Below you can find a step by step tutorial on how to integrate Microsoft Azure Active Directory with MetaDefender Sandbox using the OpenID Connect protocol.
Prerequisites: An Entra Tenant (quick guide: https://learn.microsoft.com/en-us/entra/identity-platform/quickstart-create-new-tenant )
Prepare the MetaDefender Sandbox for the OAuth integration
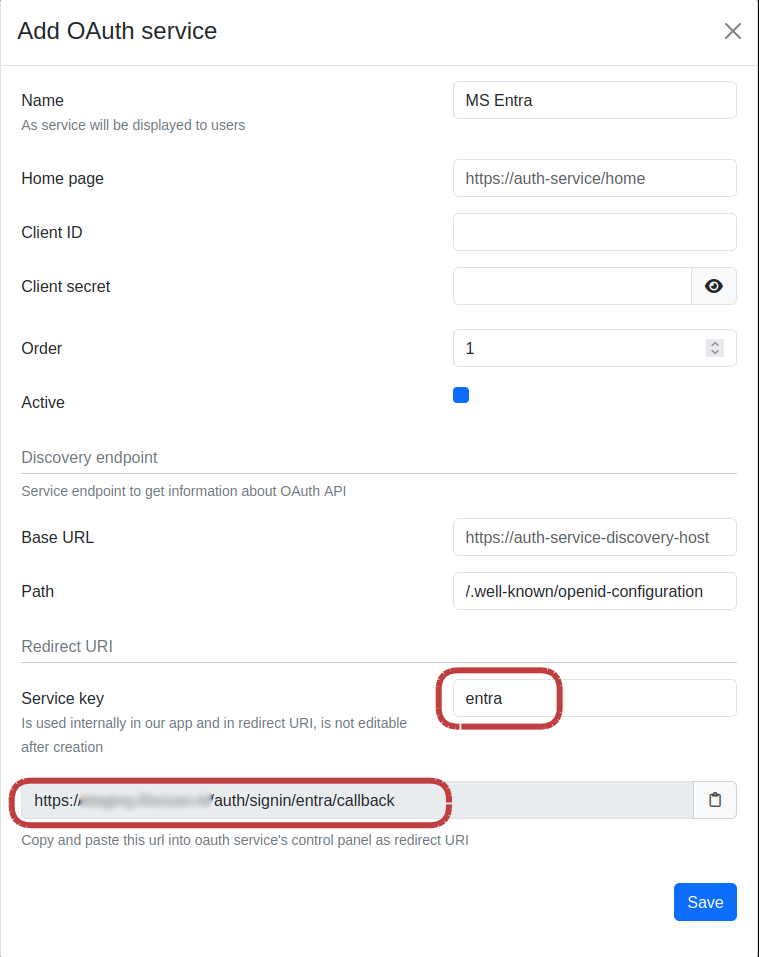
Let’s prepare MetaDefender Sandbox SSO settings as follows:
- Go to Admin panel > Settings > Authentication on MetaDefender Sandbox page.
- Click on + Add Service button
- Fill in the Name (e.g. "MS Entra") and Service key (should be "entra") values
- Do not click Save yet, the remaining values will be filled in later
