| Release date | Scope |
|---|---|
| May 31st, 2022 | MetaDefender Email Gateway Security 5.6.1 is a maintenance release focusing on minor improvements and fixes. |
New & improved
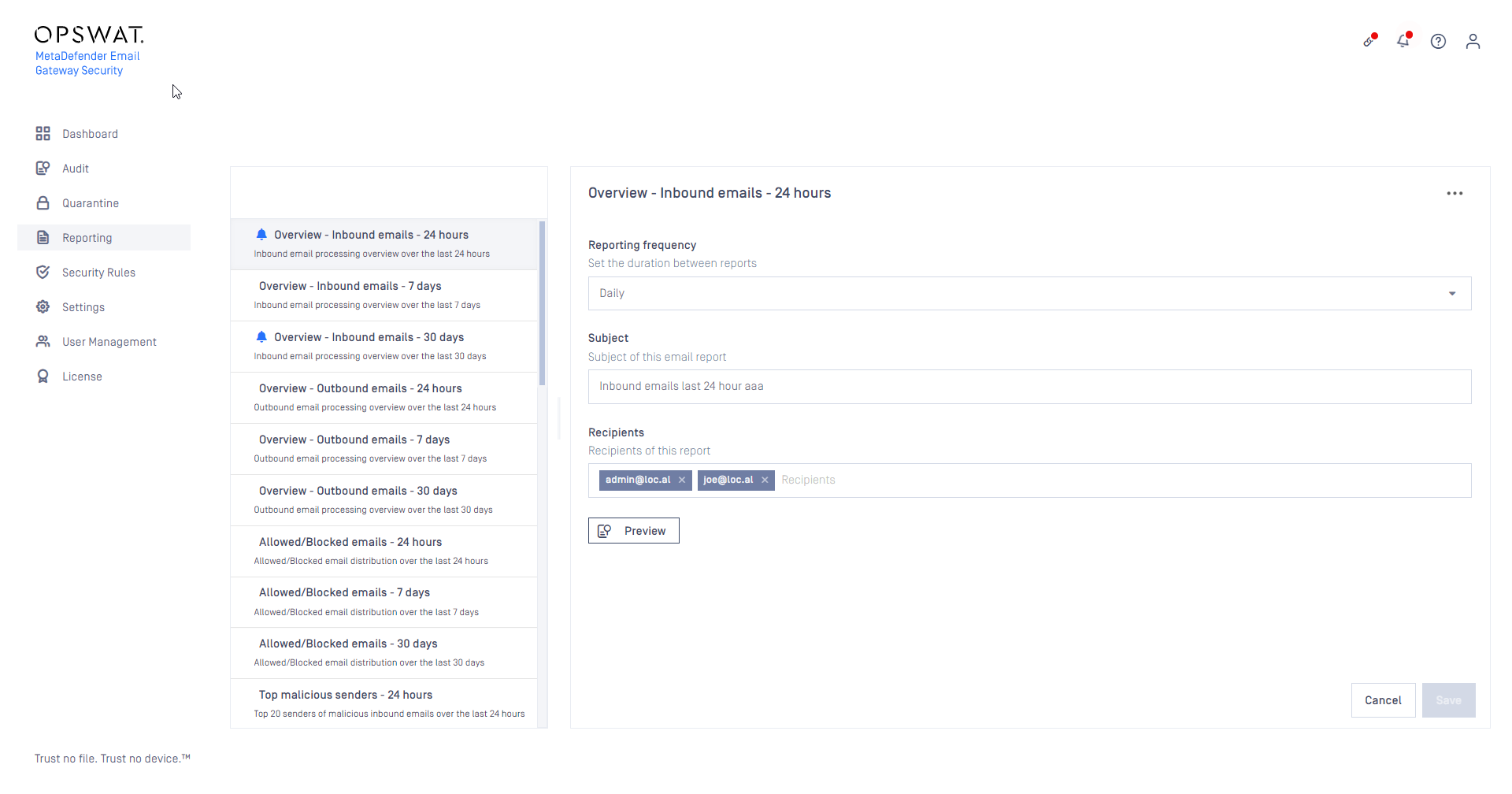
Send reports as scheduled emails
Email Gateway Security reports can now be delivered by the product attached to preconfigured report emails.
For details see Reporting and Scheduled report emails.
Changed
Enhanced password policy by default
Enhanced password complexity policy is enabled for new (with new installation or newly created) local type user directories by default.
For details see Local type user directories.
