MetaDefender Transfer Guard integration with MD Core
You need a security dongle inserted in the BLUE server to be able to access MetaDefender Core GUI.
MetaDefender Core Integration
MetaDefender Transfer Guard is integrated with MetaDefender Core. Once properly Configured, all the files trasferred using MetaDefender Transfer Guard will be scanned for malicious activity by MetaDefender Core. This scan will be performed before the transfer is done. Please, if you want more details on MetaDefender Core management and operation, go to https://docs.opswat.com/mdcore
API Key
API key are required in order to enable API integration with other products.
How to generate an API Key
Before accessing MetaDefender Core GUI, the management IP needs to be changed from the default 10.10.10.10 address. Subnet 10.10.10.0/24 is an internal subnet used by MetaDefender Core and would conflict when trying to access
In MetaDefender Transfer Guard BLUE, go to http://<management IP>:8008 to access built in MetaDefender Core GUI and login.
- From the sidebar menu go to User Management.
- Click on admin user
- Copy the API key (generate one if the box is empty). We will use it to configure MetaDefender Transfer Guard BLUE side to configure the integration with MetaDefender Core
Configuring MetaDefender Transfer Guard BLUE for MD Core integration
Connection
In order to configure MetaDefender Core, fill out the necessary information on the MetaDefender Transfer Guard BLUE configuration page:
- URL: The url of the MetaDefender Core we will use to scan the files transferred (e.g http://localhost:8008).
- API Key: Paste the API Key copied in the previous step, API Key.
- Timeout [Sec. 1-600]: can be used to specify a timeout when waiting for results from MetaDefender Core.
- Enabled: check this box to activate MetaDefender Core scan for trasferred files.
- Block empty files: 0B files will be blocked by MetaDefender Core.
- Test Connection: press this button to check if the connection with MetaDefender Core instance is OK.
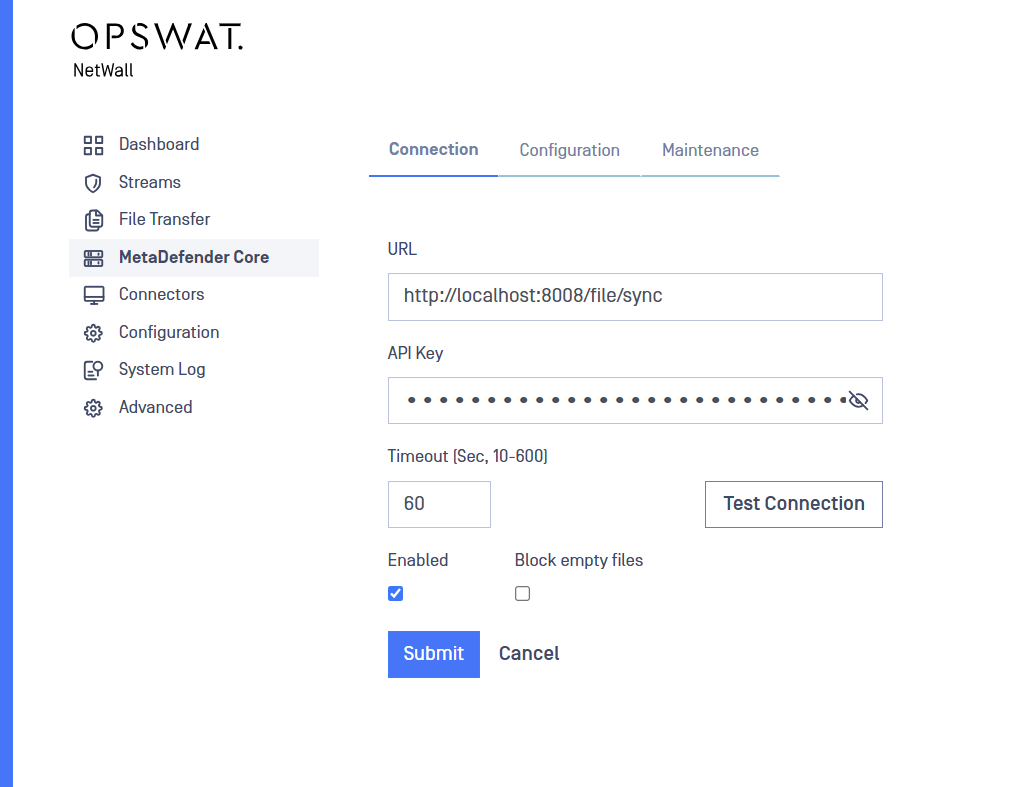
Click Submit to save the changes. MetaDefender Transfer Guard will now process files with MetaDefender Core.
