| Release date | Scope |
|---|---|
| February 14th, 2022 | MetaDefender Email Gateway Security 5.5.1 is a maintenance release providing minor improvements and fixes. |
New & improved
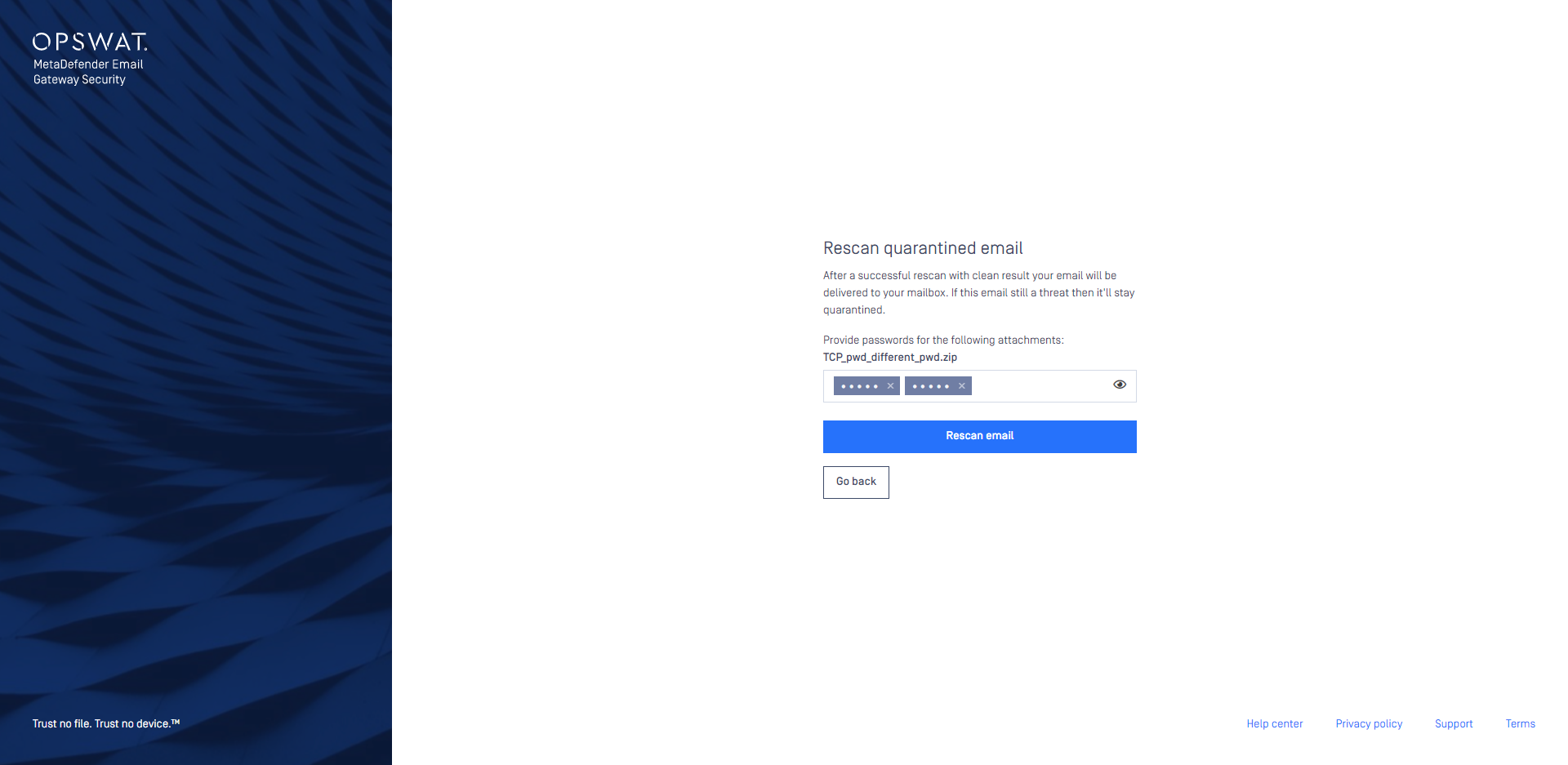
Multi-level password protected attachments
Nested password protected attachments (e.g. password protected pdf in a password protected zip) are now supported both in the rescan page and in the Quarantine rescan function.
