What's new
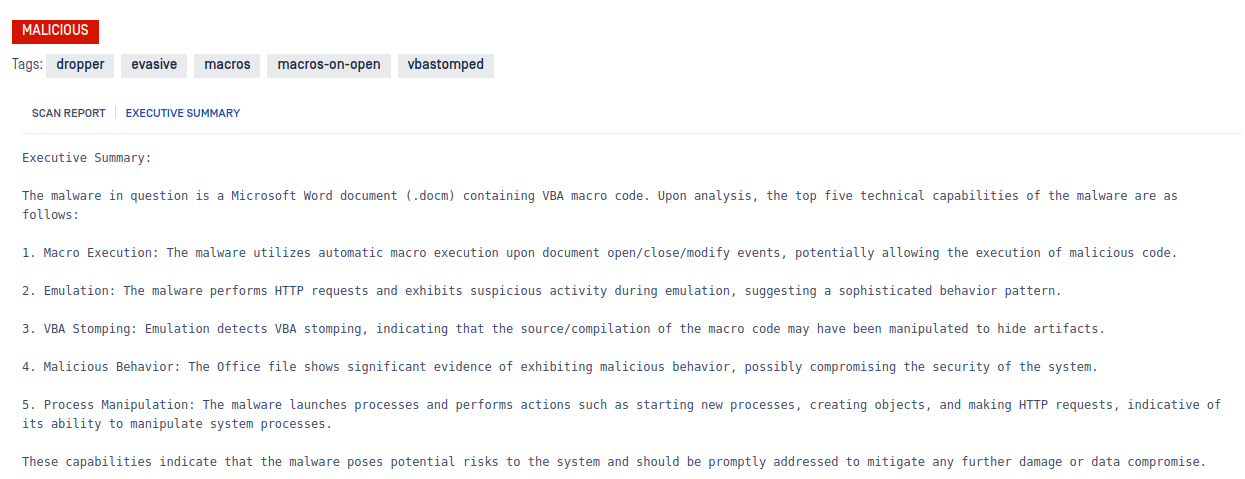
We are excited to announce the release of MetaDefender Aether for Core v3.0.0. With this update, users can now enable dynamic file analysis and behavioral threat detection directly within their Core environment—no additional infrastructure required.
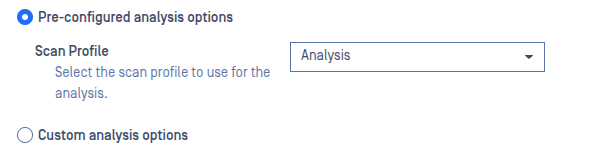
- Simplified and Enhanced OSINT Lookups - OSINT lookups were simplified and local reputation results are now visible in the OSINT results as OFFLINE_REPUTATION
- Verdict Renaming – Updated verdicts to provide clearer guidance on how to interpret analysis results and take appropriate actions based on potential threat levels
- E-PUB support - Added support for EPUB files, to ensure broader compatibility with widely used e‑reading formats.
- IOC Skip List Migration - Moved the IOC skip list (allow/blocklist) from the local application database to the separated detection database package to enable frequent updates
- Core Component Hardening - Hardened core components with additional security safeguards to strengthen the overall defense posture.
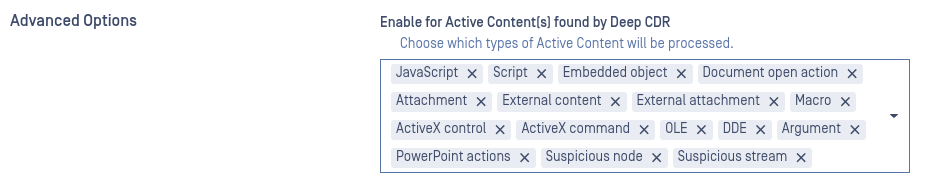
- QR Code Detection Improvements - Improved to allow the scanning of rendered images in documents and emails
- Batch File-Type Detection - Enhanced to improve accuracy across complex payloads.