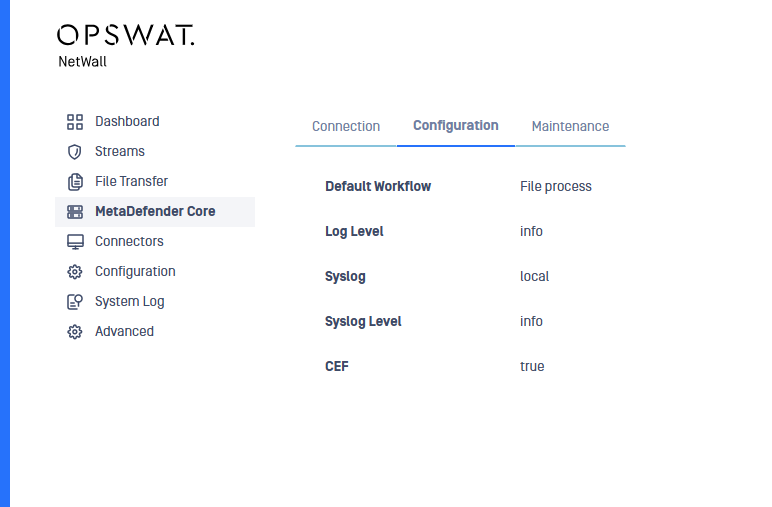
Configuration
In Configuration tab, the user have the following options:
- Default Workflow: Select the default MetaDefender Coreworkflow to be used to scan the transferred files for all the channels.
- Log Level: Level of logging, The default value is info.
- Syslog: Switch on logging to a local or remote syslog server. Multiple servers can be specified separated with comma.
- Syslog Level: Level of Syslog logging.
- CEF: If this box is checked, the log format is Common Event Format.
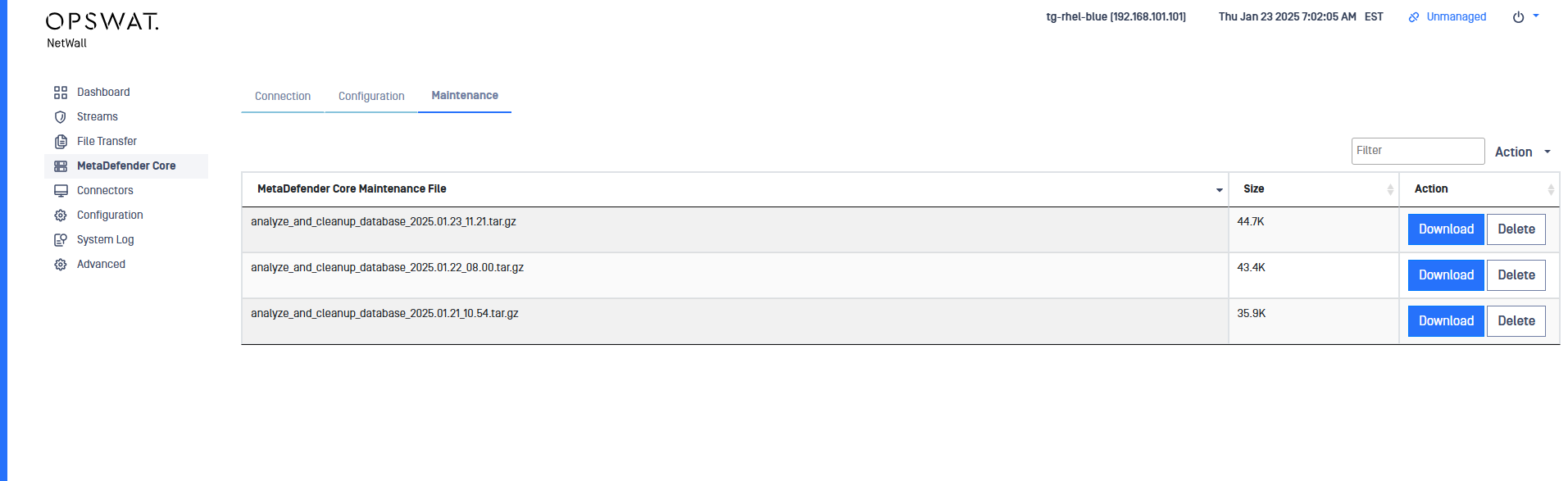
Maintenance
In daily basis the system performs MetaDefender Core data base maintenance operations, freeing database space and generating database log files. Once generated, users can download and/or delete these files in the Maintenance label in MetaDefender Core section of the right-side menu.
