| Version | 5.13.0 |
|---|---|
| Release date | 18 December 2024 |
| Scope | A major version focused on new features, enhancements and stability bug fixes. |
Making sure to check out the Known Limitations
OPSWAT will discontinue support for CentOS 7 and RHEL 7 after December 2024 in MetaDefender Core and its associated engines.
If you need some more time to transition from legacy OS, refer to this instruction Lock Your Engine and Plan for Migration.
New Features, Improvements and Enhancements
| Details | |
|---|---|
| New OS support: Rocky Linux 9 | We are now introducing Rocky Linux 9.4 support as a replacement for CentOS 7 starting from this version. We also provide a new Docker image based on official Rocky Linux repository. You can try it here: MetaDefender Core Rocky Linux image and Rocky Linux for non-root image. |
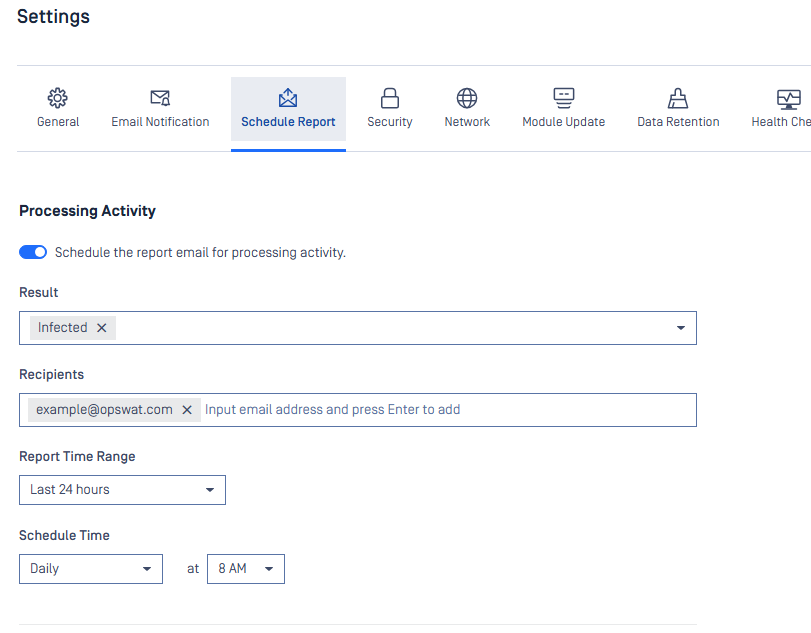
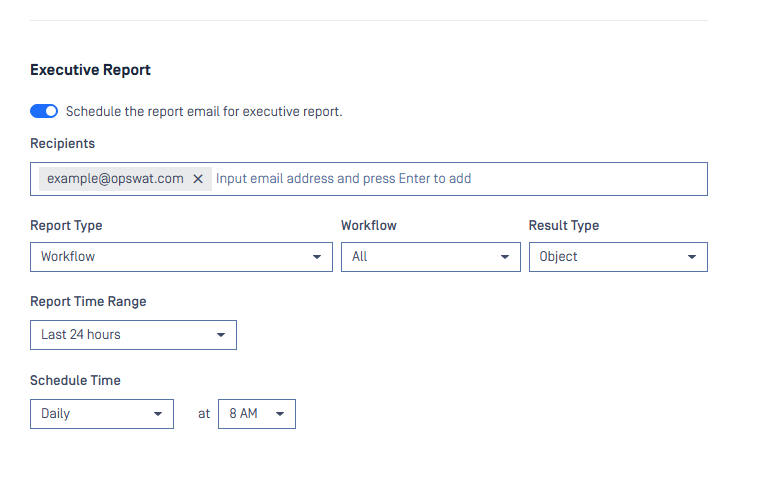
| Report scheduling | MetaDefender Core provides a new feature that enables Administrators to schedule not only when executive report and processing history report are sent but also set recurring schedules for automated delivery. This feature goes with abilities to specify email recipients, apply filters to tailor the data and define precise time range.