Bug Fixes
- BAT Script Classification Fix - Corrected file-type misclassification for obfuscated BAT scripts, eliminating related false positives.
Threat Detection 2.0.0 Release Notes
MetaDefender Aether for Core supports independent updates to detection logic and threat intelligence, enabling faster deployment of new protections and a more rapid response to emerging threats. The following updates have been delivered over the past several months.
What's new
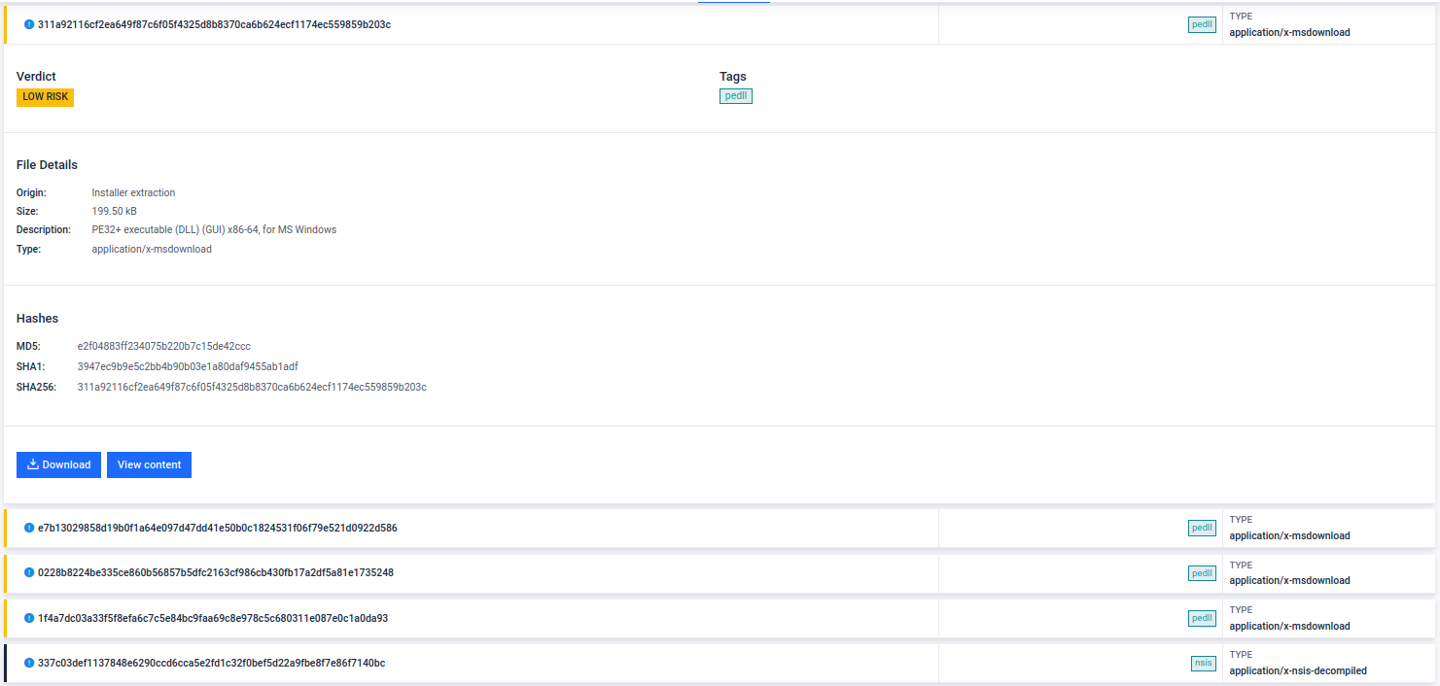
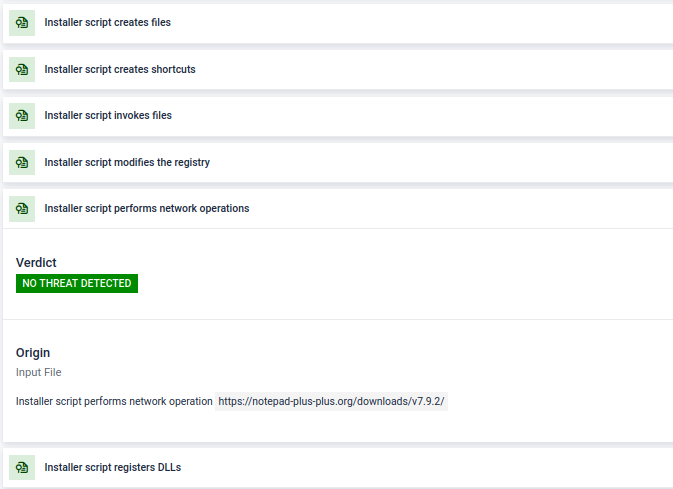
- Significant Enhancements to PE Installer Analysis - Added deep static extraction and analysis for Windows installers: NSIS, Inno, InstallShield, Advanced Installer, Wise, WiX, InstallAnywhere, and Actual Installer. It now extracts prioritized embedded files, analyzes installer scripts, and scores custom installers heuristically.
