| Version | 5.14.2 |
|---|---|
| Release date | 28 May 2025 |
| Scope | This version introduces support for integration with MetaDefender Distributed Cluster v2.0, compatibility with Amazon Linux 2023, client identity tracking, and password decryption for multipart uploads, along with usability improvements and bug fixes. |
Making sure to check out the Known Limitations
New Features, Improvements and Enhancements
Integration with MetaDefender Distributed Cluster v2.0
Enables integration with a new product, MetaDefender Distributed Cluster v2.0, giving organizations exclusive benefits:
- High availability: Distributed architecture ensures continuous inspection, even during instance-level outages or maintenance.
- Fault tolerance: Isolate failures and support automatic recovery, preserving uptime and service continuity.
- Load distribution across MetaDefender Core instances: Share file scanning tasks across multiple instances, eliminating performance bottlenecks.
- Parallel archive file handling: Extract and distribute archive contents across Core instances, reducing scan time for large files and enabling resumption of interrupted processing.
- Elastic scalability: Easy to add more instances as file volumes grow, scaling capacity seamlessly to meet organizational demand.
- Centralized orchestration: Manage all MetaDefender Core instances and API Gateways from a single Control Center web console. Provide a zero-downtime upgrade mechanism with just a few simple operations.
More details about this new product at MetaDefender Distributed Cluster Overview.
New Operating System Support: Amazon Linux 2023
This release introduces support for Amazon Linux 2023 across most engines. The majority of engines are now compatible and operational on this new operating system.
Few engines still require additional time for full compatibility with Amazon Linux 2023:
- NANOAV
- File-based Vulnerability Assessment