|
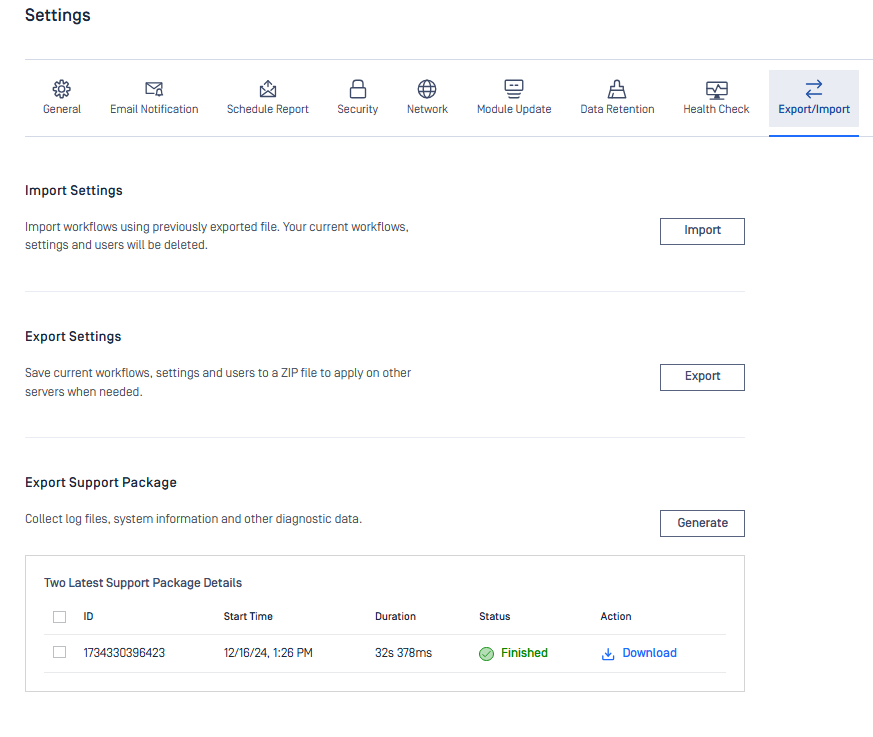
| Generate support package on web console | Administrators now can directly generate and download support packages right on web console.
|
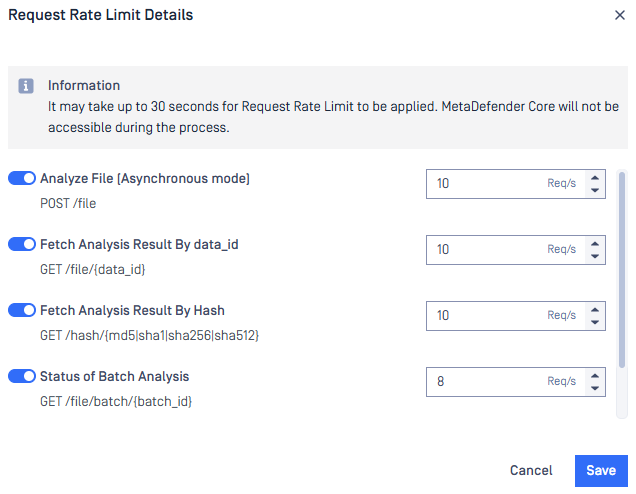
| Advanced rate limiting configuration via web console | Administrators can now configure rate limiting for various REST APIs directly through the web console. For more details, refer to Request rate limit configuration and Request rate limit test scenarios.