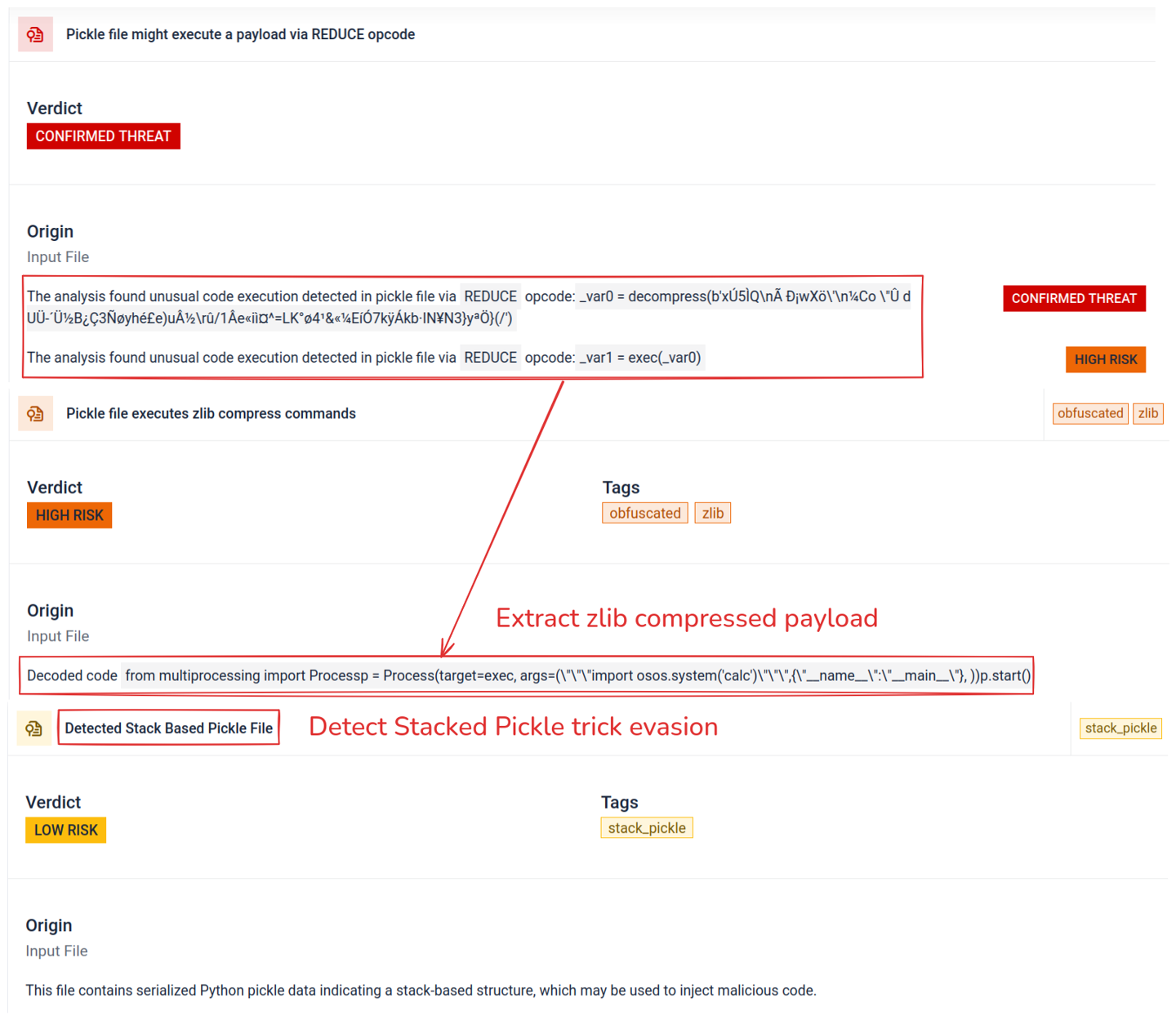
- AI / ML Model Security Scanning - Introduced security analysis for Machine Learning models, including multi-serialization parsing and deep static inspection to detect hidden malicious payloads before they impact AI workflows.