- RAR compression of Archive Compression
Further updates will be provided in future releases.
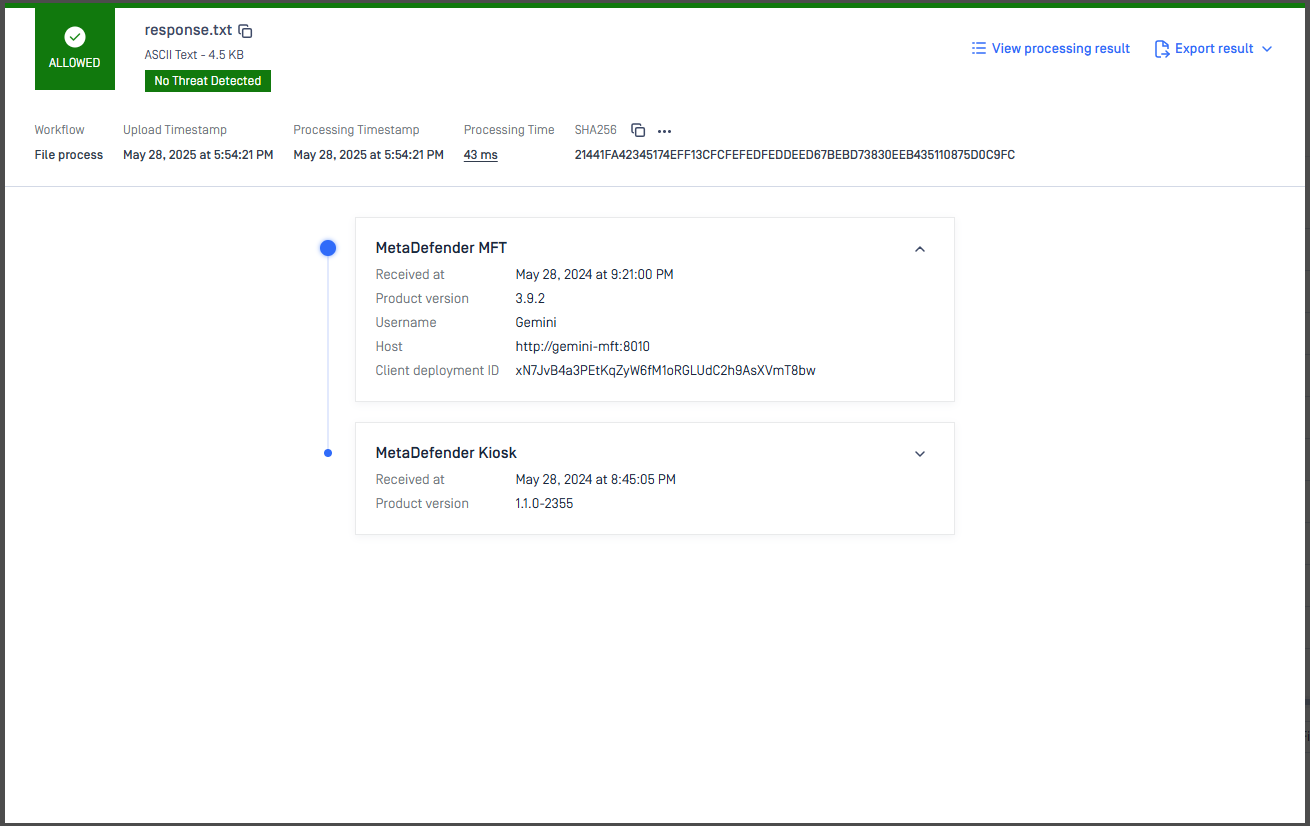
Client Identity Tracking
This release introduces support for sending client identity information with file scan requests into MetaDefender Core via a new header client-identity, enhancing visibility into the scan request lifecycle.
This optional header captures details provided by the clients a scan request passes through (e.g., MetaDefender KIOSK → MetaDefender MFT → MetaDefender Core), including:
- Client name
- Client host
- Username
- Client's deployment ID
- Received timestamp at client
- Client product version
All the following methods support this header: asynchronous mode, synchronous mode, local scan, scan from link, batch scan, multi-part uploading.
More details at:
- GET - Fetch Analysis ResultAPI
- GET - Fetch Analysis Result By HashAPI
- GET - Status of Batch AnalysisAPI
- POST - Analyze File (Asynchronous mode)API
- POST - Analyze File (Synchronous mode)API
- POST - Initiate BatchAPI
- POST - Create multipart uploading sessionAPI
The client identity details are accessible through:
- MetaDefender Core web console: View detailed scan request information directly in the user interface.
- JSON Processing Result: Client identity data is included in the processing result output.
- My OPSWAT Central Management (MOCM): MetaDefender Core forwards client identity information as part of the scan report to MOCM for centralized management and reporting.
Archive Password Support for Multi-part Uploading
Starting with version 5.14.2, MetaDefender Core introduces support for archive password handling in multipart upload APIs, enhancing functionality for processing password-protected archives.
The passwords are transmitted via header archivepwd and are secured through at-rest encryption.
More details at POST - Create multipart uploading sessionAPI.