- Please note down the Redirect URI at the bottom of the form
Register application in Microsoft Entra ID
- Sign into Microsoft Entra ID and navigate to admin dashboard
- Go to App registrations and select New registration

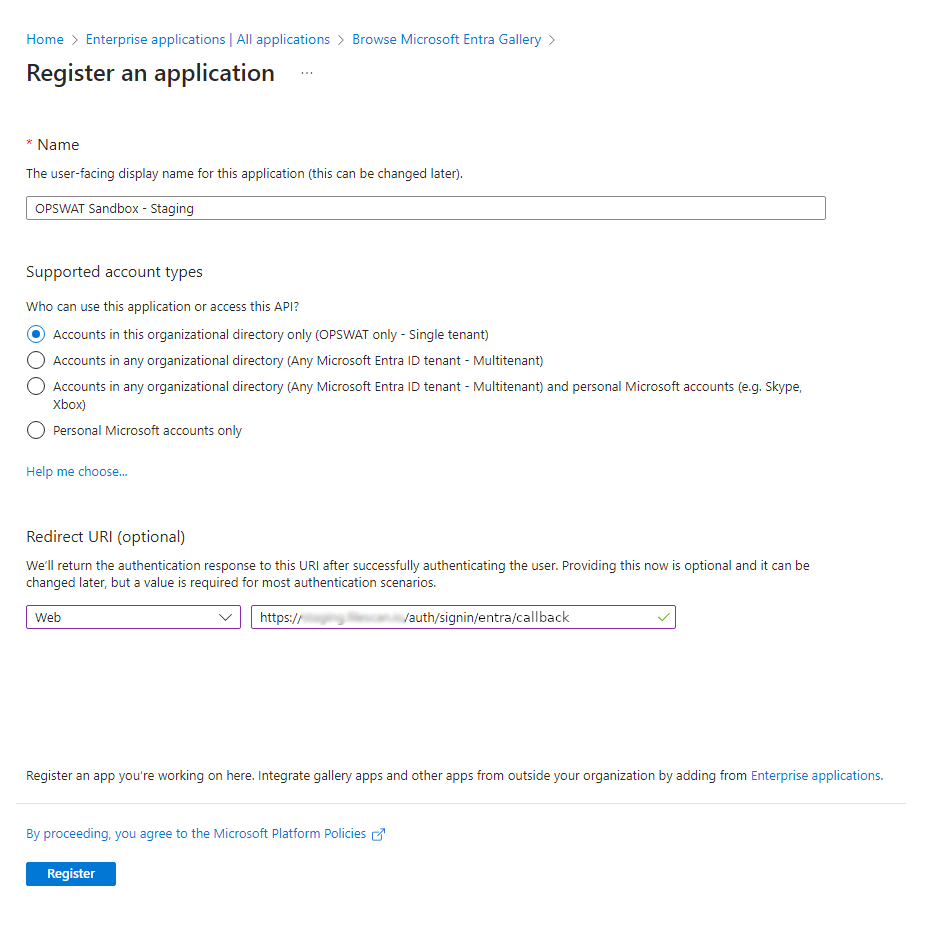
- Let’s configure the application settings.
- Give the application a name. for example “MetaDefender Sandbox”. In the following examples we will use "OPSWAT Sandbox - Staging" as the application name
- Configure the Redirect URI (
https://<host>:<port>/auth/signin/<service_key>/callback) - Use the value you noted down in the previous section.
Microsoft Entra ID supports only HTTPS protocol for redirect URI
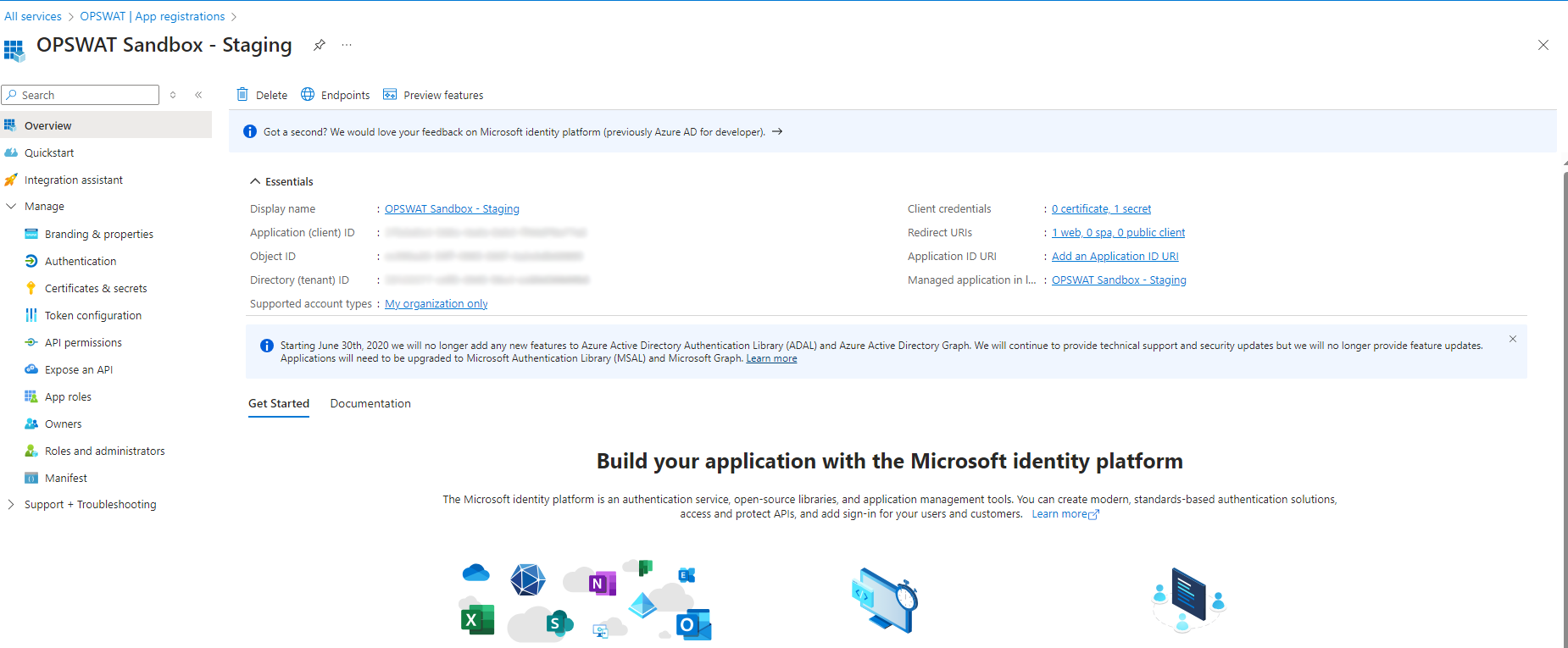