- Zero-Day Exploit Detection - Added detection for recent Windows Explorer LNK vulnerabilities (CVE-2025-50154, CVE-2025-59214) that leak NTLM credentials without user interaction. Also, introduced detection for critical XXE exploitation in Apache Tika (CVE-2025-66516).
- Phishing Campaign Intelligence - Introduced indicators for seasonal / opportunistic lures (holidays, global events). Improves campaign clustering and early phishing detection.
- Invisible String Obfuscation Detection - It now detects GlassWorm-style obfuscation techniques by identifying invisible and deceptive code constructs used to evade analysis and enable silent execution. This includes detection of homoglyph characters, PUA (Private Use Area) Unicode characters, and hidden or non-printable whitespace that visually alters code without changing execution.
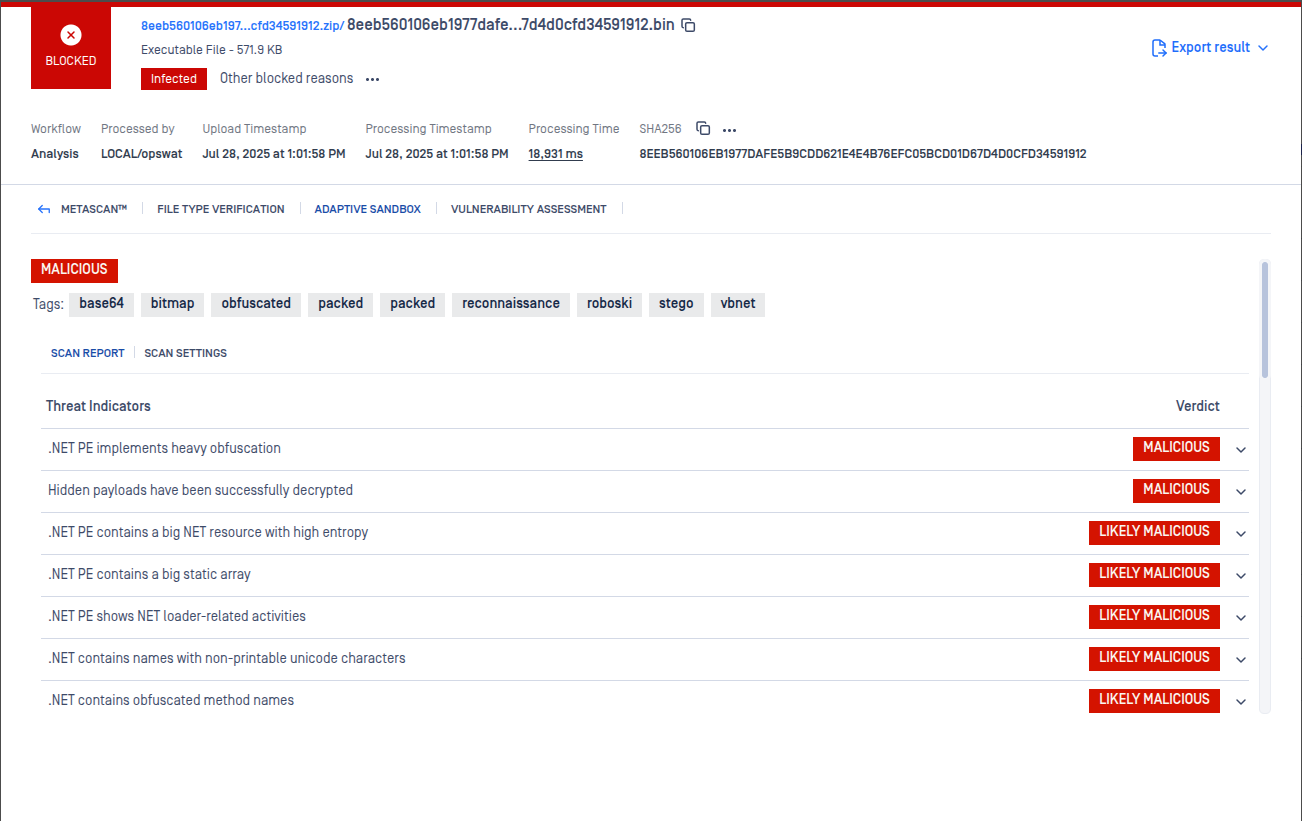
- Advanced Evasion Technique Detection - Expanded detection for techniques used to evade automated analysis, including meaningless infinite loops, abuse of password-protected in-house macros, .NET PE constant protection and control-flow obfuscation, and deobfuscation of hexadecimal-encoded JavaScript.
