Title
Create new category
Edit page index title
Edit category
Edit link
Setup for RadSec Clients without RadSec capability
RADIUS NAC Switch/Controller/AP Integration Scripts
The following scripts are provided to integrate Switches/Controllers and APs with the RADIUS NAC. In order for this integration to function, the steps on the Network Integration page must be completed.
Supported Vendors
- Unifi Wireless Integration
- Cisco Wired Integration
1. Unifi Wireless Integration
Controller Configuration
Navigate to Settings > Profiles > RADIUS and click Create New RADIUS Profile.
Under “CREATE NEW RADIUS PROFILE” give the profile a name, select and Enable Wired and Enable Wireless. Under RADIUS AUTH SERVERS add the IP address of the Radsec Proxy for port 1812 and enter the shared secret (currently we use “radsec” as shared secret). Under ACCOUNTING select Enable Accounting, Enable Interim Update and set the Interim Update Interval to 300 (5 minutes). Finally, add the IP address of the Radsec Proxy under RADIUS Accounting Servers, set the port to 1813 and enter the same shared secret entered for the authentication server.
Navigate to Wireless Network > Wireless Networks and select Create New Wireless Network.
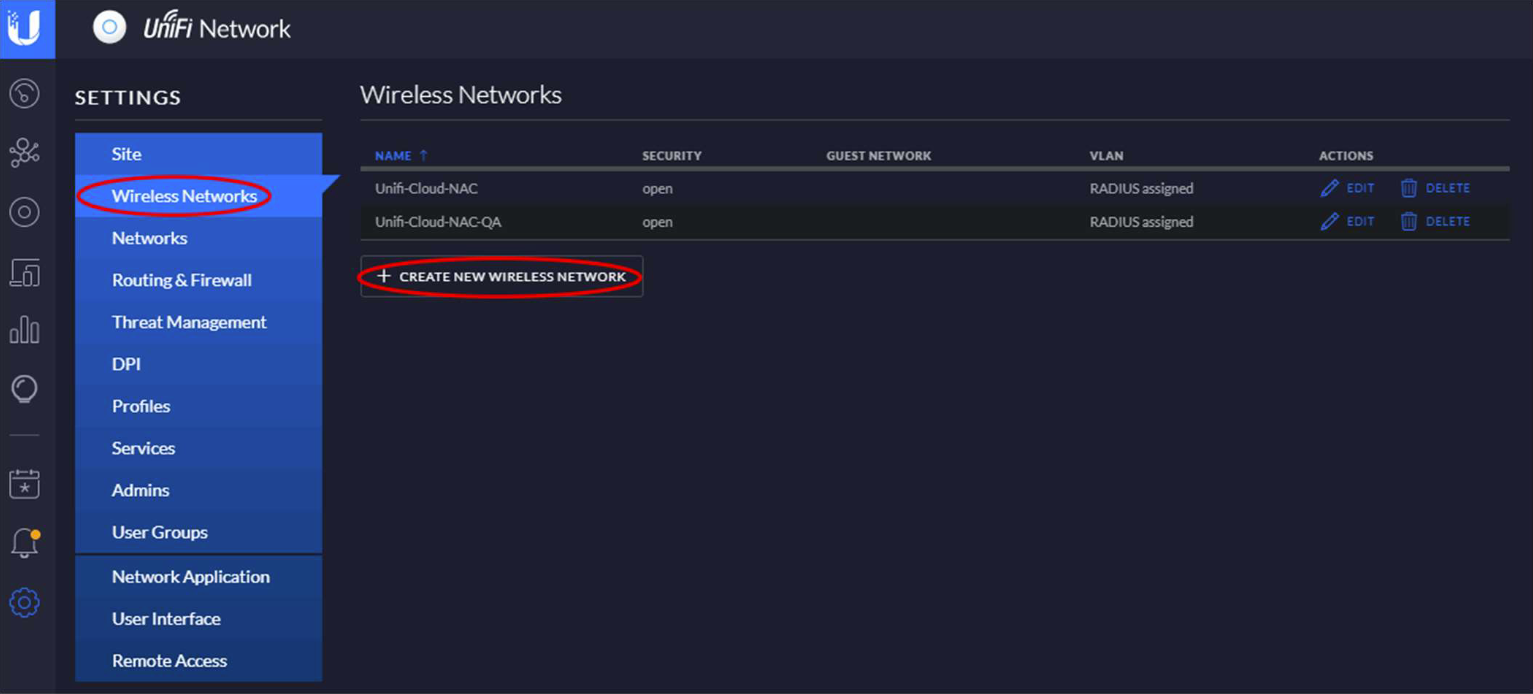
Click Advanced OPTIONS
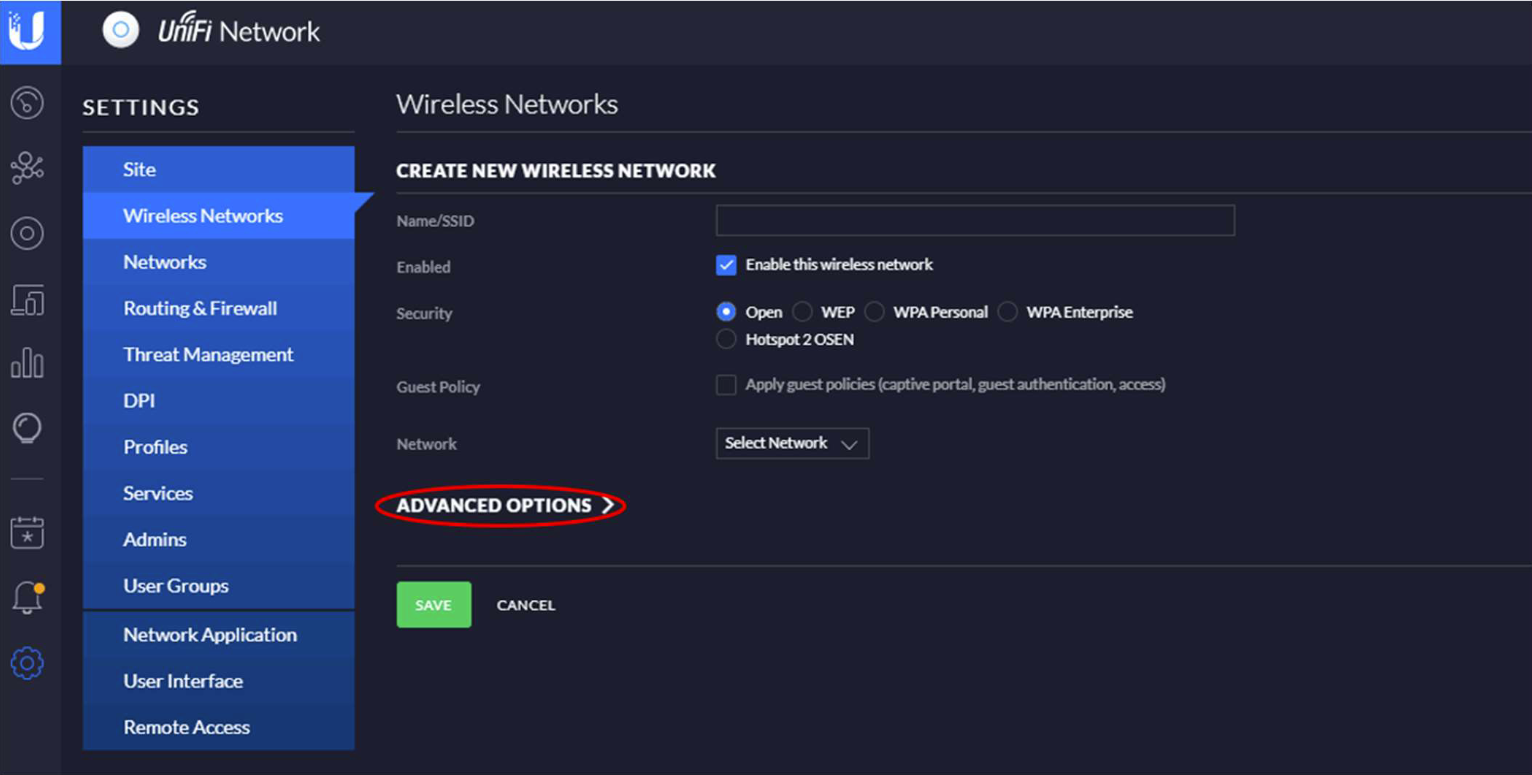
Open (Guest) SSID Configuration
Give the network (SSID) a name, ensure its enabled and expand Advanced Settings
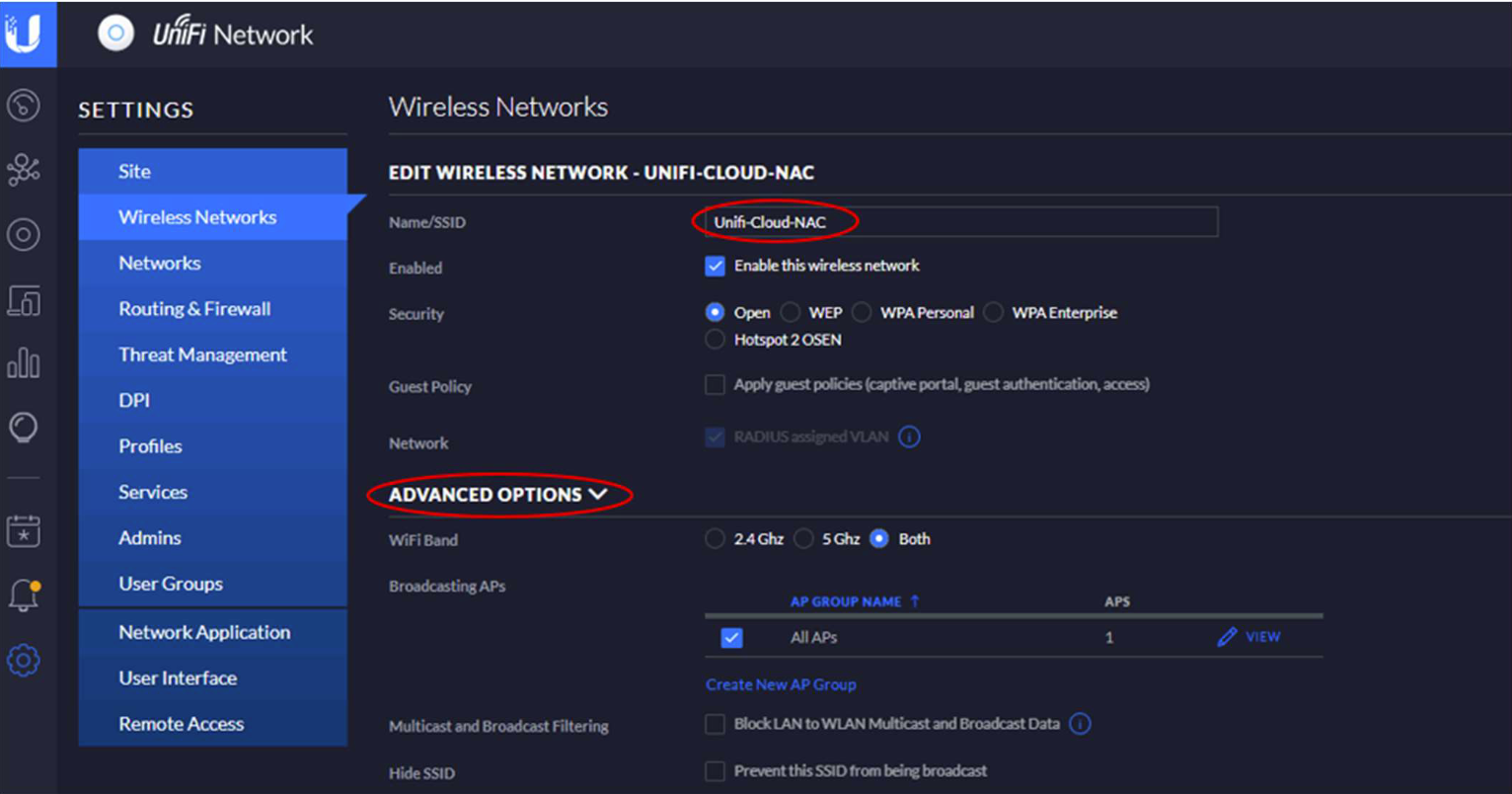
Select Enable RADIUS DAS/DAC (CoA)
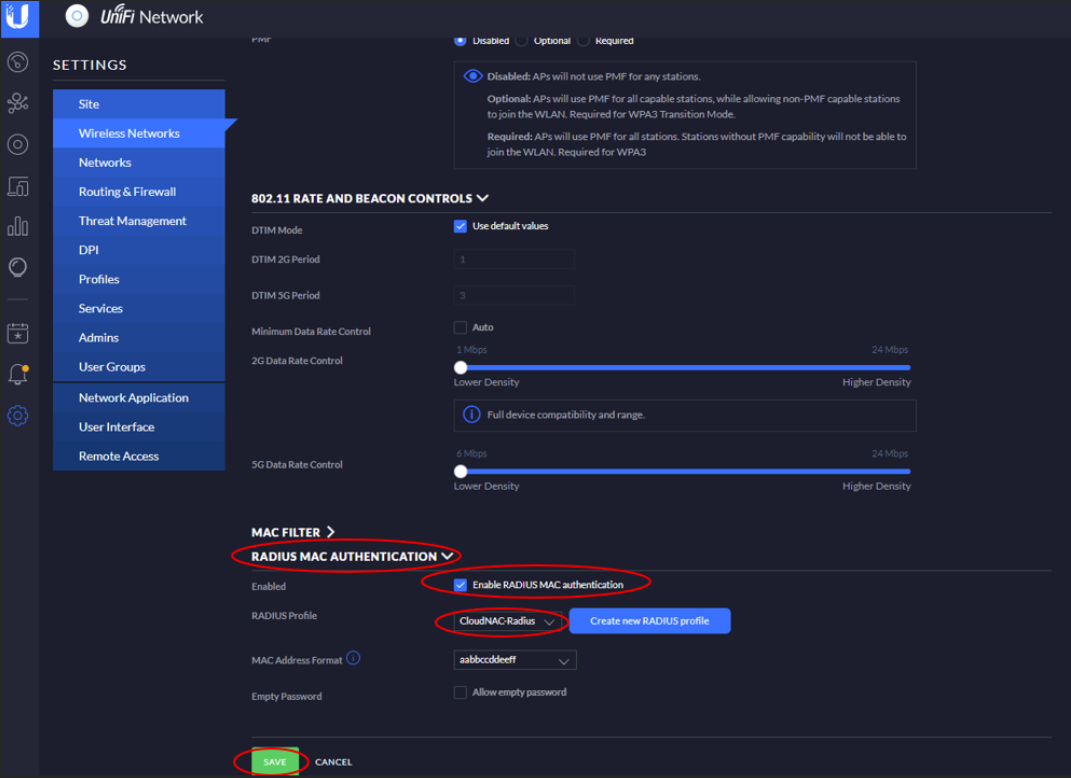
Under RADIUS MAC AUTHENTICATION select Enable RADIUS MAC Authentication, set the RADIUS profile to the one configured above for radsec proxy, and ensure the MAC address format is set to lowercase with no delimiter as shown.
RADIUS NAC Configuration