For details see Initiate rescan and provide password and Rescan email.
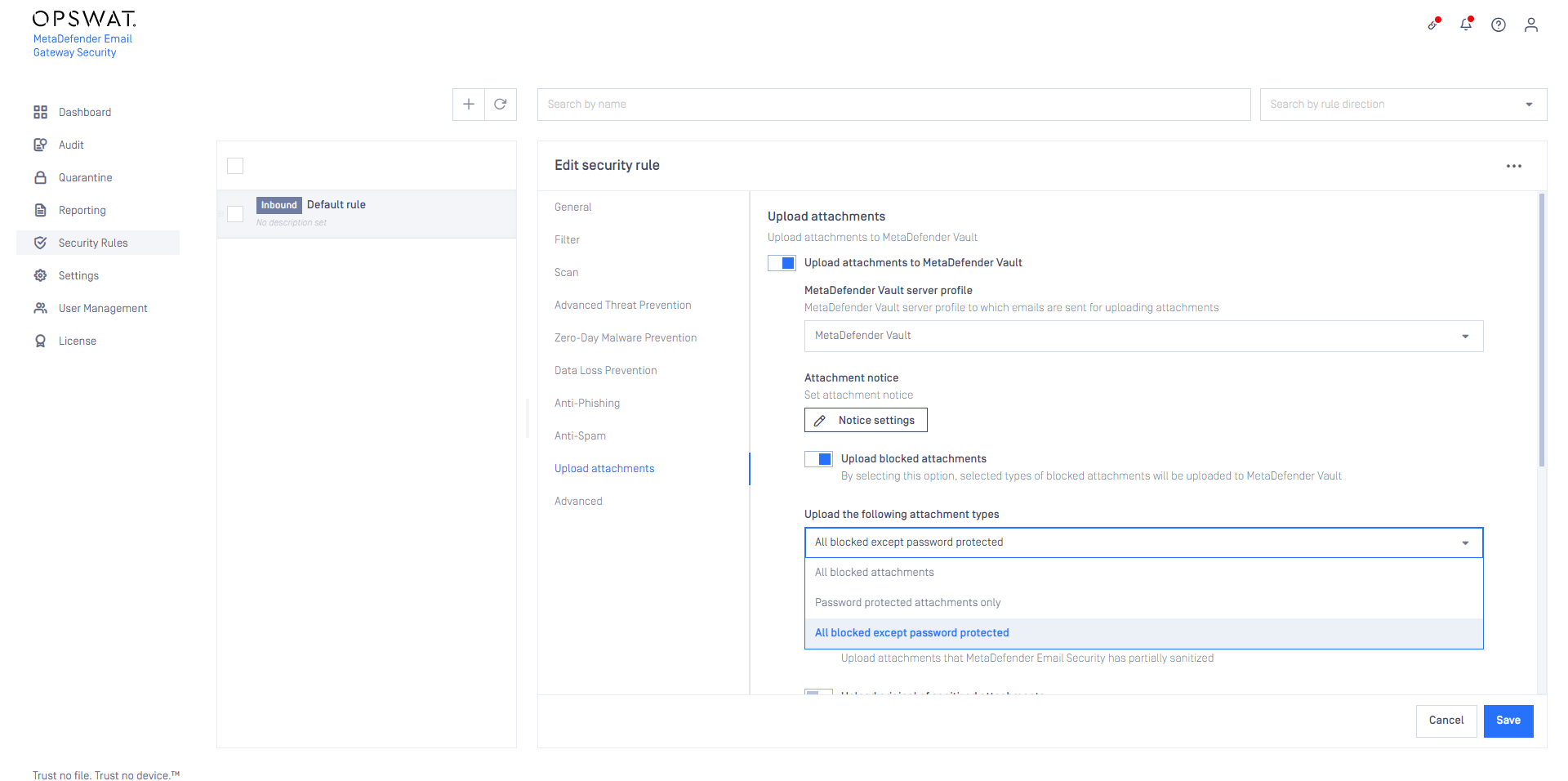
Exclude password protected from uploading
Password protected attachments can now be excluded from MetaDefender Vault upload. This way organizations can enforce users to enter the password and initiate the rescan in Email Gateway Security only.