- Expanded File Type & Archive Coverage - Added support for VSIX files, CRX archives, and improved archive file filtering and prioritization.
- HTML Threats & Web Payload Extraction - It now extracts hidden downloadable payloads from HTML href data blobs and improves detection for abused HTML capabilities (e.g., disabled context menu).
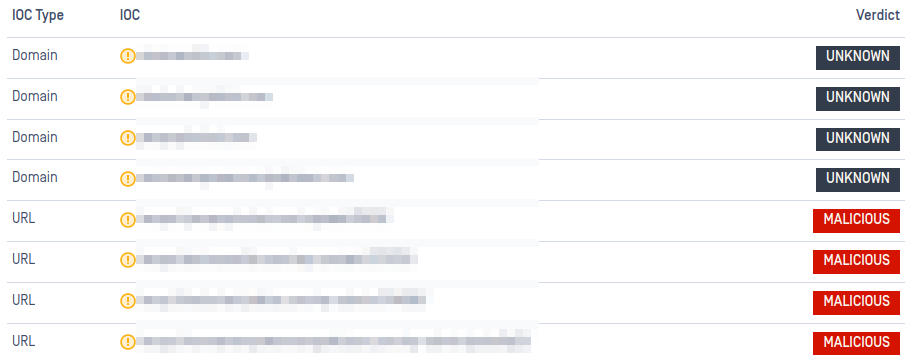
- Detection of IP logging and tracking services - Added indicators to flag the presence of IP-logging URLs that may be abused by attackers to identify victim location, apply geofencing, or support other reconnaissance and targeting activities, improving visibility into early-stage attack workflows.
Improvements
- Encrypted Documents - Enhanced decryption for protected Office and PDF documents by introducing a multi-step password recovery with fallback logic for phishing-delivered encrypted files.
