Title
Create new category
Edit page index title
Edit category
Edit link
Version 5.6.2
| Release date | Scope |
|---|---|
| August 8th, 2022 | MetaDefender Email Gateway Security 5.6.2 is a maintenance release focusing on minor improvements and fixes. |
New & improved
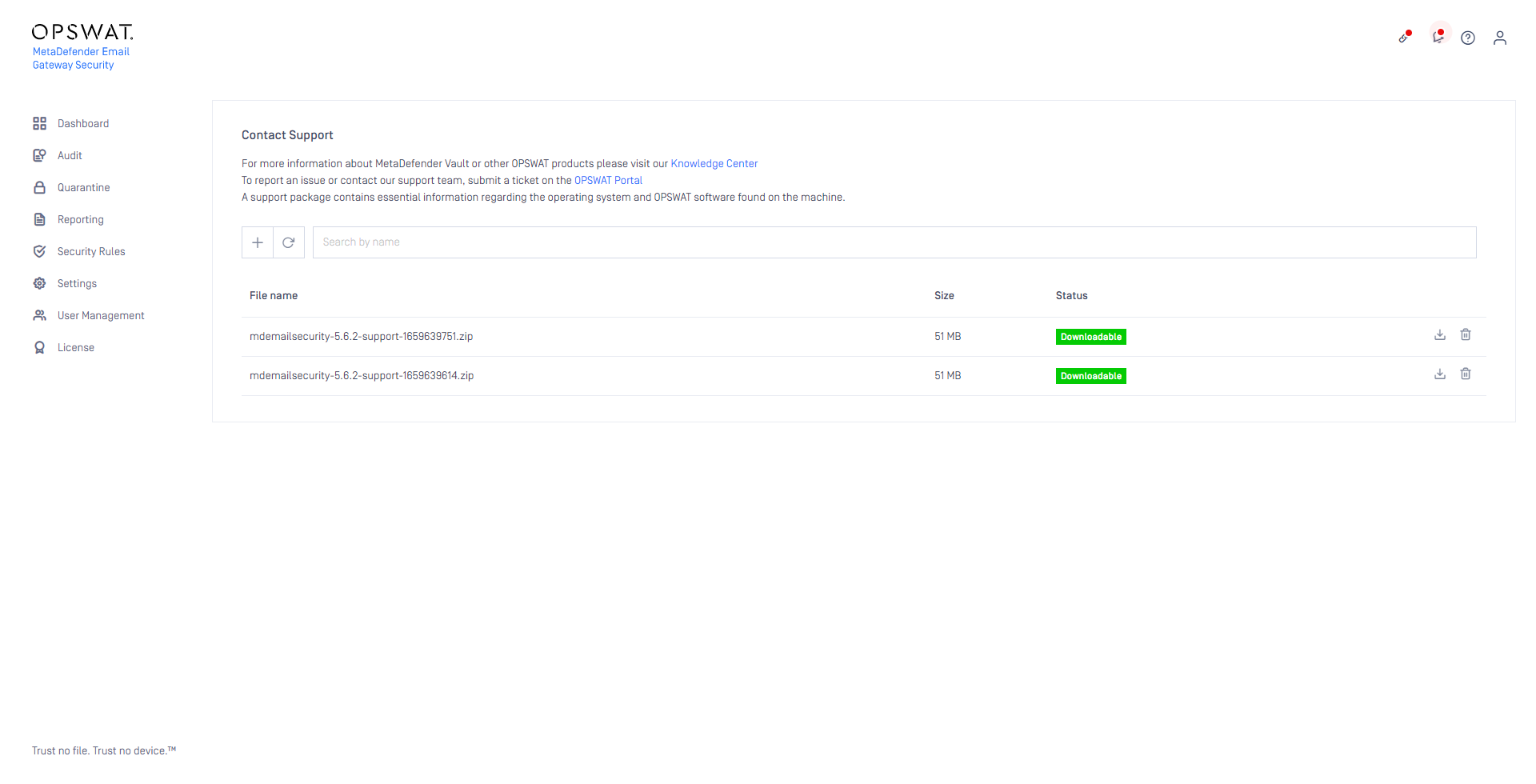
Managing support packages through GUI
Email Gateway Security support packages can now be generated and downloaded through the Web Management Console GUI. Using the Web Management Console, support packages can be downloaded through a web session, no direct access is needed to Email Gateway Security's file system.
For details see How to generate support packages.
Disclaimer variable of blocked attachments
A new disclaimer variable has been introduced that lists the file names of blocked attachments.
For details see Disclaimer variables.
Customizable quarantine report schedule
Hourly and daily quarantine reports can be configured which minute of each hour or what time on each day the quarantine report is to be assembled and sent.
For details about quarantine reports see Quarantine reports.
For details about the schedule customization see Registry configuration.
Untitled attachments get correct extension
Some email clients add attachments to emails (e.g. calendar invites) with no file name at all. Under special conditions these unnamed attachments can cause file type mismatch - and are blocked - in MetaDefender Core.
To avoid such situations, Email Gateway Security will fabricate a file name with correct extension (e.g. [Unnamed attachment].ics in case of a calendar invite) before passing these unnamed attachments to Core.
Changed
Delivering processed blocklisted files
When Enable processing of blocklisted files was on in the Core side rule, then the attachment was delivered, even if the attachment file type was blocklisted.