For details see Upload attachments.
Retry in case of anti-spam engine failure
In the rare case of the failure of the anti-spam engine, Email Gateway Security will retry the spam scan within the timeframe of the timeout.
This way the anti-spam engine failure will impact processing with lower probability.
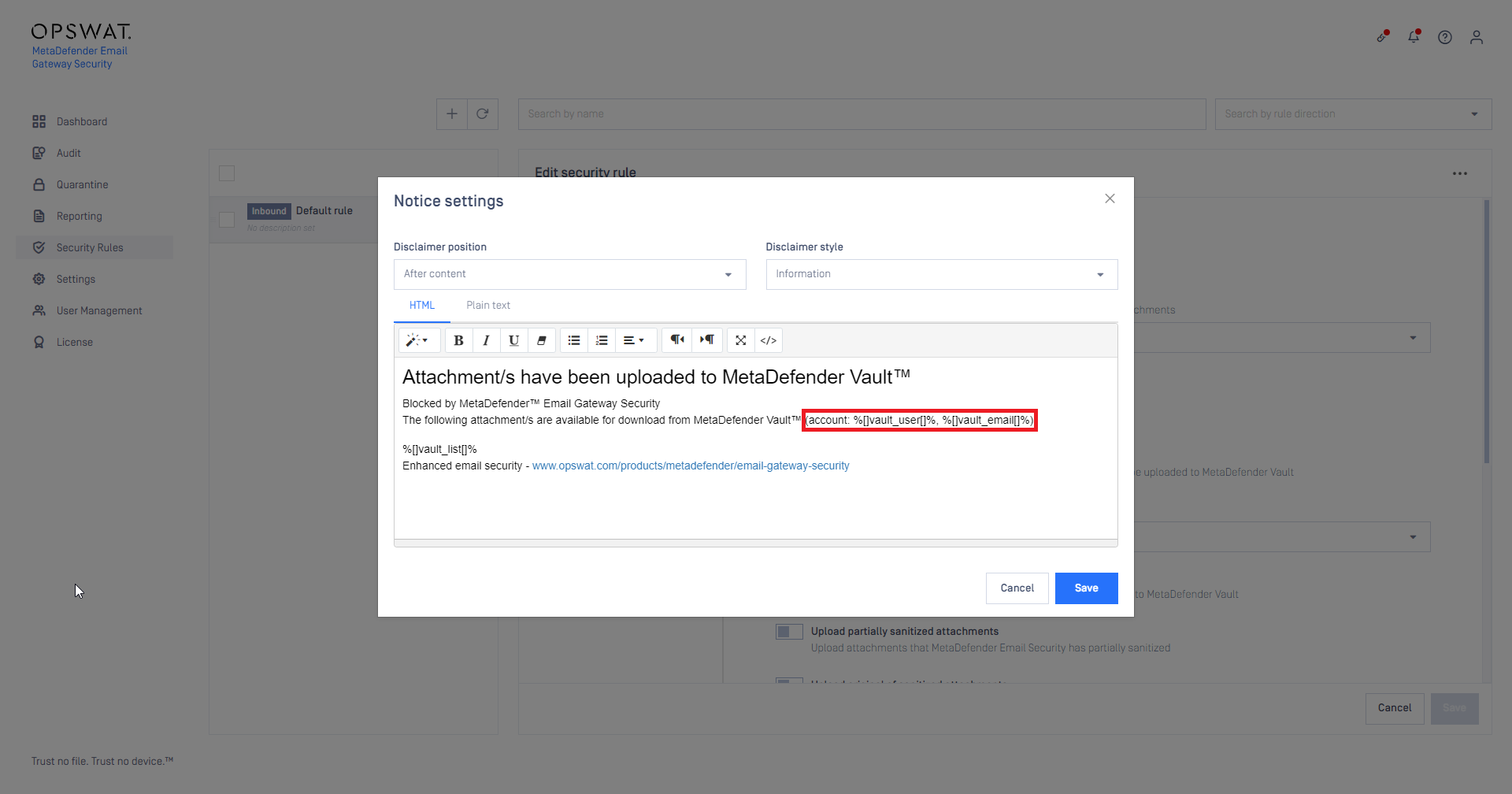
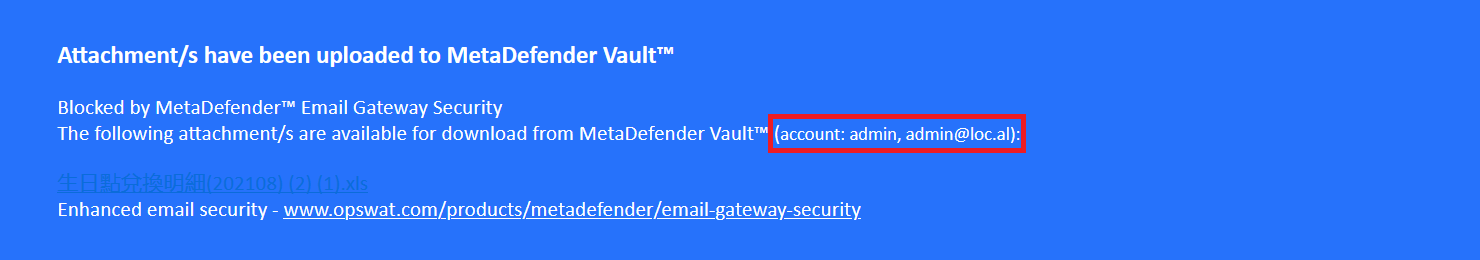
Vault account details in the upload notice
Email Gateway Security can be integrated to a secure storage solution called MetaDefender Vault to store certain kind of attachments there instead of delivering them with the email.
For uploaded attachments Email Gateway Security can append the email with a disclaimer providing information about the uploaded attachments.
Now new disclaimer variables are available that provide information about the MetaDefender Vault account to which the files have been uploaded.
For details see Server profiles, Upload attachments and Disclaimer variables.
