The possible infrastructure vary depending on what are the AWS services for hosting MetaDefender Core and how the PostgreSQL database is provisioned
Options:
- EC2 Instances + AWS RDS
- EC2 Instances + PostgreSQL Pod
- AWS Fargate + PostgreSQL Pod
- AWS Fargate + AWS RDS
We offer a provisioning script that depending on the selection, we automatically provision the cluster for you and install the K8S components needed for MetaDefender Core service.
MetaDefender PostgreSQL database details
Recommendations
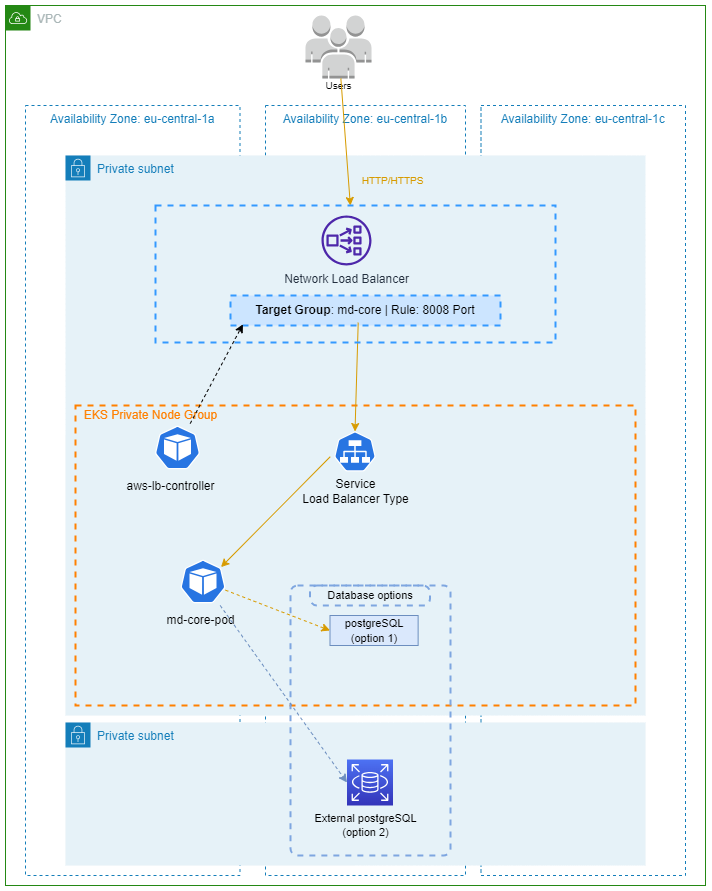
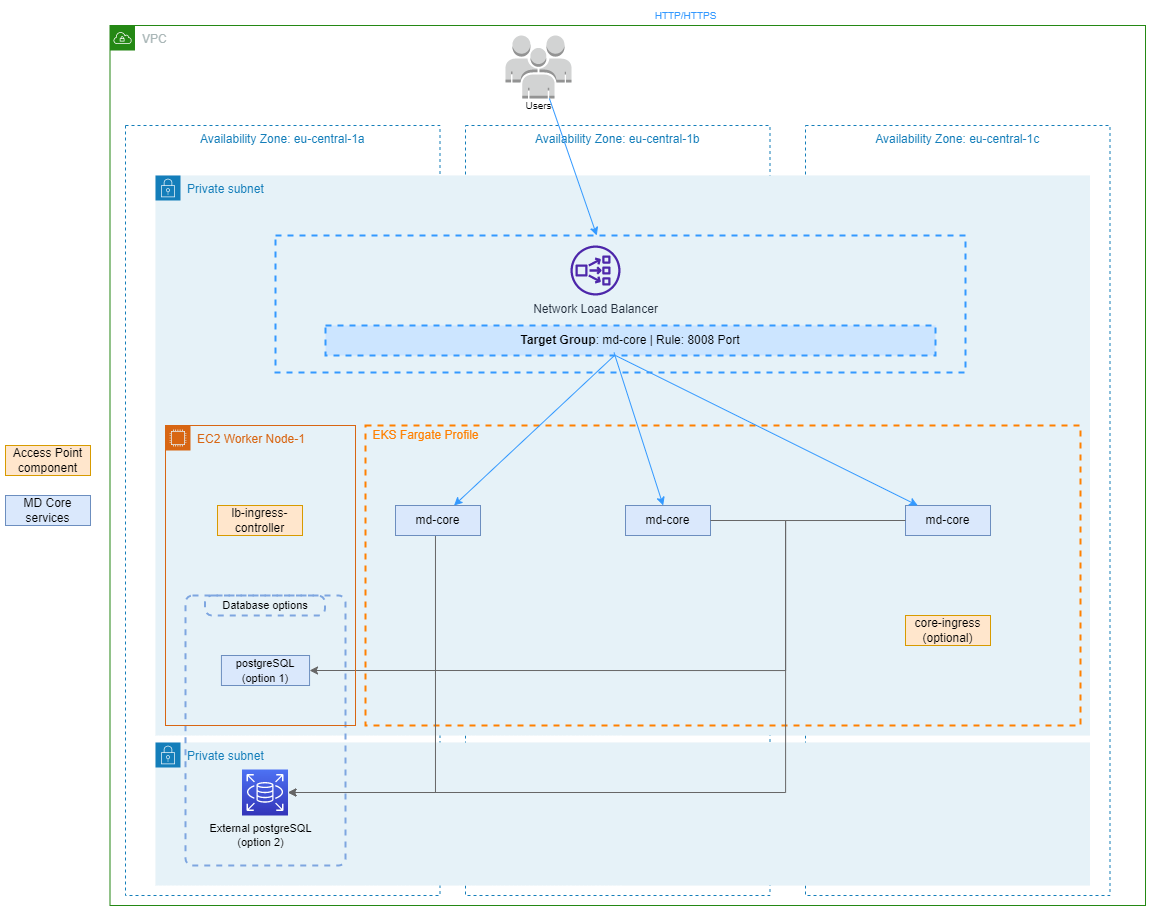
For running MetaDefender Core in a Kubernetes cluster we recommend to use, for production environments, an external database service for PostgreSQL. In case of AWS it is AWS RDS which the script will install and configure to be accessible from the cluster.