This change may give unexpected results for example with automated deployments and scripts that utilize the old, permissive default password policy.
Vault always impersonate recipient
Vault uploads impersonate the recipient for both inbound and outbound rules.
For details see Upload attachments.
Fixed
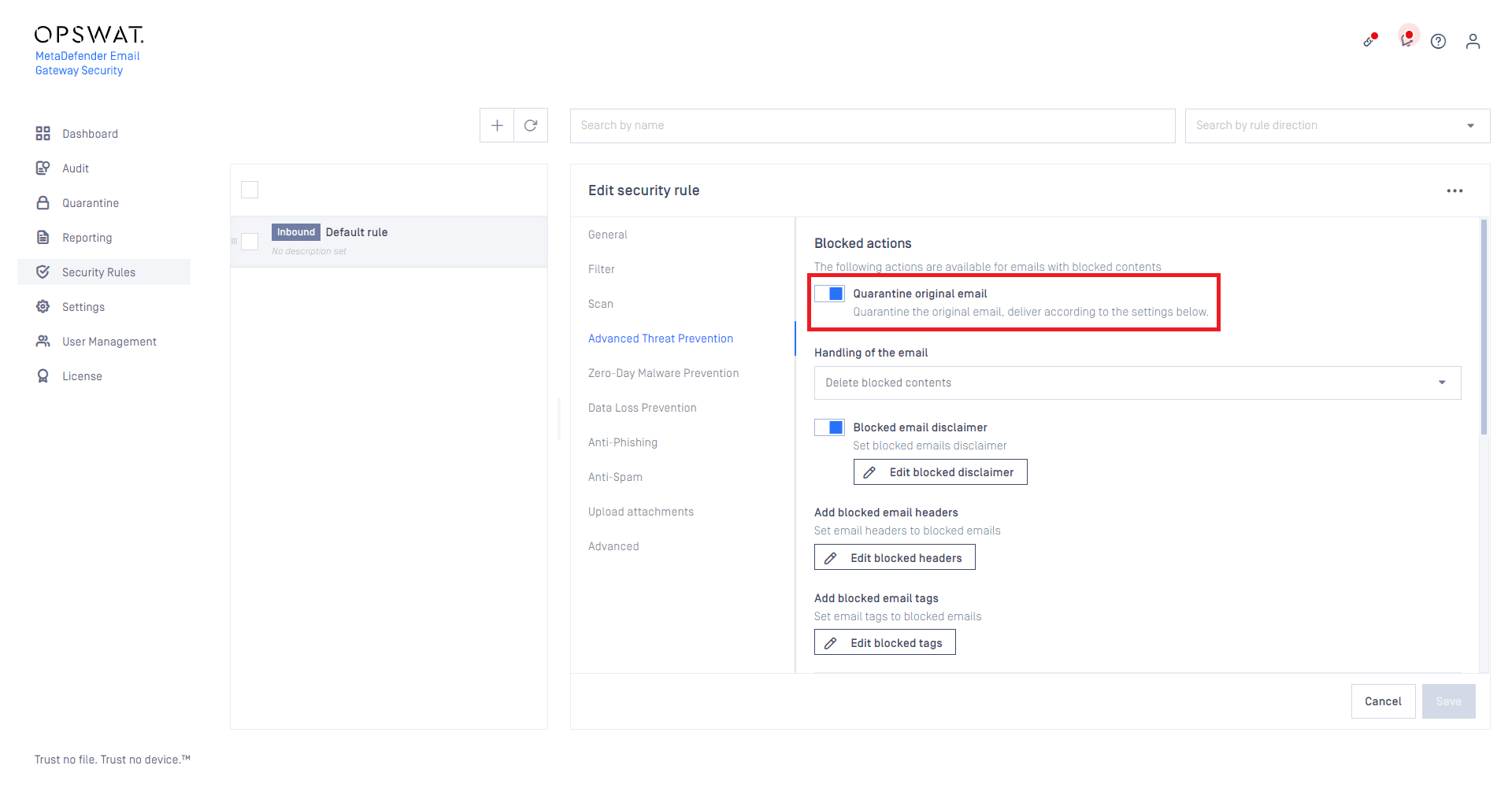
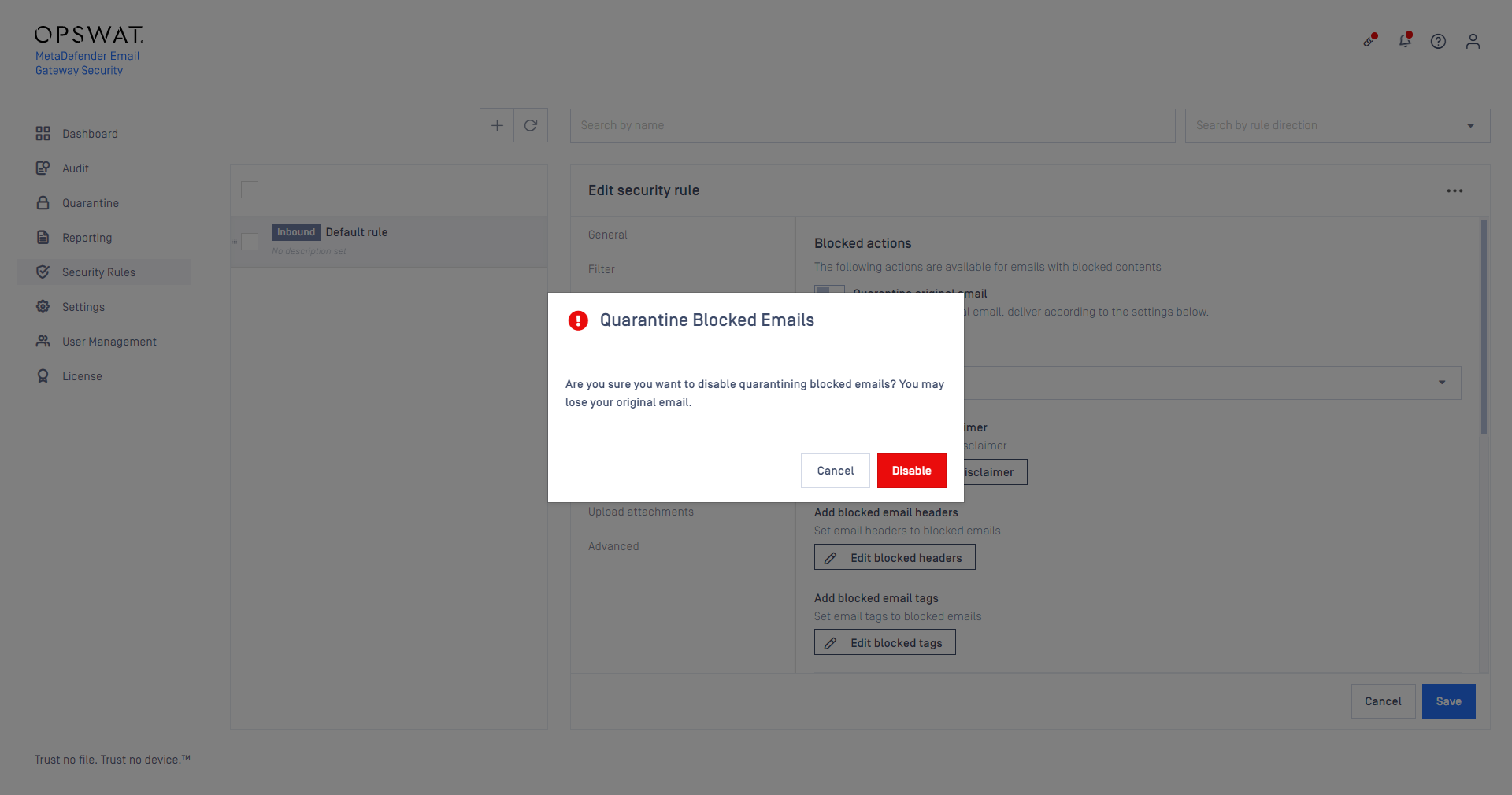
Quarantine disabled warning stuck
When Advanced Threat Prevention / Quarantine original email was disabled for a security rule, the warning notification was displayed for each consecutive visit of any security rules.
With the fix, this message comes only after disabling the quarantine feature.
Field should contain 32 characters
At the time of configuring Email Gateway Security instances in Central Management, the This field should contain 32 characters validation message was displayed for the CORE URI ADDRESS in certain cases.
Privilege escalation vulnerability
A privilege escalation vulnerability allowed non-administrator users to gain unauthorized privileges on the product to execute harmful actions via the user management configuration.
For details see https://nvd.nist.gov/vuln/detail/CVE-2022-32272.
Updated
| Component | Version |
|---|---|
| OpenSSL | 1.1.1o |