Unifi leverages RADIUS assigned VLANs. The roles configured in the RADIUS NAC UI for the Unifi NAS type should be configured as shown below.
2. Cisco Wired Integration
Cisco 2960X Switch Configuration
In this example, a Cisco 2960X configuration is provided. However, any Cisco Layer 2 switch supporting the following features are eligible for integration:
- RADIUS Authentication/Accounting
- MAC Authentication Bypass (MAB)
- RADIUS Change of Authorization (CoA)
Note – In this example RadsecProxy is 10.10.10.10 (replace this IP with the IP of your RadsecProxy system)
Note – Replace the VLAN number on the example port configuration with the desired default VLAN for the port.
Note – The “radius-server vsa send authentication” command is enabled by default and auto-generated on some IOS versions. If the command does not show up in a sh run, “sh run all” can be used to verify that it is configured on the switch.
aaa new-model aaa authentication dot1x default group radius aaa authorization network default local group radius aaa accounting dot1x default start-stop group radius aaa session-id common aaa accounting update newinfo periodic 10 ! aaa server radius dynamic-author client 10.10.10.10 server-key XXXXX port 3799 auth-type any ! dot1x system-auth-control ip device tracking ! interface GigabitEthernetX/X/X (replace with interface number) description MetaAccess RADIUS NAC User Test Port switchport access vlan X (replace with desired default VLAN for port) switchport mode access mab authentication host-mode multi-auth ! ip radius source-interface X (Layer 3 management interface) ! radius-server host 10.10.10.10 auth-port 1812 acct-port 1813 key XXXXX radius-server vsa send authenticationRADIUS NAC Configuration
Cisco leverages RADIUS assigned VLANs. The roles configured in the RADIUS NAC UI for the Cisco NAS type should be configured as shown below.

