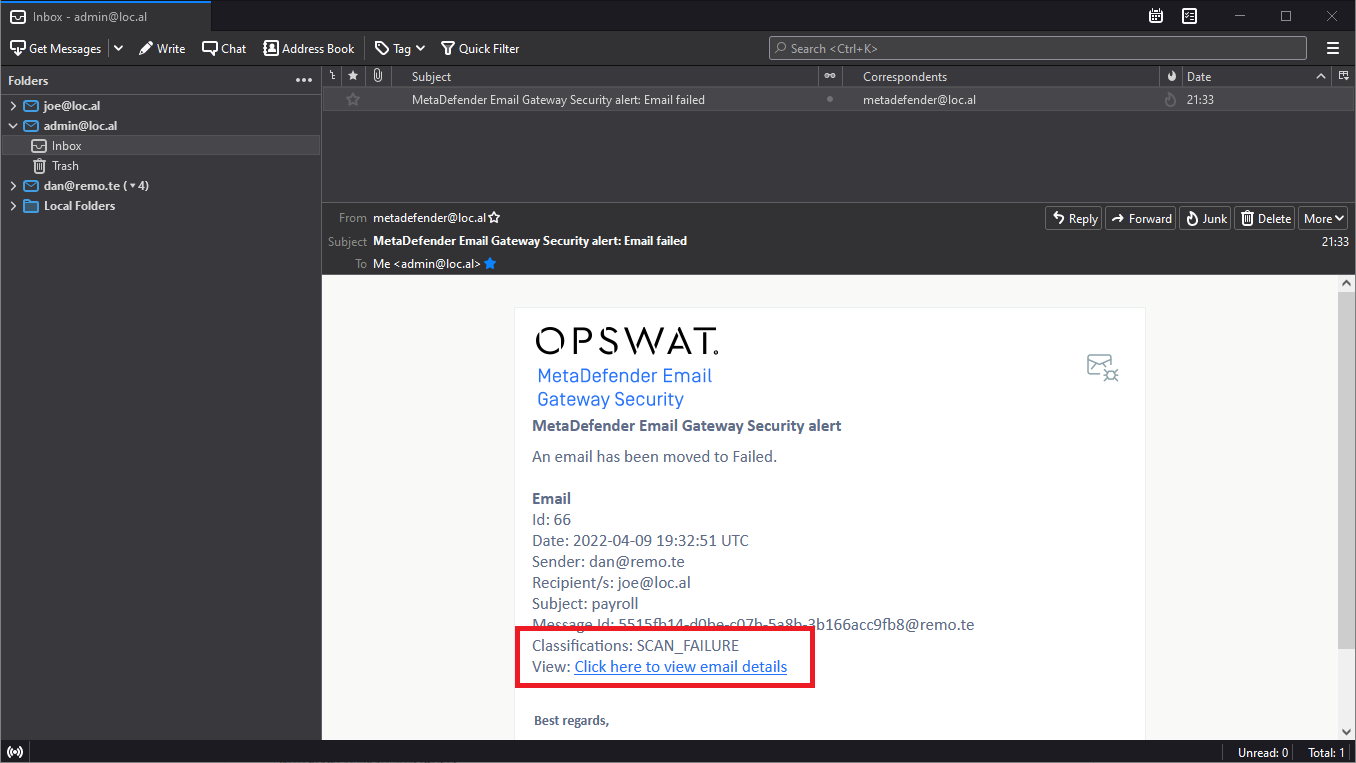
More rich context in failure notification emails
Email Gateway Security may be configured to send an alert email to administrators whenever an email fails to process.
Among other details, these emails contain now the classifications of the failed email, and a direct link to the details of the email under Audit > Email History.
Disclaimer grouping and new default disclaimers
To have a more compact disclaimer experience, disclaimers can now be grouped together so that all disclaimers can be in a single block inside the email.
