Title
Create new category
Edit page index title
Edit category
Edit link
Configuration
This section covers configurations specific to the High Availability (HA) cluster setup.
HTTPS and TLS certificate
MetaDefender MFT HA Controller™
To enable HTTPS for MetaDefender MFT HA Controller™, navigate to the <installation directory>\appsettings.json file. Within the Kestrel:Endpoints section, modify the Url to use the https scheme and specify the desired port. Additionally, include the Certificate section to define the certificate settings.
Example
..."Kestrel": { "Endpoints": { "Https": { "Url": "https://0.0.0.0:8100", "Certificate": { "Path": "<path to .pem/.crt file>", "KeyPath": "<path to .key file>" } } }}...MetaDefender® MFT
In the recommended network setup the communication between the HA Controller and the active/passive nodes occurs over an internal network. In this scenario, HTTPS is not strictly required—but it is recommended for added security. Using TLS internally helps to protect against internal threats, misconfigurations, or accidental exposure.
How to configure on both nodes
You can configure HTTPS for the MetaDefender® MFT nodes from the Web UI, see more details here.
Since the server configuration is instance node specific you have to separately configure HTTPS for both active and passive nodes. Because certificate configuration can only be applied on a node while it is active, updating the certificate on the passive node requires manually triggering a failover so that the passive becomes active. After configuring the certificate on that node, you may optionally trigger failover again to restore the original node to active status. See more details about manually trigger a failover mechanism here.
If you change the protocol, hostname, or port, you must update the Nodes configuration section in MetaDefender MFT HA Controller™ to reflect the new values.
More information about the Nodes section can be found here.
Certificate requirements
The MetaDefender MFT HA Controller™ will validate the certificate presented by each application node—checking both its trust chain and validity period—before forwarding traffic or accepting node communication.
If you issue a custom certificate (or self-signed cert) for the application servers, you must also install the corresponding root certificate (or CA cert) into the MetaDefender MFT HA Controller™’s trusted root certificate store so it can validate server certificates.
HA Cluster Notification URL
If you are using email notifications you have to configure the Notification URL Configuration. Change the Notification URL to the HA Controller’s address.
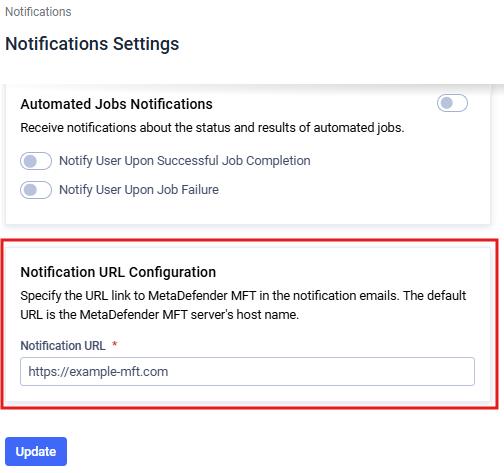
This address will be used in the email notifications as link to the MetaDefender® MFT. Since users will access the application through the MetaDefender MFT HA Controller™ the notification URL must be changed to it's address.
More information can be found at the Notification URL section.
Server config
Server configuration is instance-specific and stored locally (not in the shared database). All settings under Settings > Security > Server Configuration—such as HTTPS, rate limiting, and port configuration—must be set independently on each node.
Changes made on one node do not automatically apply to the other node.
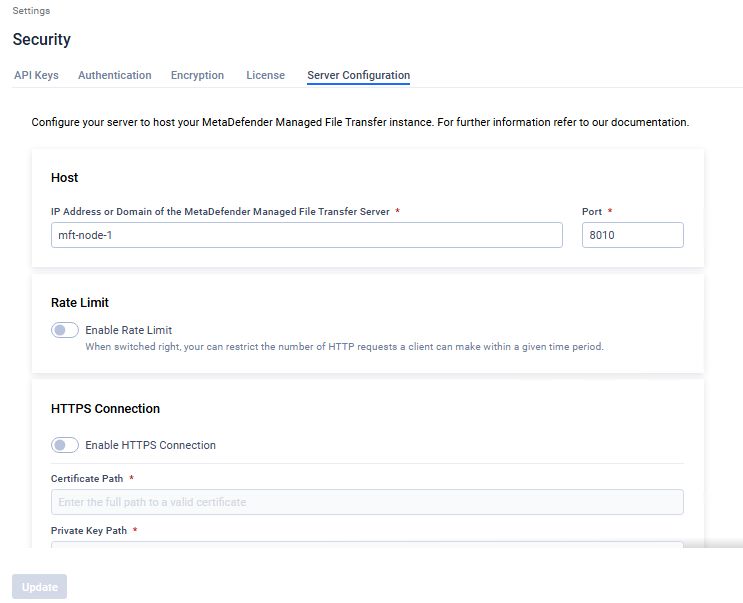
It's not necessary to align the MetaDefender® MFT Server Configuration across nodes. For instance, the hostname will inherently differ between nodes. Additionally, if Node1 has higher specifications and requires a larger rate limit, you can configure a higher rate limit on Node1 compared to Node2.
You can use the Host field to check which Node is currently active.