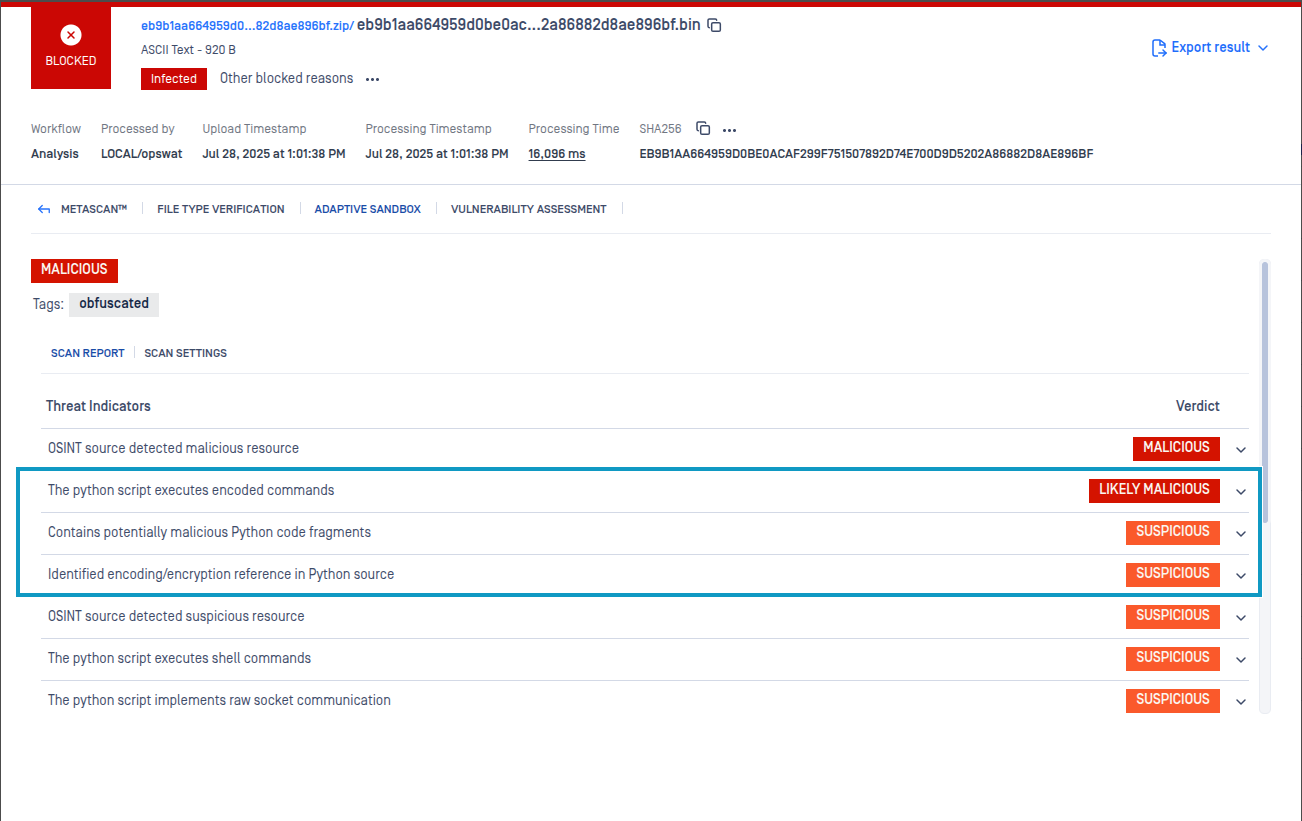
- Base64-Encoded Payload Extraction - Added base64 decoding for dynamically created files during emulation. This improves visibility into malware that reconstructs payloads at runtime to bypass static analysis and hide secondary stages until execution.