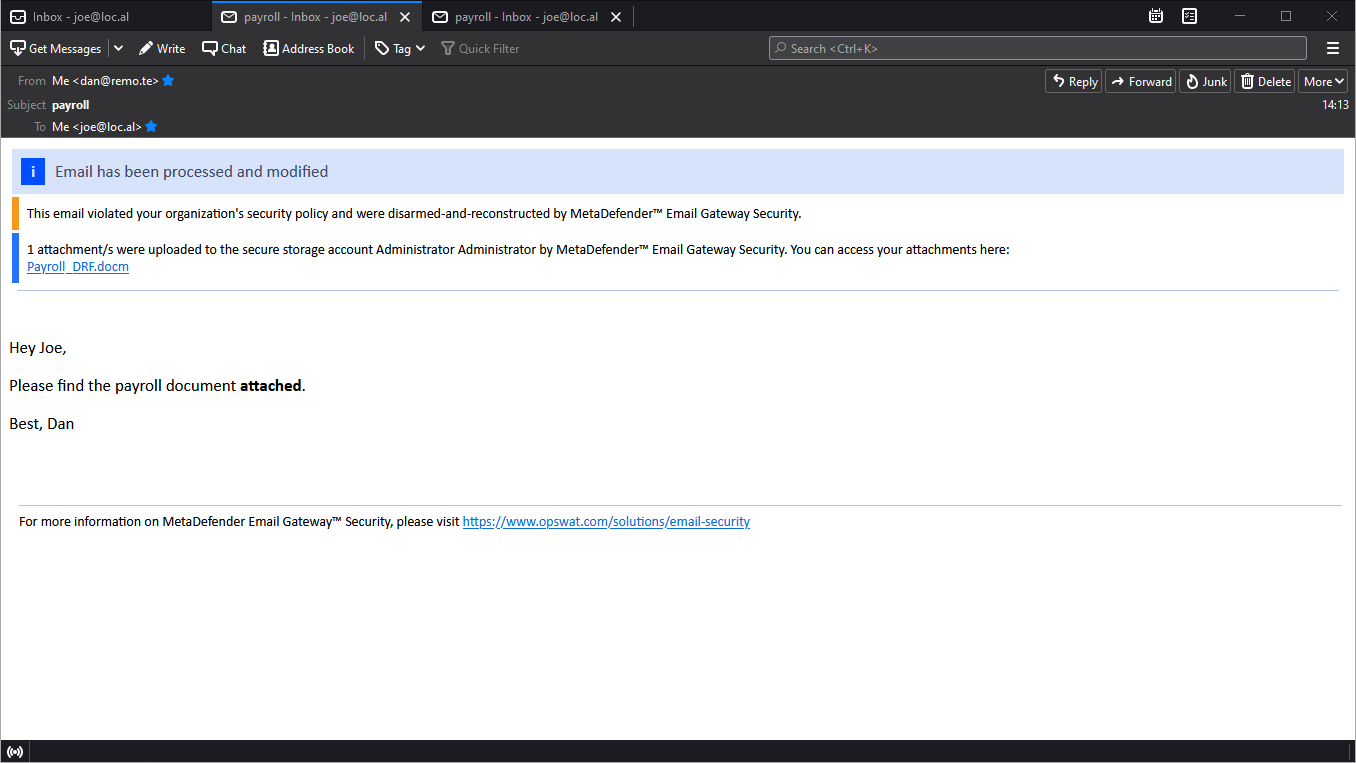
Disclaimers have new default values to support the compact, group layout (default from now) better. Also, new disclaimer variables are available.
On top of all this, Email Gateway Security supports lots of new disclaimer variables especially for regular attachments.
For details see Policy and Disclaimers.