Historical Data
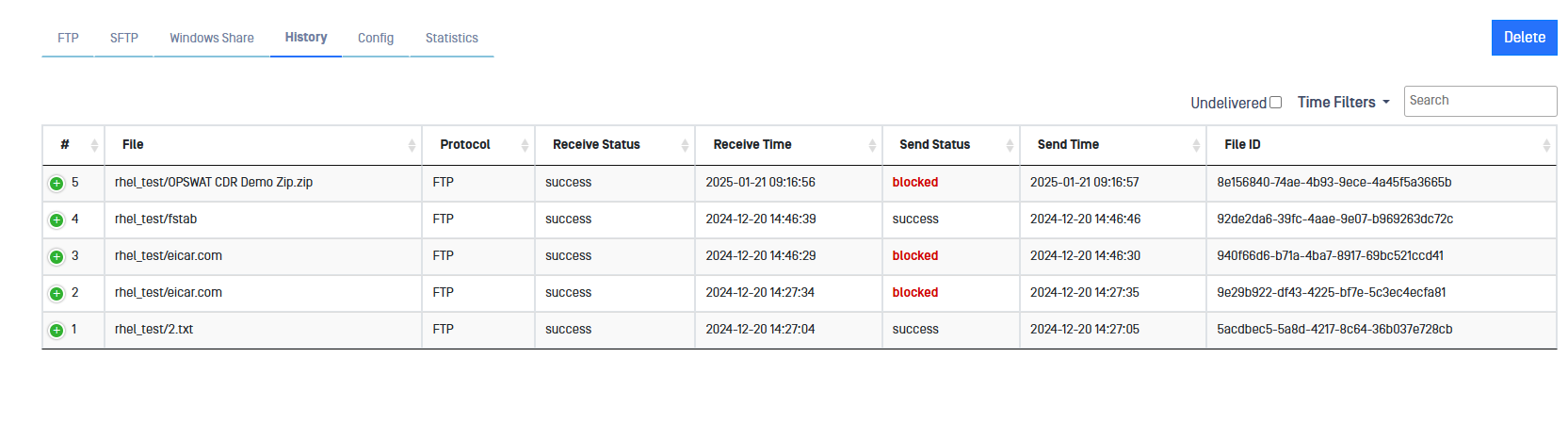
MetaDefender Transfer Guard will keep record of the files transferred from BLUE to RED. To consult the Historical data just click on the History tab within File Transfer section.
Please, notice that File Transfer Historical Data is not stored in backups. Check https://docs.opswat.com/netwalldiode/configuration/diode-backup for more information about that feature.
