Title
Create new category
Edit page index title
Edit category
Edit link
Release Notes
| Version | 5.9.0 |
|---|---|
| Release date | 21 May 2025 |
| Scope | Focused on new functionalities, enhancements and bug fixes |
Before upgrading MetaDefender ICAP Server to v5.9.0 or newer from v5.6.0 or earlier, make sure you review the Release Notes and the following Documentation:
New Features, Improvements and Enhancements
| Details | ||
|---|---|---|
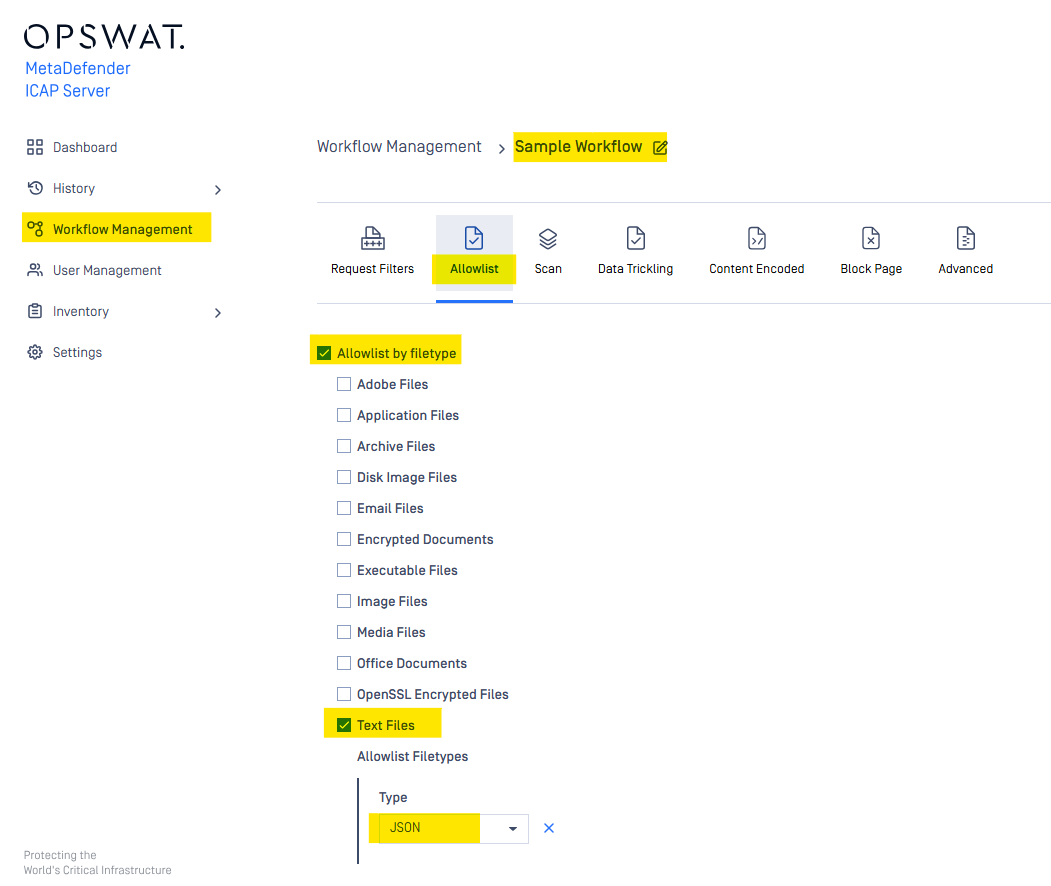
| Allow List by File Type Per Workflow | Starting from v5.9.0, MetaDefender ICAP Server now performs File Type Verification before sending files to MetaDefender Core for processing. This helps reduce the MetaDefender Core load by filtering unnecessary files before scanning (see Allow list). Note: To enable the Allow List feature on Rocky Linux 9.x / Red Hat 9.x, users must install
| |
| New UI for Downloading Support Packages | Users can now generate and download support packages directly from the UI for troubleshooting purposes, instead of executing .bat or .sh scripts from the CLI. 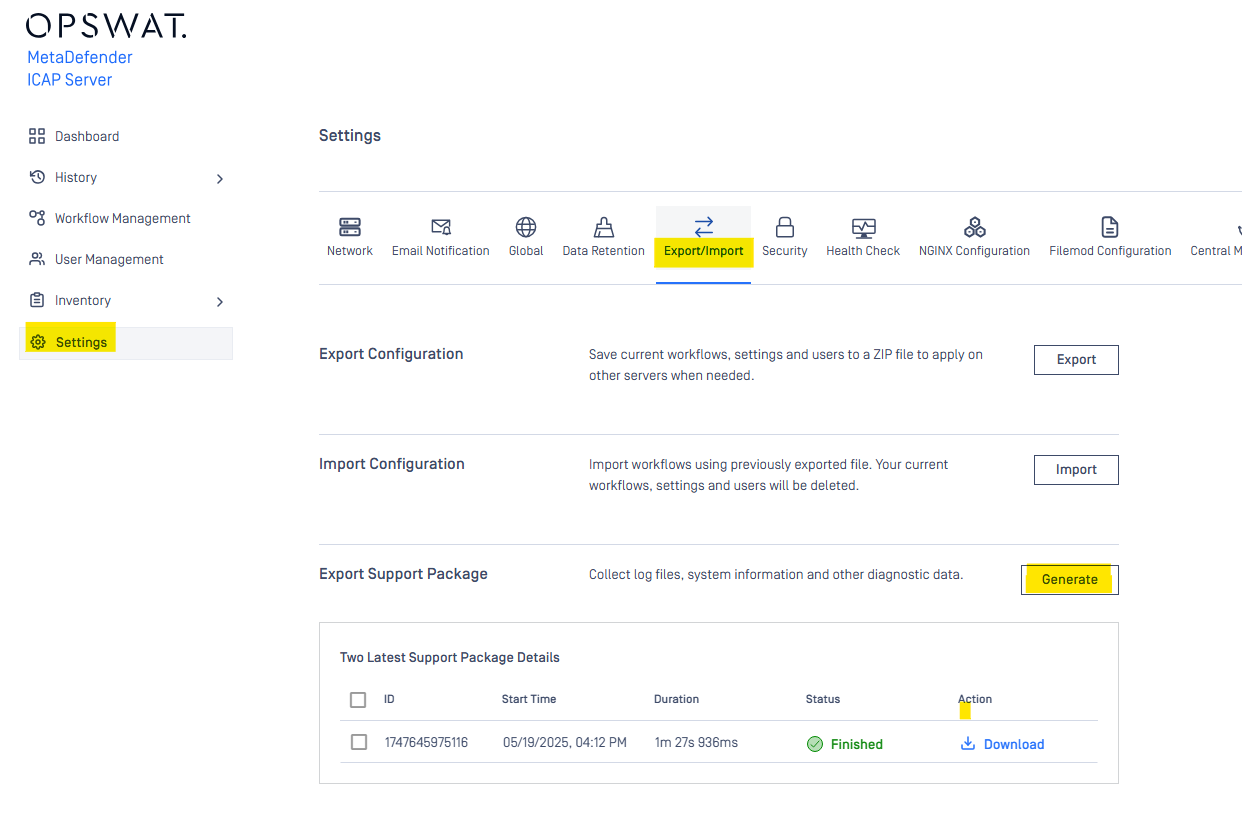 | |
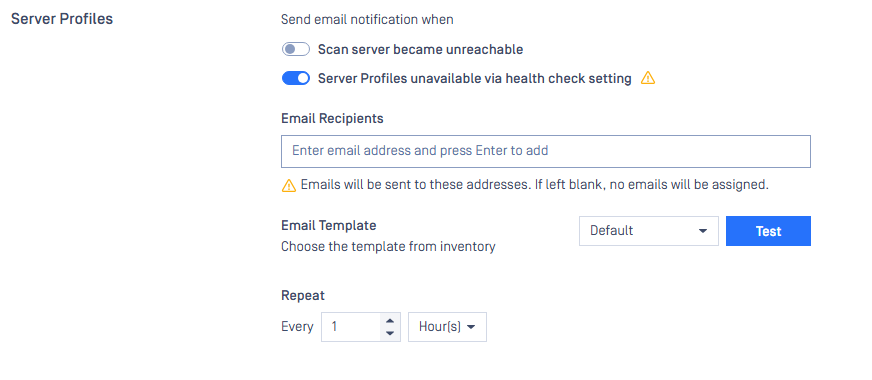