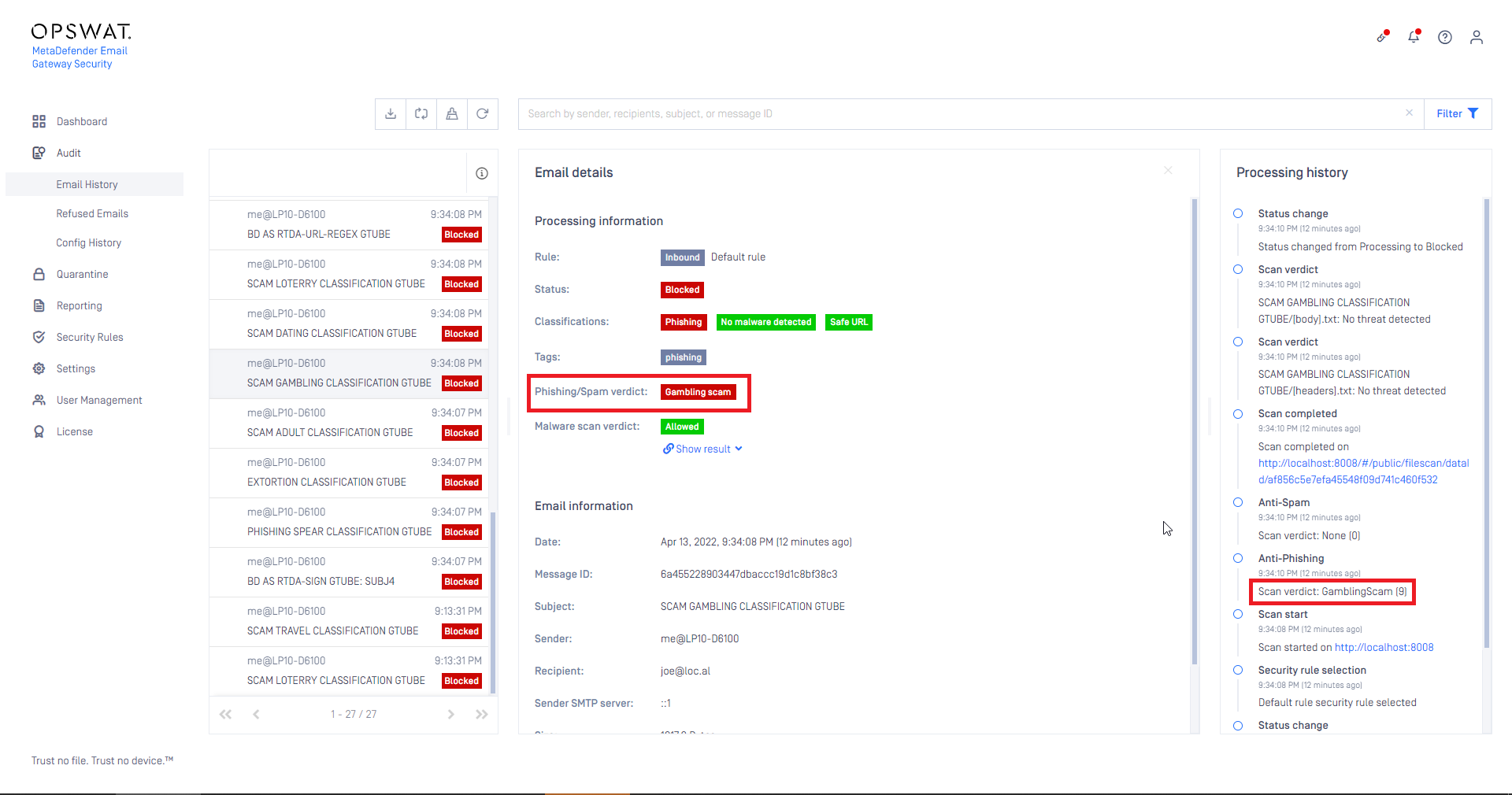
Support for new phishing email sub-categories
To better understand phishing campaigns, Email Gateway Security now supports sub-categorization of certain phishing email types (e.g. spear phishing, scams).
The sub-categories are displayed in the email details and in the processing history.
For details see Phishing subcategories.
Better support to translate the GUI and the notifications
Email Gateway Security now provides easy ways to translate the Web Management Console and the notification, alert and report emails sent by the product.
For details see Translation support.