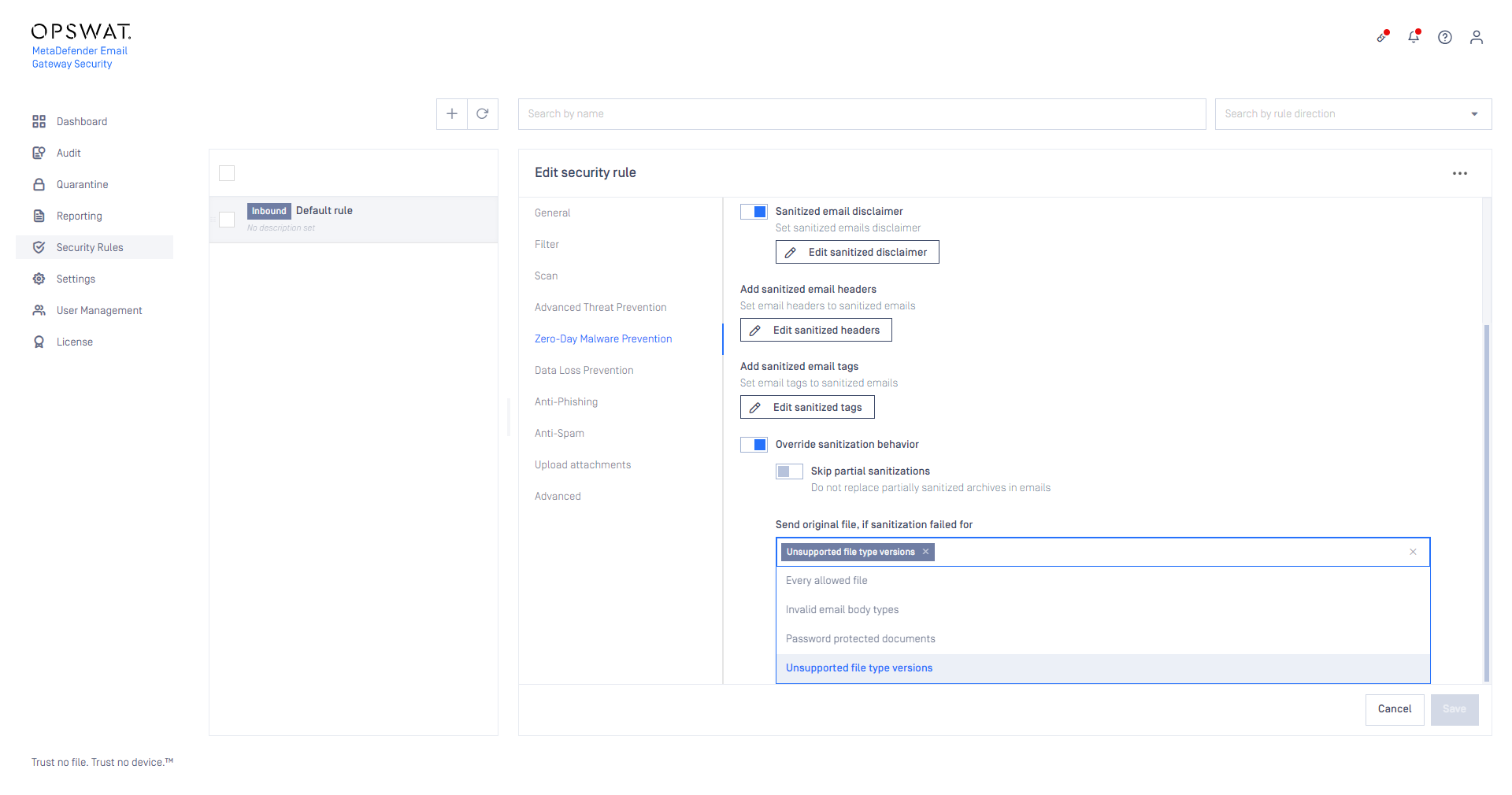
Fall back for unsupported file type version
A new option is available to fall back to the received email body or attachment file in case when the sanitization of the file fails due to file type versions (e.g. old, proprietary Microsoft Excel file types) that the Deep CDR engine does not support.
For details see Zero-Day Malware Prevention.