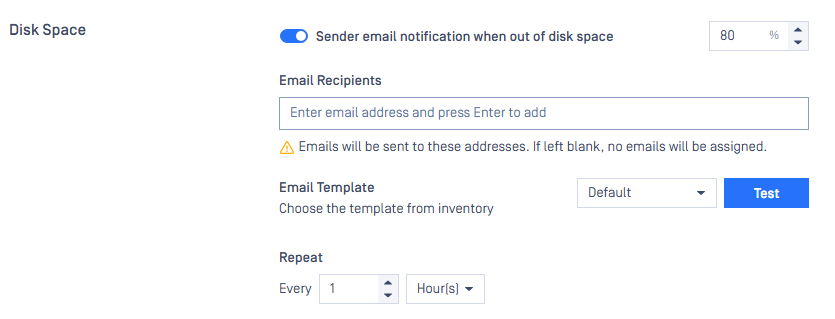
| Email Notification Enhancement | Support for new email notifications for:
| |
| CIS Support for Linux | Supports CIS Level 1 for Ubuntu 22.04, 24.04 and RHEL 9 (refer to CIS Level 1 Guidelines) | |
| Security Enhancements | Upgraded third-party libraries for improved security:
| |
| Usability Improvements |
|
Bug Fixes
| Details | |
|---|---|
| Minor Fixes |
|
Known Limitations
| Details | |
|---|---|
| Proxy Configuration | Currently, HTTPS proxy configuration is not supported. |
| SAML Directory (SSO Integration) Limitations | In MetaDefender ICAP Server v5.5.0, users cannot create a new SAML directory via the web UI.
|
| Stability Issues on Red Hat / CentOS with Kernel Version 372 | MetaDefender ICAP Server 5.1.0 or newer may encounter stability issues on Red Hat / Cent OS systems running kernel version 372. Solution: Upgrade to kernel version 425, where Red Hat has resolved this issue. |
| MetaDefender ICAP Server's NGINX Web Server Fails to Start with Weak Cipher Suites for HTTPS | Starting with MetaDefender ICAP Server v5.1.0, OpenSSL 1.x has been replaced with OpenSSL 3.x -- across the product and its dependencies -- to enhance security and address vulnerabilities. As part of this upgrade, NGINX's OpenSSL 3.x on MetaDefender ICAP Server now enforces stricter cipher policies and rejects all weak cipher suites. The web server now only accepts "HIGH" encryption cipher suites https://www.openssl.org/docs/man1.1.1/man1/ciphers.html (MD5 and SHA1 hashing based are also not accepted). As a result, if you already configured MetaDefender ICAP Server for HTTPS using a weak SSL cipher with your certificate, the server will not start due to the enforced security policies in NGINX's OpenSSL 3.x. |
| no_proxy Configuration | Starting with MetaDefender ICAP Server v5.1.0, the no_proxy setting must support CIDR for IP addresses.
For more details, refer to No Proxy configuration |
| Connect to MetaDefender Core with TLS on Debian OS | MetaDefender ICAP Server v5.1.0 on Debian OS must execute the two following commands to enable TLS when connecting to MetaDefender Core:
Resolution: Upgrade to MetaDefender ICAP Server v5.1.1, where the issue is resolved. |
| TLS 1.3 Not Supported on Windows Server 2012 | TLS 1.3 is not supported on Windows Server 2012 due to limitations with Schannel SSP. Reference |