Title
Create new category
Edit page index title
Edit category
Edit link
Vulnerability and Patch Management
Under Policies, Administrators can set up My OPSWAT Central Management to run checks on vulnerabilities and path management on client devices (Windows, MacOS, and Linux).
Vulnerabilities and Exposures
This section of the policy allows Administrators to check for CVEs based on severity level, CVSS scores, OPSWAT scores, or specific CVEs. Administrators can also specify what types of devices that My OPSWAT Central Management checks the section against.
Specify CVEs
To specify specific CVEs for My OPSWAT Central Management to trigger an alert for, administrators can do the following:
- Sign into My OPSWAT Central Management and navigate to Policies > Vulnerability and Patch Management
- Check off Device has any CVEs from the list below and select Download Sample CVEs list. This will prompt a CSV download to begin.
- Once completed, open the CSV and follow the format to create the list of CVEs you wish to list as a critical issues. Save changes.
- Navigate back to My OPSWAT Central Management > Policies> Vulnerability and Patch Management. Select Choose File, select the file. A list of the CVEs from the CSV will appear.
- Optional: Mark as a critical issue.
- Confirm with PIN and Save.
Patch Management
This section of the policy allows Administrators to check for patch management products installed on client devices (including based on version), or any missing patches.
Require a specific patch management product
This setting within Patch Management allows Administrators to require that their client devices need a specific patch management product and to mark as an issue otherwise. To see this setting, you must enable No patch management is installed.
Here, Administrators can also specify patch management product versions as well if desired. To add a wildcard, users can enter 'x' after a version number to apply to all. For example, '1.x' would apply to all versions that start with a 1 for that product.
Exclude specific missing patches
This setting within Patch Management allows Administrators to filter out patches that may not be needed for their client devices. To see this setting, you must enable Exclude specific missing patches.
Here, Administrators can list the specific patches they wish to exclude. To exclude specific missing patches:
- Sign into My OPSWAT Central Management, and navigate to Policies > Policy Detail (select your policy) > Vulnerability and Patch Management.
- Under Vulnerability and Patch Management, navigate to the Patch Management sub-section.
- Check Exclude specific missing patches. A text box will appear.
- In the text box, add the desired patches to be excluded from the patch management scans. Once you have typed out the name or ID of the patch, press Enter to submit that patch. You must enter at least one patch to save.
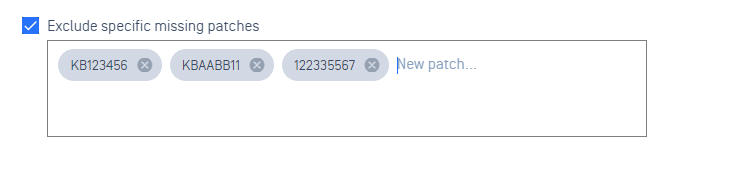
- To remove any patch exclusions, select the 'X' associated with the patch(es) you wish to remove.
- Save.
Application Updates
This section of the policy allows Administrators to check for applications installed on client devices and either enable/disable automatic updating of those applications. This is for Windows exclusively.
Here, Administrators can also list applications they wish to exclude from automatic updates. To exclude specific applications:
- Sign into My OPSWAT Central Management, and navigate to Policies > Policy Detail (select your policy) > Vulnerability and Patch Management.
- Under Vulnerability and Patch Management, navigate to the Application Updates sub-section.
- Check Prevent the following applications from being updated . A text box will appear. Note: Excluded apps will not show in the Patch Management tab in the MetaDefender Endpoint if enabled.
- In the text box, add the desired applications to be excluded from automatic updates. Once you have typed out the name of the application, press Enter to submit that application. You must enter at least one application to save.
- To remove any application exclusions, select the 'X' associated with the application(s) you wish to remove.
- Save.
Additional information on excluded applications
Applications excluded from Application Updates will still show under specific compliance categories and tabs:
- In the MetaDefender Endpoint, under the Vulnerability Detection tab, excluded applications will display but not have the option to be updated.
- Excluded applications are still considered for the device's security score.
- Excluded applications are still considered for vulnerability detection.
- Excluded applications are not automatically added to the CVE Allowlist.