Now, if the attachment is blocklisted, then it gets blocked in any case.
Attachments with no file extension
Previously attachments in emails without a file name extension got the MIME Content-Type: application/octet-stream. This could lead to email clients adding unexpected extensions to the attachment files (e.g. .dat extension).
Now Email Gateway Security determines the MIME Content-Type based on the file type the attachment was converted to by Deep CDR (when there is a conversion). This way there is a lower chance for unexpected file extensions.
Fixed
Alert emails generated in a recursive loop
Alert emails MetaDefender Email Gateway Security alert: SMTP relay refused email were generated in a loop when no server profile was configured for Alerts & Reports.
Incorrect session timeout validation
Session timeout validation allowed too large values causing users potentially being locked out.
The validator is changed now to allow the maximum value to 1 day (86400000 ms).
Filenames triggered Safe URL Rewriting
File names with extension (and other cases where there was no whitespace ahead a dot character) were misinterpreted by the parser as URLs and Dynamic Anti-phishing (URL rewriting) was applied on them.
Disclaimers appended to attachments
Due to a bug in the MIME parser, in certain cases disclaimers were appended to text file attachments.
Link editor opened in the background
The link editor of the disclaimer editor opened in the background rendering impossible to edit links.
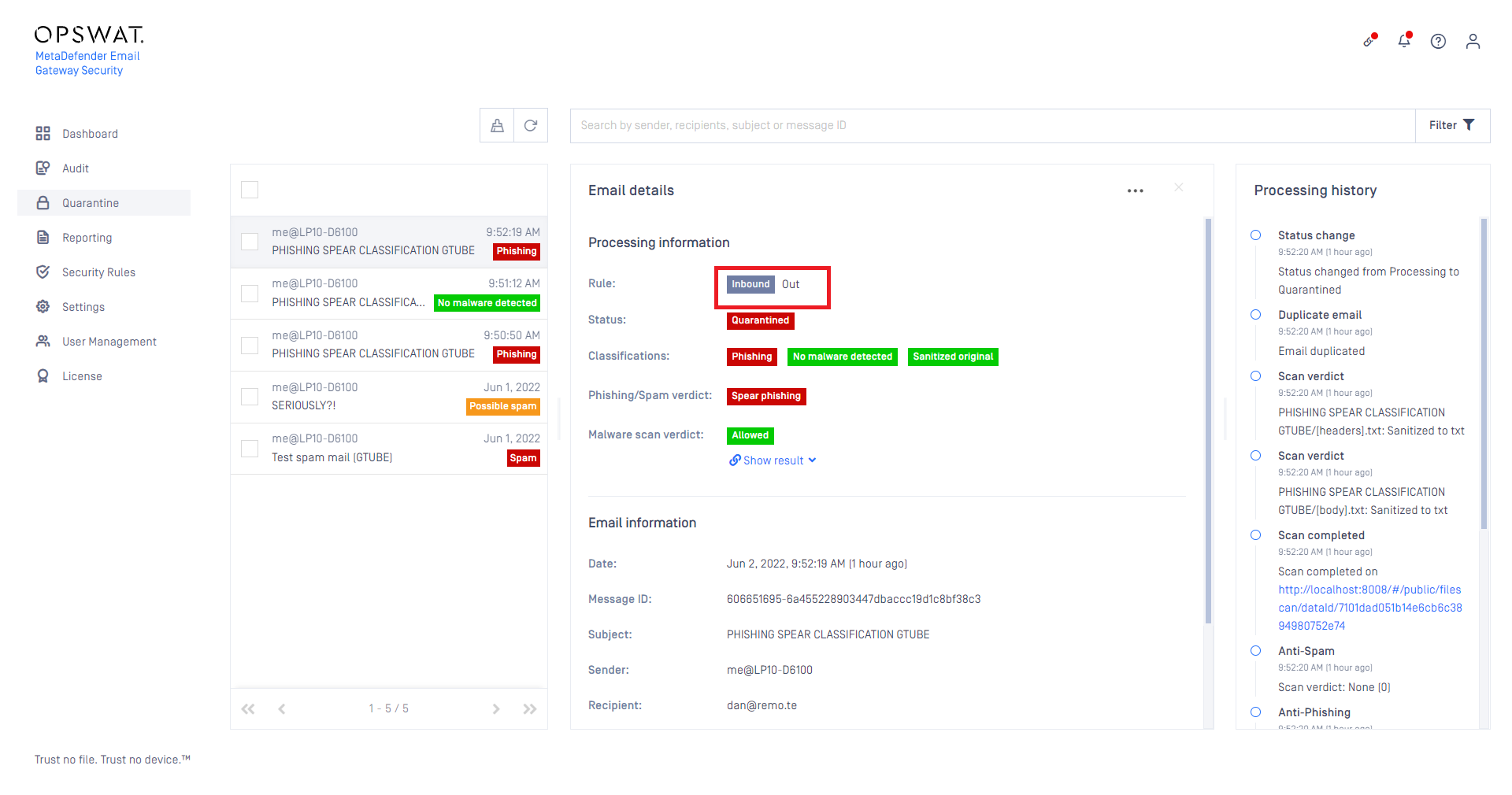
Outbound rules marked as inbound
In the Quarantine, rules (even outbound ones) were always marked as inbound.
Updated
| Component | Version |
|---|---|
| OpenSSL | 1.1.1p |