|
| Syslog configuration via REST API | Administrators now can configure and setup syslog via REST API. Document: |
| Ability to download summarized user list | MetaDefender Core introduces an ability for Administrators to download a summary list of users and groups present on the product. You can find the Export button in User Management which generates a CSV file listing all the users and groups' information. |
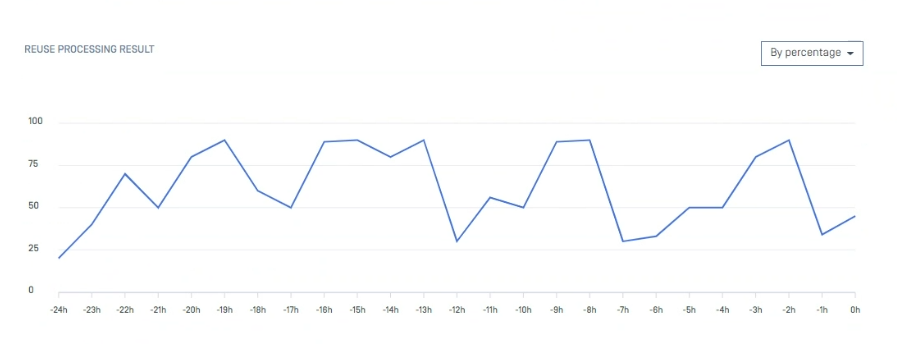
| Executive Report | New chart and statistics to display how many percentages/files are reused by hash.
|
| Tool to hide specific data from support package | Provides an ability to hide sensitive data from logs, support package, which may contain information such as IPv4, IPv6, MAC address and file path. For instruction, refer to How to Create Support Package? and try the new parameter |
| Support CIS level 1 | MetaDefender Core supports CIS Level 1 for Ubuntu 22.04 and RHEL 9. For more details, refer to CIS Level 1 Guidelines. |
| PostgreSQL v16 support (remotely) | MetaDefender Core starts supporting remote PostgreSQL v16. The product does not perform any version upgrade on customer's remote PostgreSQL. Note: The bundled PostgreSQL version is v14.15 in this release. |
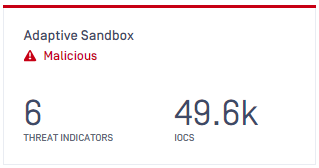
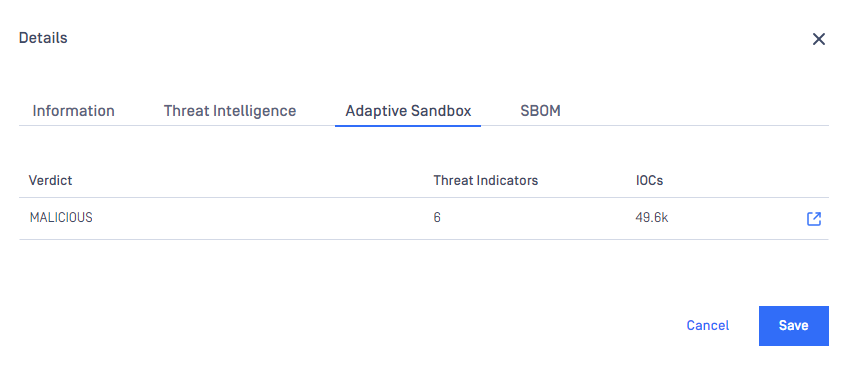
| More detailed Adaptive Sandbox's scan result | For files scanned with Adaptive Sandbox, result display now provides more details as well as adding informative records in "Quarantine" feature.