- Note down Application (client) ID and Directory (tenant) ID of the newly created application as it will be needed in a later step
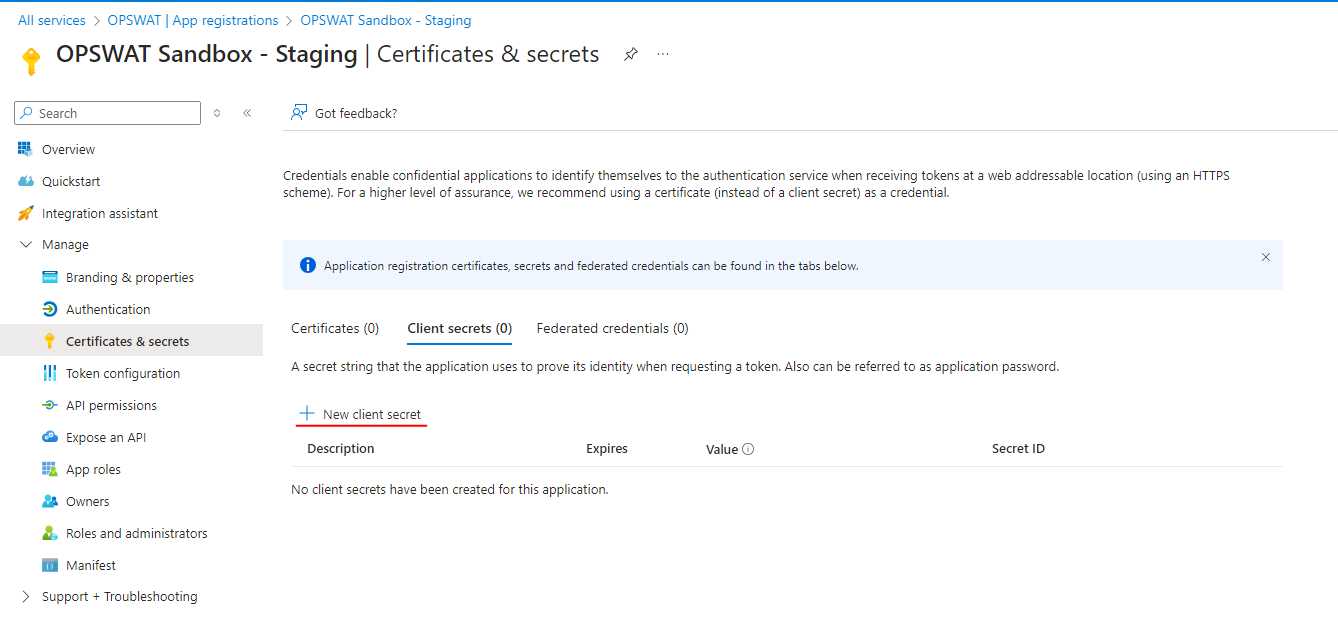
Generate Secret key for Entra ID SSO
Go to Certificates & Secrets and generate a new client secret string (also referred to as an application password). Record the client secret.
You will not be able to retrieve client secret at a later time because it will be hidden. You need to generate a new secret in this case.
Configure MetaDefender Sandbox for Entra ID SSO
Let’s configure MetaDefender Sandbox SSO settings using the information collected above
- Go to Admin panel > Settings > Authentication on MetaDefender Sandbox page.