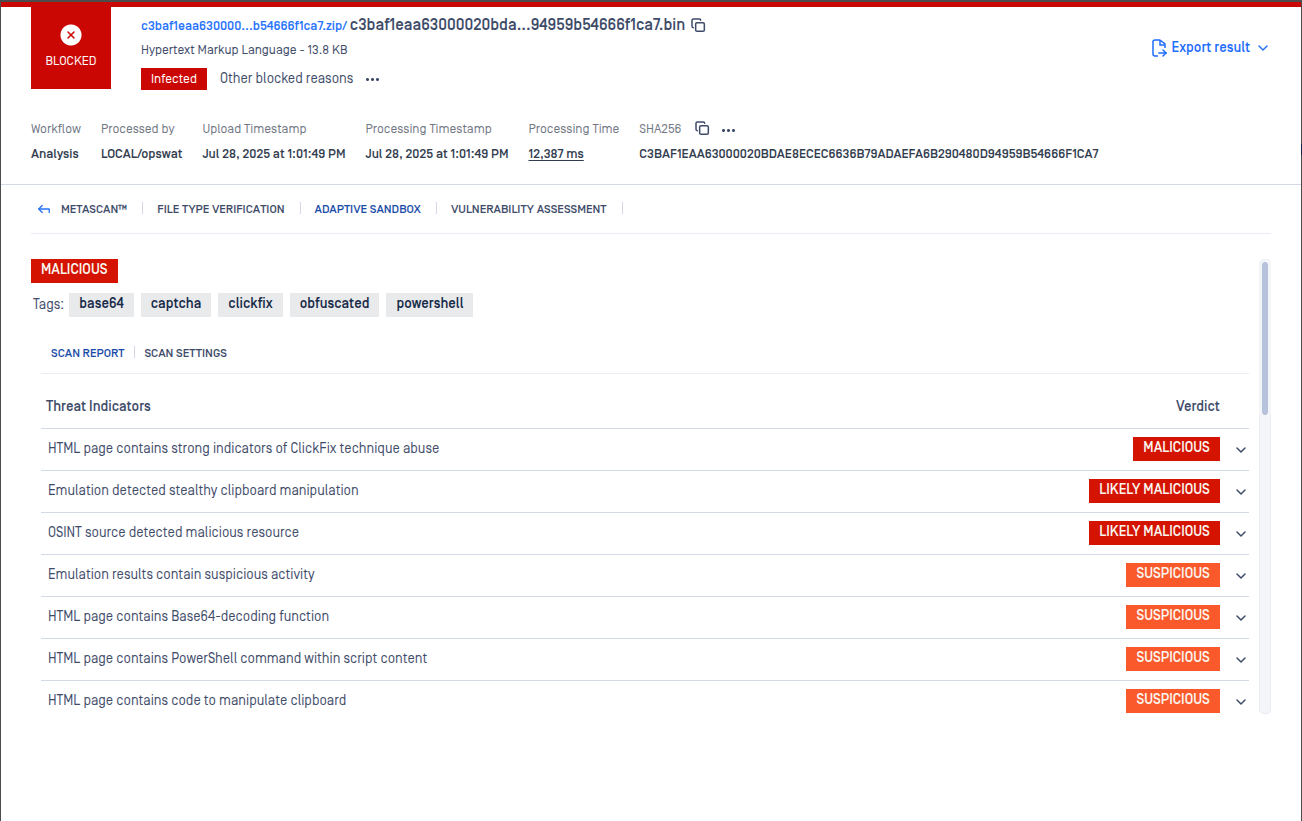
- ClickFix Variant Detection - Improved detection for new ClickFix variants that abuse hex-encoded URLs and msiexec execution.
- Email & Phishing Analysis Accuracy - Improved EML parsing to correctly associate images with embedded URLs, support text-based attachments, and enhance call-to-action detection across multiple languages.
- Multi-Stage Infection Chain Visibility - Improved emulation triggering for downloaded scripts, enabling full infection chain analysis when payloads are fetched from an external resource.
- Better Detection Precision & URL Noise Extraction Reduction - Reduced false positives by refining encryption-related indicators shared by malware and legitimate installers, adapting string-detection heuristics for PE files.
Bug Fixes
- MSI Extraction Reliability - Fixed multiple issues causing missing or incomplete payload extraction from MSI installers.
- URL Redirection & Download Chain Handling - Fixed missing redirected URLs, deduplicated download tasks, and added detection for delayed redirections.
- Indicator Stability & Engine Robustness - Fixed unintended indicator triggers (including PDF-related), skipped unnecessary PE disassembly when packers are detected, and resolved multiple internal indicator bugs.
- Duplicate Tags - Tags originating from multiple sources were being shown repeatedly in the UI. The fix ensures that tags are properly deduplicated so each one appears only once.
|