For non-production environments or for stateless use cases, we offer the option of installing the database within the cluster using a standard PostgreSQL image.
EC2 Instances + AWS RDS / PostgreSQL Pod
AWS Fargate + AWS RDS / PostgreSQL Pod
Resources Inventory
Access Management
| Service Type | Resource Name | Description |
|---|---|---|
| IAM Role | terraform-<CLUSTER_NAME>-cluster-ServiceRole | IAM Role for the cluster to assume the policies attached to it |
| IAM Role | terraform-<CLUSTER_NAME>-cluster-NodeInstanceRole | IAM Role for the nodes to assume the policies attached to it |
| IAM Policy | terraform-<CLUSTER_NAME>-cluster-PolicyELBPermissions | Policy for the EKS cluster to be able to get networking information for configurations |
| IAM Policy | terraform-<CLUSTER_NAME>-cluster-PolicyCloudWatchMetrics | Policy for the EKS cluster to be able to put metrics in CloudWatch |
| IAM Policy | terraform-<CLUSTER_NAME>-cluster-PolicyAWSLoadBalancerController | Policy for the nodes to be able to modify the load balancer settings |
| TLS Private Key | NA | Generates a secure private key stored in the Terraform state file |
| AWS Key Pair | <CLUSTER_NAME> | Upload to AWS the OpenSSH public key format to logging-in to the Worker Nodes. |
| EKS Cluster Auth config | terraform-<CLUSTER_NAME>-cluster- | Generates the kubeconfig file for accessing to the cluster with Kubectl |
Networking
| Service Type | Resource Name | Description |
|---|---|---|
| AWS Network Load Balancer | AWS Autogenerated | Network load balancer (Not created from terraform, created using eks_install_lb_controller.sh ) |
| VPC | terraform-<CLUSTER_NAME>-cluster/VPC | VPC for the whole architecture to be deployed in |
| 3 Public Subnets | terraform-<CLUSTER_NAME>-cluster/SubnetPublicX | 3 public subnets deployed in 3 different availability zones |
| 3 Private Subnets | terraform-<CLUSTER_NAME>-cluster/SubnetPrivateX | 3 private subnets deployed in 3 different availability zones |
| Internet Gateway | terraform-<CLUSTER_NAME>-cluster/InternetGateway | Internet Gateway service to allow the cluster to access to internet |
| Public NAT Gateway | terraform-<CLUSTER_NAME>-cluster/NATGateway | Public NAT gateway for the services in the private network to access to the public network and route the traffic to the internet gateway to access to internet |
| Elastic IP | terraform-<CLUSTER_NAME>-cluster/NATIP | Public IP attached to the NAT gateway for accessing to internet |
Security
| Service Type | Resource Name | Description |
|---|---|---|
| Security Group | terraform-<CLUSTER_NAME>-cluster-ClusterSharedNodeSecurityGroup | Communication between all nodes in the cluster |
| Security Group | terraform-<CLUSTER_NAME>-cluster-ControlPlaneSecurityGroup | Communication between the control plane and worker nodegroups |
| Security Group | terraform-<CLUSTER_NAME>-cluster-remoteAccess | Allow SSH access to the managed Worker Nodes in the Node Group |
| Security Group | terraform-<CLUSTER_NAME>-cluster-PostgreSQLSecurityGroup | Allow access to postgres db |
Compute
| Service Type | Resource Name | Description | Option |
|---|---|---|---|
| EKS Cluster | <CLUSTER_NAME> | EKS Cluster service for managing the Kubernetes Cluster | All |
| EKS Node Group | terraform-<CLUSTER_NAME>-nodegroup | Node group configuration of the Worker nodes of the EKS Cluster | EC2 Instances |
| RDS Instance | <CLUSTER_NAME>-postgres-db | PostgreSQL engine in RDS instance | AWS RDS |
| EKS Fargate Profile | fp-<CLUSTER_NAME> | Fargate Profile configuration | AWS Fargate |