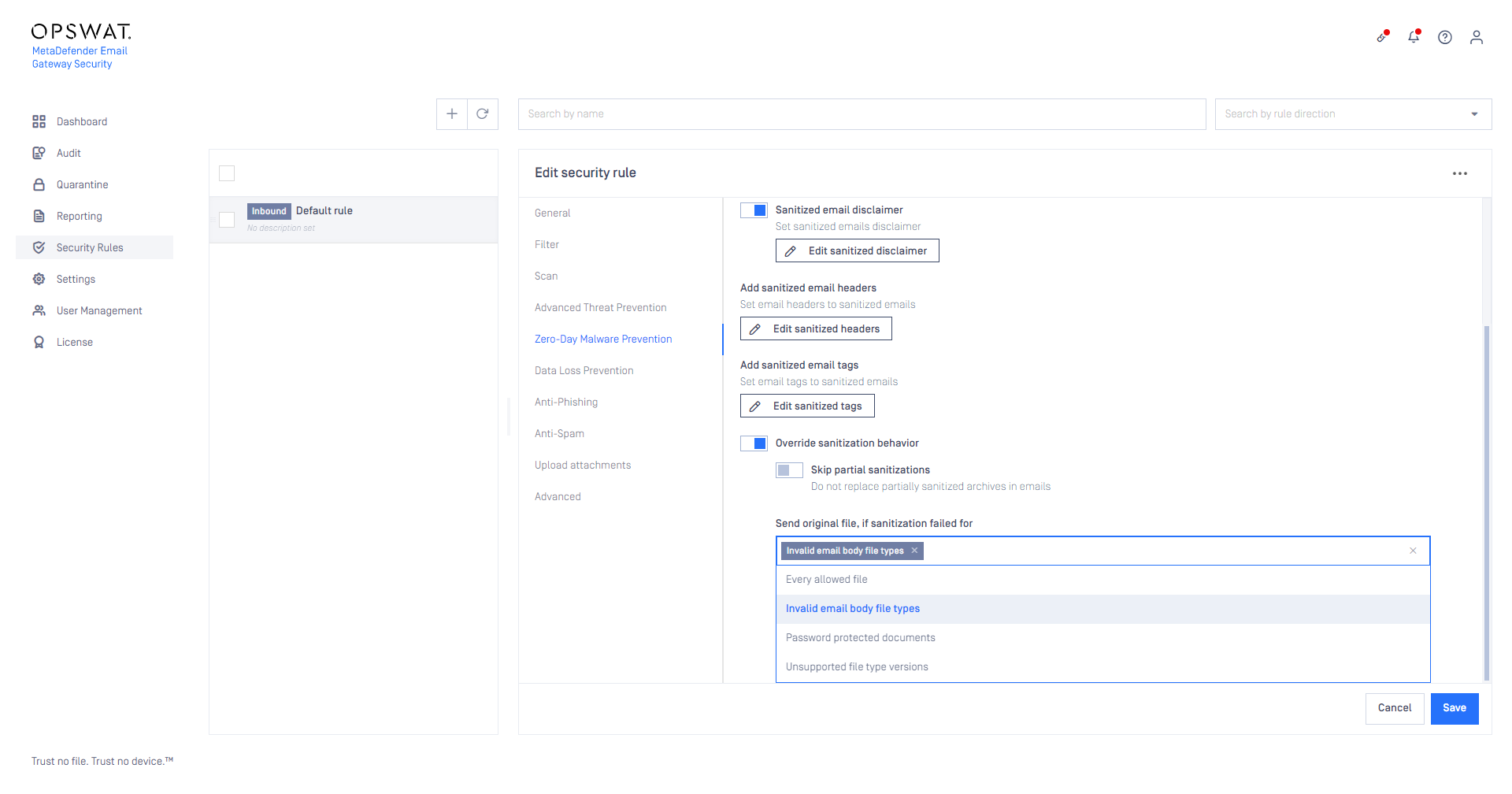
Fall back for invalid email body conversion
Email bodies can be plain text or HTML. Email Gateway Security supports converting HTML bodies to plain text bodies by the Deep CDR engine, but no other conversion is allowed.
A new option is available now to fall back to the received email body in case when the sanitization of the body fails for whatever reason, or when the sanitization in Deep CDR is set to an invalid (e.g. plain text to HTML, or HTML to pdf, etc.) email body type conversion.
For details see Zero-Day Malware Prevention.
Fixed
421 temporary error, please try again later
Due to a bug in its email parsing workflow Email Gateway Security failed to validate the syntax of certain emails and rejected them with the SMTP status ‘421 temporary error, please try again later’ after the SMTP DATA command.
Updated
OpenSSL was updated to 1.1.1m.

