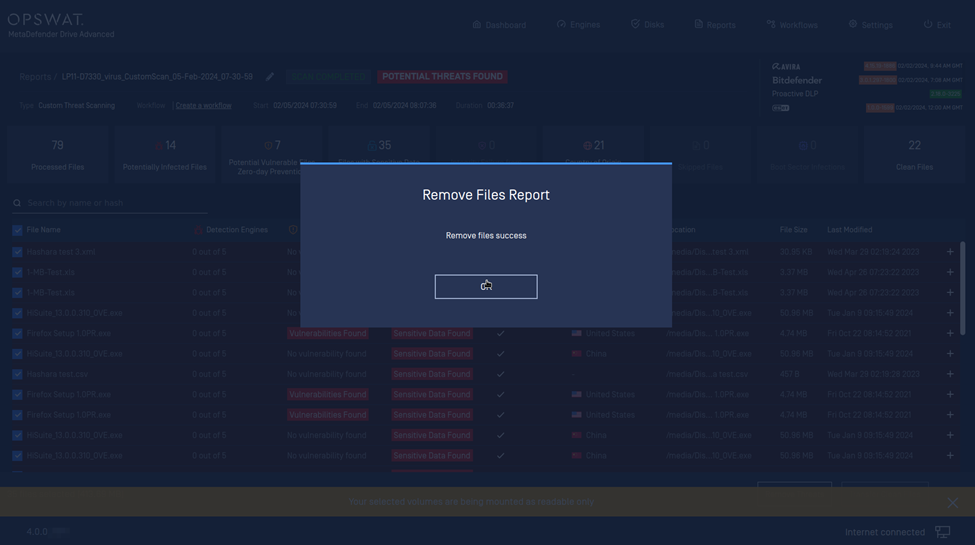
After the scan report has been generated, MetaDefender Drive's operators can sort and remove the data identified as potential threats from the system disks.
Use the filters to sort the files based on the type of the potential threat:
- Potential Infected Files
- Potential Vulnerable
- Sensitive Data
- Country of Origin
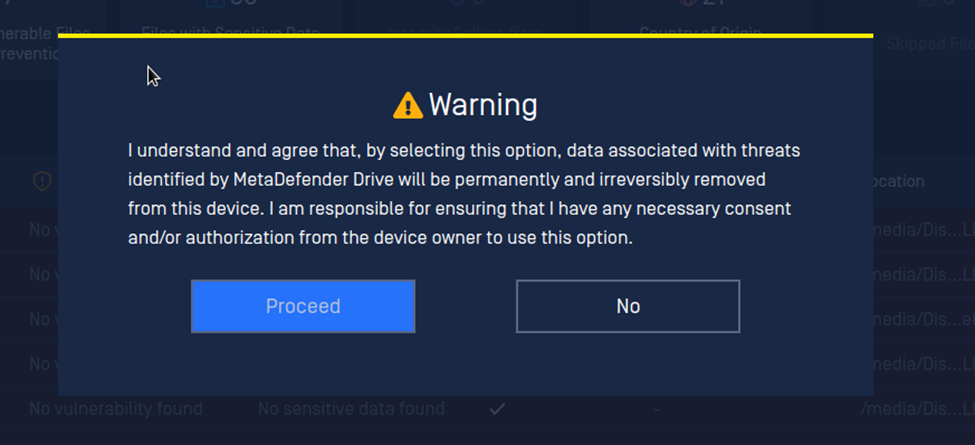
Please exercise caution with this step, as there is no way to recover your deleted data. If you are uncertain about the next step, please shut down your system, back up your data, perform the scan again, and then perform the file removal.
- Select the files you have decided to remove, and click Remove Files. Then, read the Warning and confirm that you understand the risks that come with removing the identified threats from your system, and click Proceed:
- Your disks will be mounted as WRITABLE to prepare for file removal. You can track the file removal progress displayed on the status bar at the bottom of the screen:
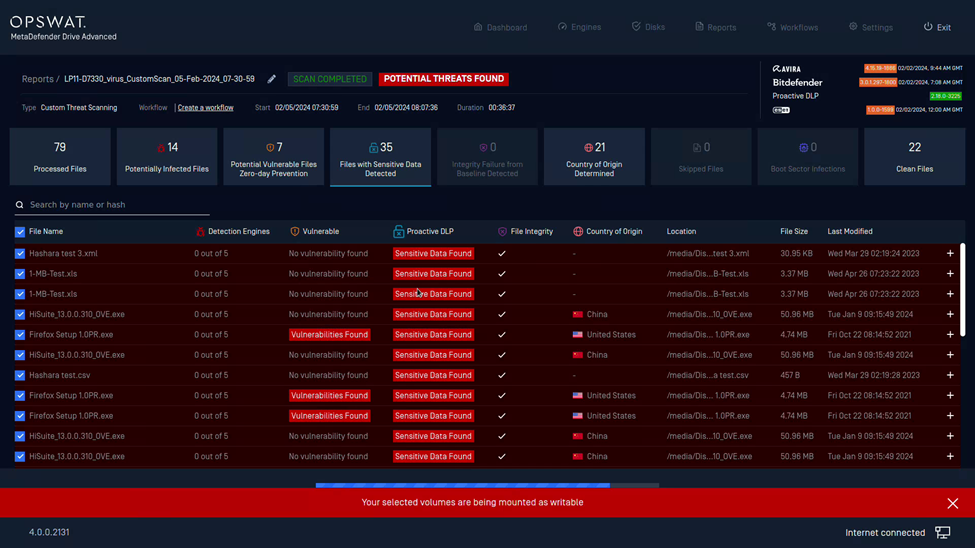
- When the file removal is complete, the system disks will be re-mounted as READ-ONLY again: