Title
Create new category
Edit page index title
Edit category
Edit link
Add An Amazon S3 Storage
In order to integrate Amazon S3 with MetaDefender for Secure Storage please follow these steps:
- From the left side menu, navigate to Storage units, and from the Object Storage tab, choose Add Amazon S3 Storage
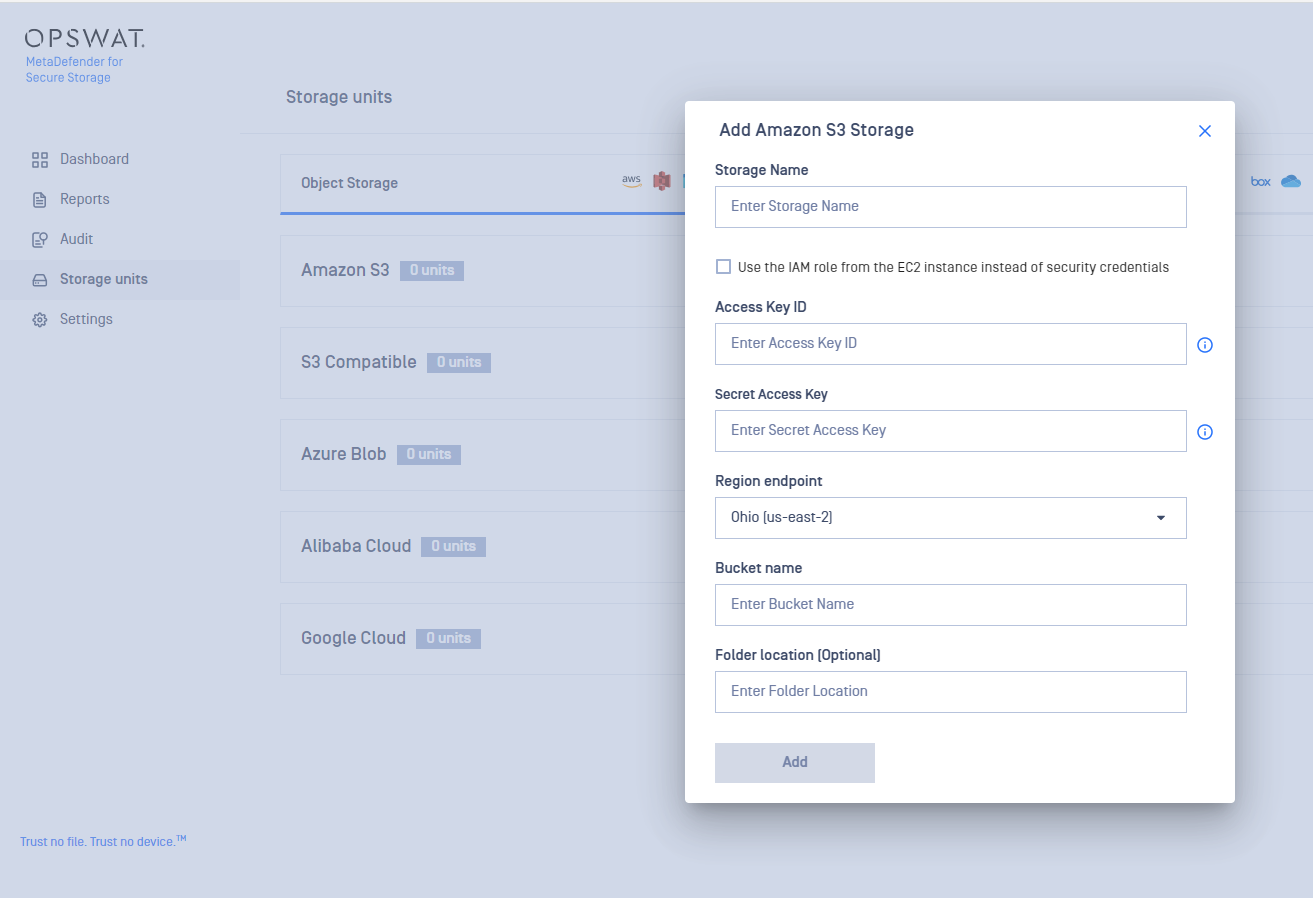
- Give your storage a name so you can easily identify it later
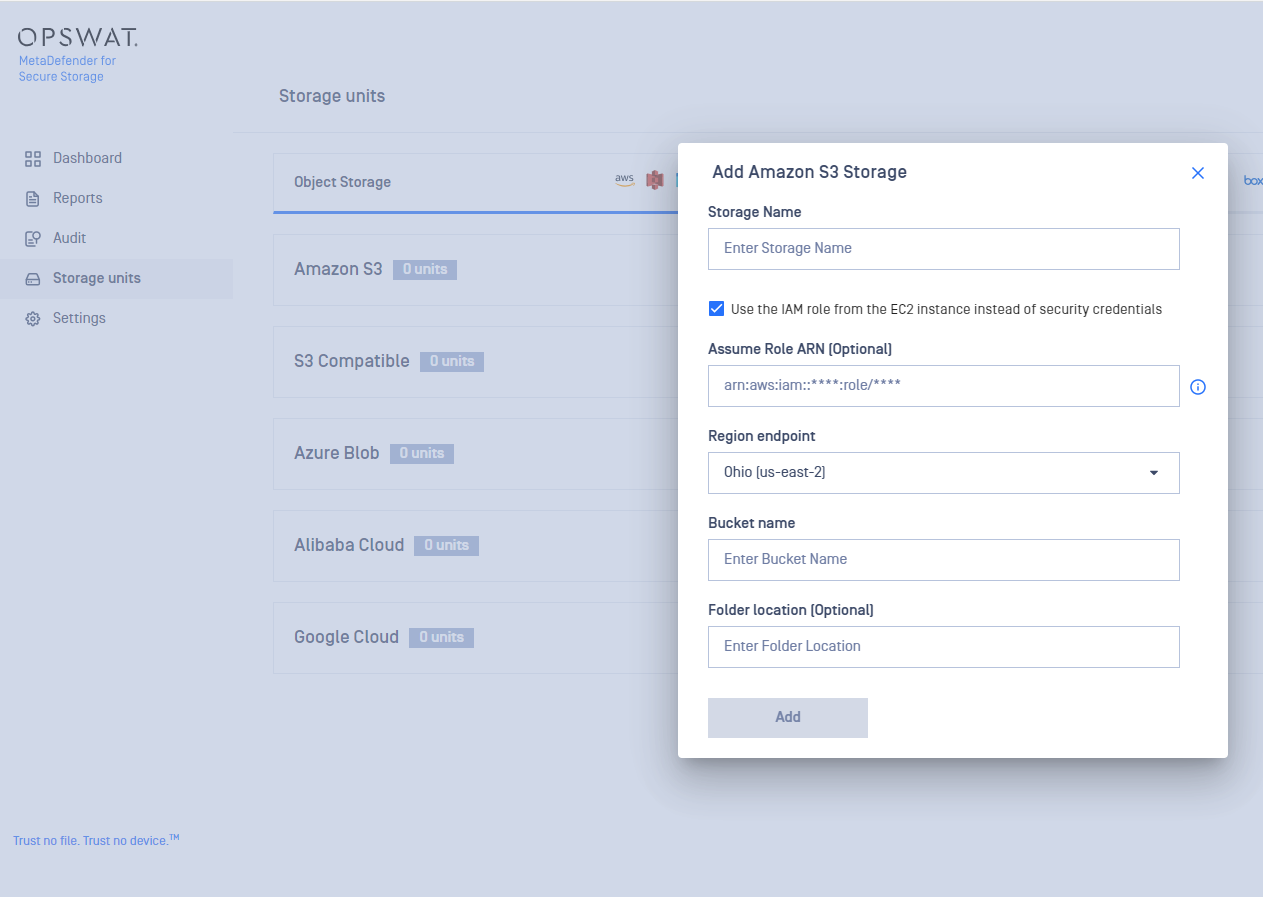
- There are two ways to connect:
- via the IAM role from the EC2 instance (If you choose this option, skip the following two steps and continue from step 6)
- using security credentials
- Enter your Access Key ID. Scroll to the end of this page for more details.
- Enter your Secret Access Key. Scroll to the end of this page for more details.
- Choose the region endpoint where your S3 endpoint is located.
- Enter the name of the bucket you wish to process with MetaDefender for Secure Storage.
- If you wish to only process a particular folder enter the name or path of the folder in the Folder location field. Leave this field empty if you wish to process the entire bucket.
- Select the MetaDefender Core Pool that you wish to use.
- Select Add in order to finish the process.
Where can I find the Access Key ID and Secret Access Key?
To generate an Access Key ID / Secret Access Key pair please follow these steps:
- Log in to IAM Console and go to Users
- In the Details pane, click the appropriate IAM user or create one if none exists