Changed
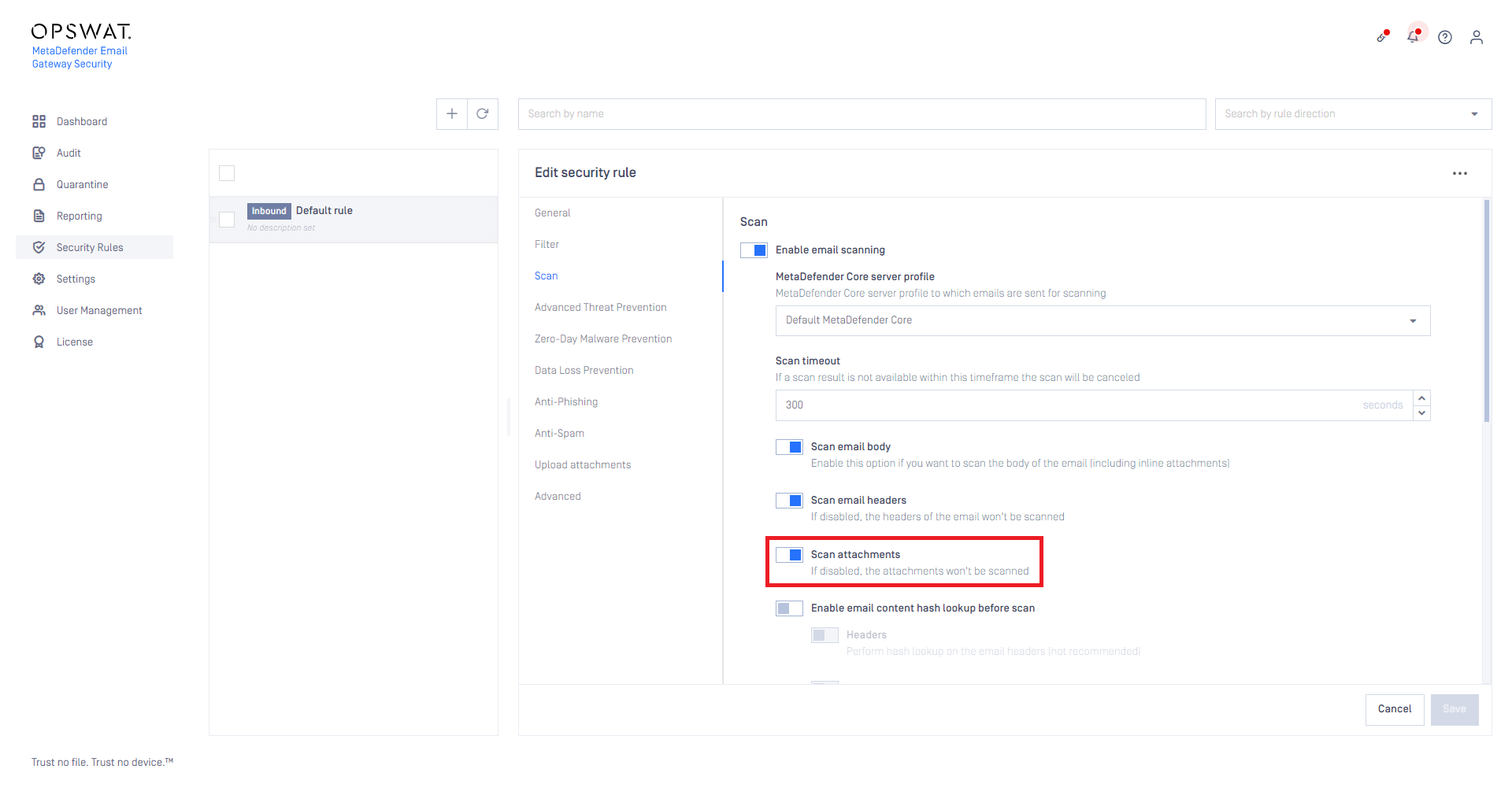
Scanning of attachments can be disabled (offloaded)
In previous version scanning of regular attachments was always on, whenever email scanning was enabled for a security rule in Email Gateway Security.
In version 5.6.0 scanning the attachments can be toggled separately in each security rule.
To maintain backwards compatibility, Scan attachments is on by default for new installations and systems upgraded from previous versions.
One potential use case of this feature is to offload scanning of attachments to MetaDefender Vault. For details see Integration with MetaDefender Vault.
For details about the configuration see Policy.
Disclaimers are grouped by default
For new installations disclaimers are set for the new, grouped layout.
For details see Policy and Disclaimers.
To maintain backwards compatibility, Group disclaimers is off for systems upgraded from previous versions.
Fixed
421 temporary error, please try again later
Undocumented S/MIME encrypted TNEF signature structures caused Email Gateway Security's email parsing workflow to fail to validate the syntax of certain emails. These emails were rejected with the SMTP status ‘421 temporary error, please try again later’ after the SMTP DATA command.
LDAP authentication failed when DN changed
When Web Management Console access was configured to use LDAP and users changed their DN (distinguished name), the login of such users failed with the following log message: Can't cache user. Already exists in DB with different DN attribute.
Typically the DN changes when users change organization units (OU).
Email Gateway Security can now handle DN changes of cached users.
Updated
| Component | Version |
|---|---|
| OpenSSL | 1.1.1n |
| Qt | 6.2.4 LTS |
| Nginx | 1.21.6 |