|
| Usability enhancements / changes |
|
| Performance enhancements |
|
| Security improvements |
|
| Engine integration |
|
| Docker enhancements |
|
| Logging enhancements |
|
| UI updates |
|
Bug Fixes
| Details | |
|---|---|
| Fixes on product stability issues |
|
| Other minor bug fixes | Implemented UI enhancements and resolved minor bugs. |
Known Limitations
| Details | |
|---|---|
| Database connection failure occurred in a specific circumstance after upgrading to version 5.11.0 | This issue has been resolved in version 5.11.1. This issue does not affect all cases when upgrading to version 5.11.0. After applying the authentication method
We prepare a Knowledge Base (KB) for troubleshooting the issue and bringing the system back online: How to Troubleshoot an Error related to Connection to Database Failing after an Upgrade to v5.11.0? The issue will not occur in the following scenarios:
|
| Reuse processing result by hash might be slow in high-load situations | This issue has been resolved in version 5.10.1. Since its introduction in version 5.8.0, this feature has helped improve overall performance and reduce significant load when processing similar files. However, we have realized this feature might run slowly in high-load scenarios against large database sizes. |
| Temporary files in the resource folder may not be properly cleaned up if the Archive Extraction engine crashes | Starting from MetaDefender Core version 5.10.1, if the Archive Extraction engine crashes, temporary files from specific extraction transactions may not be properly cleaned up. However, this issue is relatively rare. |
| Reject importing non-empty required_engines setting in containerized environments | This issue occurs only in containerized environments. If the config zip file includes non-empty required_engines setting, MetaDefender Core will reject the import. Workaround:
|
| Button "Revert to Default" in Workflow Rule might not work as expected | This issue has been resolved in version 5.6.0. When modifying settings in Workflow Rule, the ' |
| The Engine Update feature may not work as expected in certain environments | We have observed that the Engine Update feature may not work properly in an environment protected by a [Palo Alto firewall](Palo Alto firewall). In the log file, you might find the error message ' If upgrading to the latest version of MetaDefender Core does not solve the issue, please consider setting up MetaDefender Update Downloader product. This product is responsible for downloading engines, and MetaDefender Core will retrieve and update its engines from there. |
| UI inconvenience on small resolution screens | This issue has been resolved in version 5.5.1. MetaDefender Core version 5.5.0 introduces significant changes to support UI accessibility. However, this leads to an inconvenient issue when displaying Workflow Rule on small or zoomed-in resolution screens. Some tabs at the bottom of the list may not be displayed properly. Workaround: Try zooming out a little bit on the browser. |
| Performance degradation when processing large archive files | This issue has been resolved in MetaDefender Core version 5.5.0 and the Archive Extraction engine version 6.2.1.
|
| Stability issue when encountering malformed data created by the FileType engine | This issue has been resolved in version 5.4.1. The FileType engine version 6.0.2 may generate malformed data, which can negatively impact MetaDefender Core version 5.4.0 or older when written to the PostgreSQL database:
If you experience similar issues, follow these troubleshooting steps to resolve the problem: Rectify malformed FileType data in PostgreSQL database |
| Stability issues on Red Hat / CentOS systems with kernel version 372.13 | MetaDefender Core version 5.2.1 or later may not function correctly with Red Hat or CentOS operating systems that use kernel 372.13. Red Hat is addressing the kernel issues. Please try upgrading to kernel version 372.26. |
| PostgreSQL and MetaDefender Core services cannot initialize in certain containerized environments | This issue was addressed in MetaDefender Core v5.11.1 In a containerized environment, MetaDefender Core version 5.2.0 or newer may work properly when:
Workarounds for older versions:
|
| MetaDefender Core's NGINX web server will not start if weak cipher suites are used for HTTPS | On MetaDefender Core version 5.2.0 and later, OpenSSL 1.x has been replaced by OpenSSL 3.x within the product and its dependencies, including PostgreSQL and NGINX, to enhance security and address known vulnerabilities in OpenSSL 1.x. However, NGINX's implementation of OpenSSL 3.x in MetaDefender Core enforces strong encryption by rejecting all weak cipher suites. It only accepts "HIGH" encryption cipher suites as defined by OpenSSL https://www.openssl.org/docs/man1.1.1/man1/ciphers.html. This means ciphers based on MD5 and SHA1 hashing are no longer supported. Consequently, if you previously configured MetaDefender Core for HTTPS connections using a weak SSL cipher with your certificate, the service will not start due to NGINX's OpenSSL 3.x security enforcement. To prevent and remediate the issue before upgrading MetaDefender Core, please refer to the following resources: HTTPS Failure on MetaDefender Core 5.2.0 (or newer) |