- From the Security Credentials, tab click Create Access Key
If you already have a maximum of two access keys—active or inactive—you must delete one first before proceeding. If you need more than two root access keys, IAM users (each of whom can be assigned their own access keys) would probably better suit your requirements.
Using IAM role for Amazon S3 integration
On S3 integration with IAM, the role configured on the EC2 machine will be used to authenticate.
With the optional field of Assume Role Arn, Metadefender for Secure Storage allows integration with other buckets that are in different accounts from the current AWS account.
This is possible by configuring Assume Role ARN field, with the ARN of the role that has access to the other account's S3 bucket.
Note:If the EC2 instance that is running MDSS is also using IMDSv2 you will need to run the following AWS CLI command and add your instance id to it:
aws ec2 modify-instance-metadata-options --instance-id <INSTANCE_ID> --http-put-response-hop-limit 3 --http-endpoint enabledThis is required because MDSS runs within docker and IMDSv2 restricts the number of "hops" each request to the metadata service can make.
Necessary AWS policies
These are the necessary AWS policies required in order to add an Amazon S3 Storage:
s3:GetObjects3:PutObjects3:GetObjectVersions3:ListBuckets3:ListBucketVersionss3:GetObjectTaggings3:GetObjectVersionTaggings3:PutObjectTaggings3:PutObjectVersionTaggings3:DeleteObjects3:DeleteObjectVersions3:PutLifeCycleConfiguration