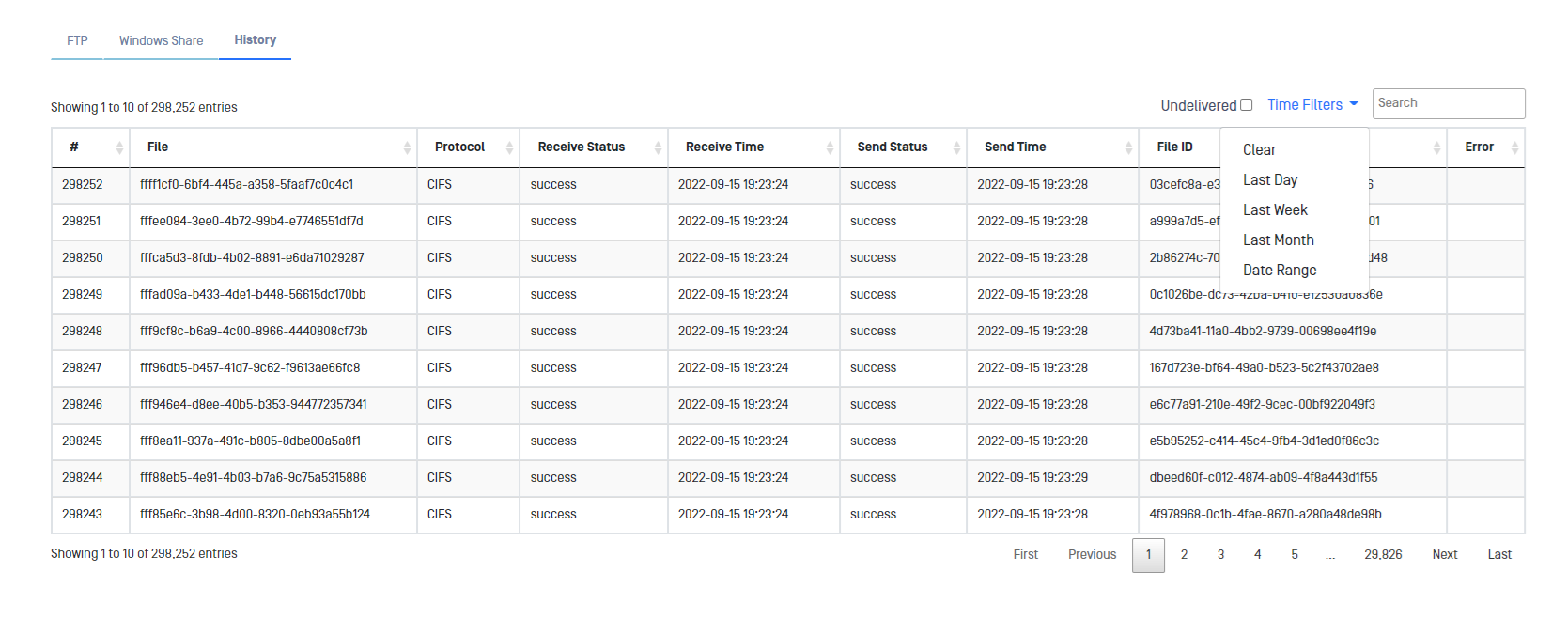
Once the data is loaded it can be filtered in several ways.
- Undelivered: Only shows undelivered transfers. File haven't been received by RED side.
- Time filters: Daily, weekly and monthly filters can be applied. A date range can also be defined.
- Search box can be used to search for specific files by typing text.