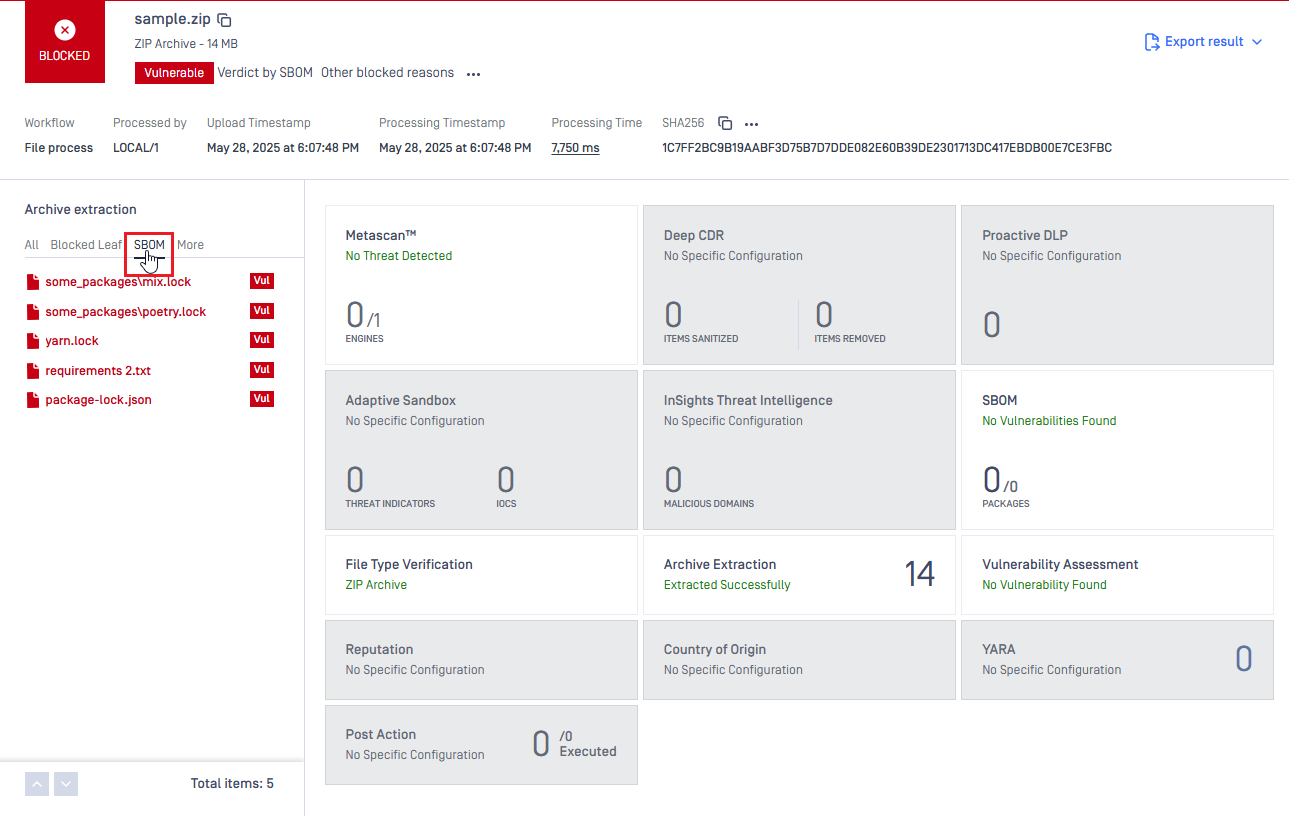
SBOM Package Filter for Archive Files and Batch
A new SBOM filter functionality has been added to the Scan Results page. This feature enables users to efficiently filter and view results for nested files in archives and batch-processed files containing SBOM package information.
Usability Enhancements & Changes
- Setting "Block files if the process fails or times out" under Deep CDR workflow now flags a result as Blocked even when sanitized version of a file cannot be added to storage successfully.
- Ensure log rotation has unique filename and no remaining file.
Technology Integration Enhancements
- Enable engines to display hyperlink within its result details.
- Future versions of Archive Extraction engine will move away from the ID format
7z_and provide a new formatextraction_. Since this version of MetaDefender Core, the new format is supported along with the old one.
Security Enhancements
Upgraded libraries for vulnerability fixes:
- NGINX v1.26.3
- Libxml2 v2.13.8
Improved API endpoints' validation.
Replaced deprecated functions of 3rd libraries.
Bug Fixes
- Fixed an issue that prevented access to web console after OS reboot. This issue happened with standalone mode and a remote PostgreSQL. When the issue happened, an error "Can't create connection" was found in log.
- Fixed an issue that stopped email sending after the machine lost internet connection.
- Fixed an issue that blocked modification of webhook configuration after enrolled into My OPSWAT Central Management.
- Fixed an issue that failed enrollment via ignition file.
- Fixed an issue that omitted blocked reason "Extraction Failed" when a temporary extracted file was absent.
