The unauthorized device is accessible under Policies → Device Policies → Unauthorized Device.
The unauthorized device page contains a list of device policies that are not allowed to connect to the system.
Any devices that are listed in the unauthorized device policy will make Neuralyzer trigger alerting when they connect to the local network.
Unauthorize device policies are added manually by the user.
Note: The blocklist policy can be detected even user didn’t turn on Anomaly Detection.
Actions on Unauthorized Device policies
1. View policy
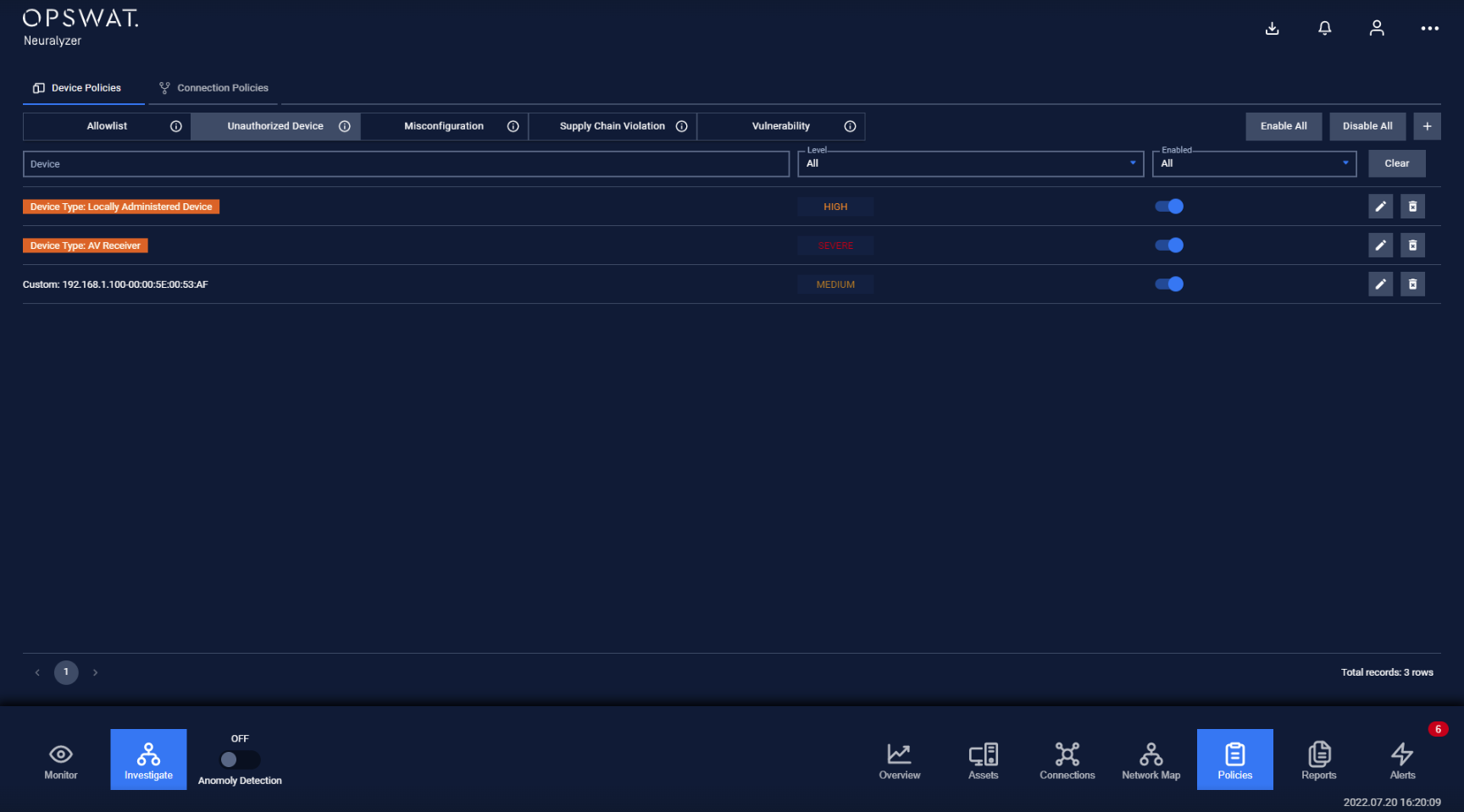
Unauthorized Device page is paginated, each page contains 20 records, the total number of policy records is displayed at the bottom of the list
Policies are displayed in a list, each record contains the following information:
- Device: the device field can have these following values:
- Device name and IP address.
- Device type/subtype, which indicates that any all devices of that type/subtype is blocked when connecting to the system.
- Vendor: which branch of device will be blocked when Neuralyzer detected.
Note: Device type will be displayed with green background.
- Criticality: Alert level (low/high/medium).
2. Create a new policy
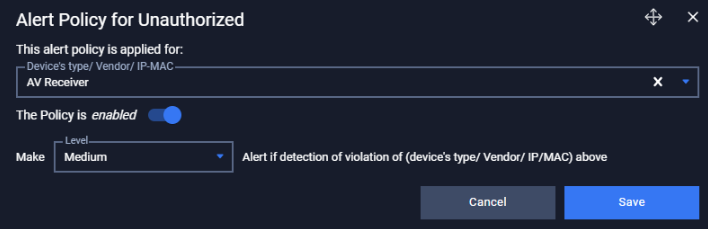
You can create a new policy by tapping on button “+” on the top right of the Policy screen, a policy creation pop-up will appear.
| Field | Type of input | Note |
|---|---|---|
| Device | Choose from drop-down list. Input device name (support searching by device’s name and IP) | |
| Enable/Disable policy option | Tap to turn on policy | Once disabled, the policy will not be applied. |
| Criticality | Choose from drop-down list | Alert criticality |
3. Edit policy
You can edit a policy by tapping on “Edit” button on the right of each policy record, a policy editing pop-up will appear.
In the pop-up editing, you can see the detail policy. You can edit by clicking on the field to be edited and perform input operations like when creating a policy.
Note: Field IP, MAC and Source of rule are non-editable .
When finished editing, click “Save” to save the changes or “Cancel” to discard all.
4. Search policy
Searching feature for policy list is located at the top of the policy page.
You can search on one or more fields of the policy, just input value onto one or more fields.
Click the “Clear” button to clear the values in the filters.
Note: You can input device name or IP into device field, we support searching device by both name and IP.
5. Remove policy
You can remove a policy from the list by clicking the "Delete" button on each the policy record.