Please, notice that this information can be checked in both sides BLUE and RED.
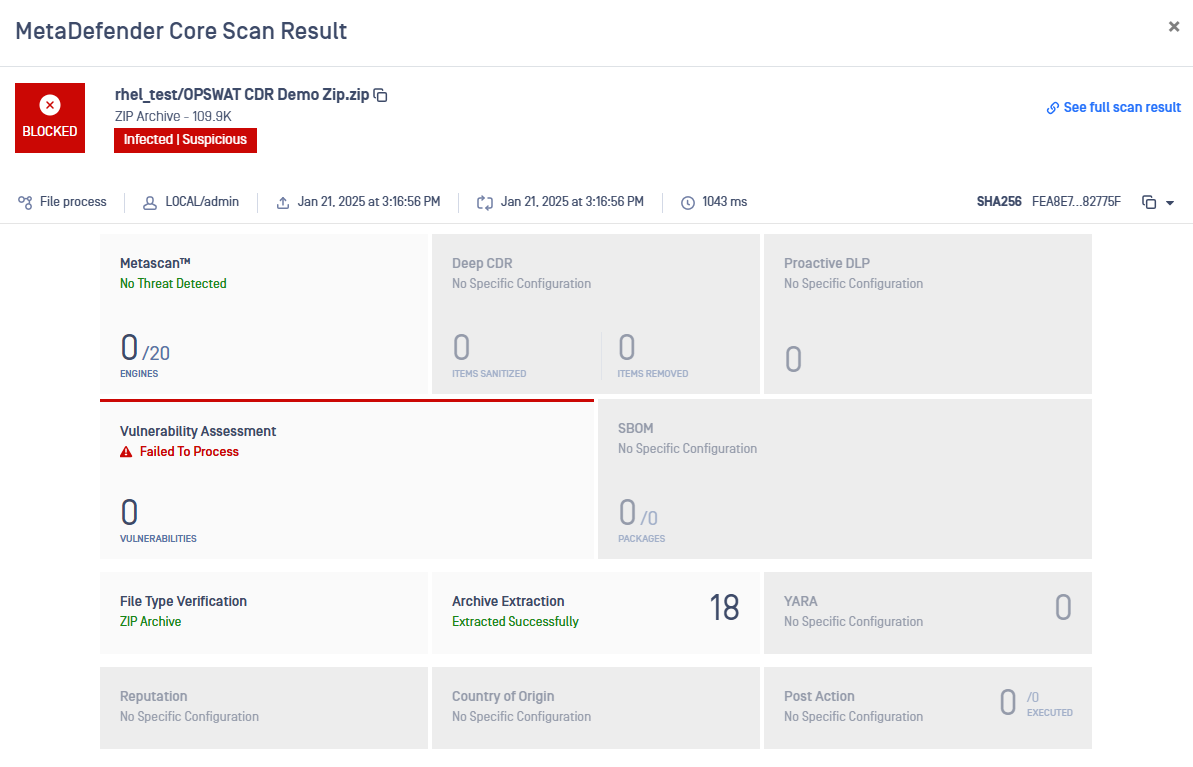
MetaDefender Core Scan Results
When thew result of scan is unsatisfactory, that file would be blocked.
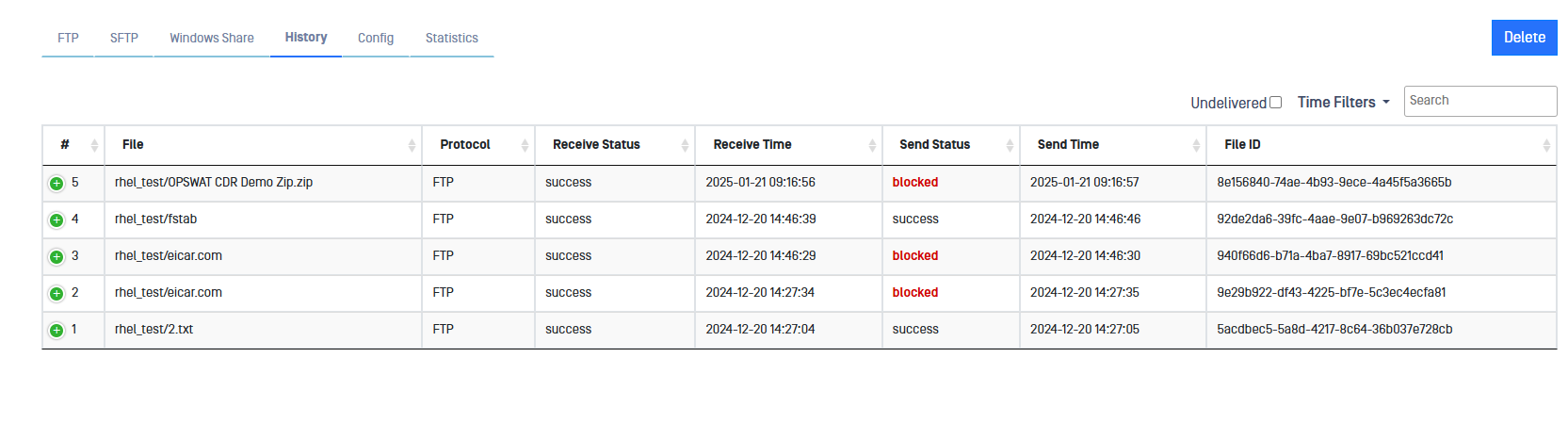
Whenever a file is blocked, the user can check the MetaDefender Core Scan Result report by clicking on the word blocked of the corresponding file.