- Fixed an issue that incorrectly disabled Country of Origin engine after importing a configuration with "Allowlist by vendor" setting enabled.
Known Limitations
| Details | |
|---|---|
| The 'Proxy server requires password' setting cannot be disabled once it has been enabled | This issue has been resolved in version 5.14.2. In version 5.14.1, there was an issue that prevented disabling the |
| Database connection failure occurred in a specific circumstance after upgrading to version 5.11.0 | This issue has been resolved in version 5.11.1. This issue does not affect all cases when upgrading to version 5.11.0. After applying the authentication method
We prepare a Knowledge Base (KB) for troubleshooting the issue and bringing the system back online: How to Troubleshoot an Error related to Connection to Database Failing after an Upgrade to v5.11.0? The issue will not occur in the following scenarios:
|
| Archive compression may fail with very large archive files that contain a large number of subfiles | This issue has been addressed in MetaDefender Core v5.14.0. MetaDefender Core has a limitation when compressing very large archive files that contain a high number of subfiles. In our test scenario, it failed when processing an archive with 300,000 or more subfiles. |
| Reuse processing result by hash might be slow in high-load situations | This issue has been resolved in version 5.10.1. Since its introduction in version 5.8.0, this feature has helped improve overall performance and reduce significant load when processing similar files. However, we have realized this feature might run slowly in high-load scenarios against large database sizes. |
| Temporary files in the resource folder may not be properly cleaned up if the Archive Extraction engine crashes | Starting from MetaDefender Core version 5.10.1, if the Archive Extraction engine crashes, temporary files from specific extraction transactions may not be properly cleaned up. However, this issue is relatively rare. |
| Reject importing non-empty required_engines setting in containerized environments | This issue occurs only in containerized environments. If the config zip file includes non-empty required_engines setting, MetaDefender Core will reject the import. Workaround:
|
| The Engine Update feature may not work as expected in certain environments | We have observed that the Engine Update feature may not work properly in an environment protected by a [Palo Alto firewall](Palo Alto firewall). In the log file, you might find the error message ' If upgrading to the latest version of MetaDefender Core does not solve the issue, please consider setting up MetaDefender Update Downloader product. This product is responsible for downloading engines, and MetaDefender Core will retrieve and update its engines from there. |
| Performance degradation when processing large archive files | This issue has been resolved in MetaDefender Core version 5.5.0 and the Archive Extraction engine version 6.2.1.
|
| Stability issues on Red Hat / CentOS systems with kernel version 372.13 | MetaDefender Core version 5.2.1 or later may not function correctly with Red Hat or CentOS operating systems that use kernel 372.13. Red Hat is addressing the kernel issues. Please try upgrading to kernel version 372.26. |
| PostgreSQL and MetaDefender Core services cannot initialize in certain containerized environments | This issue was addressed in MetaDefender Core v5.11.1 In a containerized environment, MetaDefender Core version 5.2.0 or newer may work properly when:
Workarounds for older versions:
|
| MetaDefender Core's NGINX web server will not start if weak cipher suites are used for HTTPS | On MetaDefender Core version 5.2.0 and later, OpenSSL 1.x has been replaced by OpenSSL 3.x within the product and its dependencies, including PostgreSQL and NGINX, to enhance security and address known vulnerabilities in OpenSSL 1.x. However, NGINX's implementation of OpenSSL 3.x in MetaDefender Core enforces strong encryption by rejecting all weak cipher suites. It only accepts "HIGH" encryption cipher suites as defined by OpenSSL https://www.openssl.org/docs/man1.1.1/man1/ciphers.html. This means ciphers based on MD5 and SHA1 hashing are no longer supported. Consequently, if you previously configured MetaDefender Core for HTTPS connections using a weak SSL cipher with your certificate, the service will not start due to NGINX's OpenSSL 3.x security enforcement. To prevent and remediate the issue before upgrading MetaDefender Core, please refer to the following resources: HTTPS Failure on MetaDefender Core 5.2.0 (or newer) |