- Click on + Add Service button
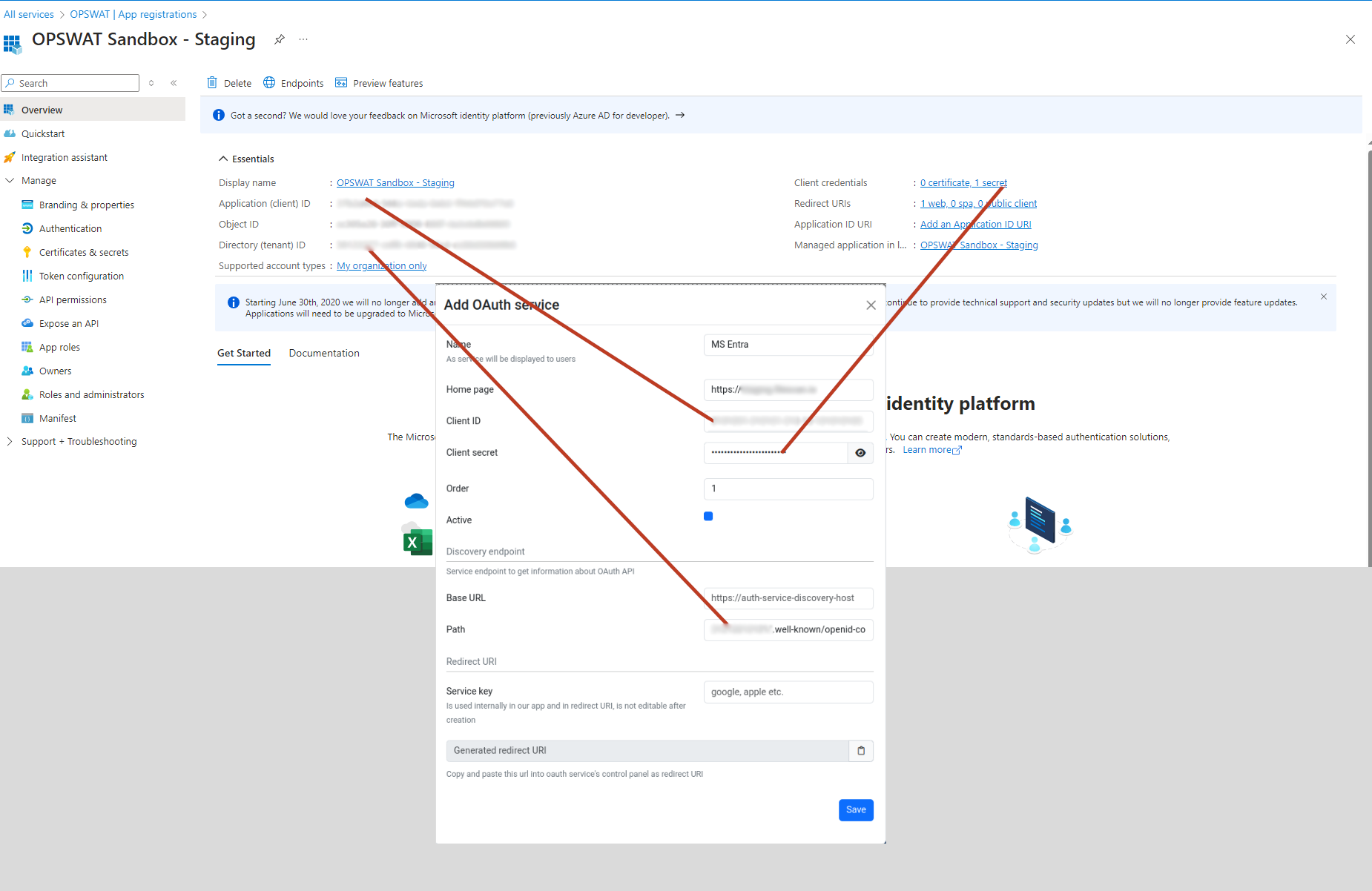
- Fill the form with the follows and save the form:
| Field | Description | Example |
|---|---|---|
| Name | Integration name | MS Entra |
| Home page | First page after log in | https://sandbox.mycompany.com |
| Client ID | Application (client) ID , comes from Entra | 1234-5678-90123-4567 |
| Client secret | Comes from Entra | abcd1234!%# |
| Order | The order of authentication can be specified | 1 |
| Active | Enable or disable the authentication | on |
| Base URL | Service base url | https://login.microsoftonline.com |
| Path | Service URL postfix. Format should be: /<tenant_id>/v2.0/.well-known/openid-configuration Tenant id comes from Entra: Directory (tenant) id | /12314/v2.0/.well-known/openid-configuration |
| Service Key | Is used internally in our app and in redirect URI | entra |
Login as an Entra organization admin
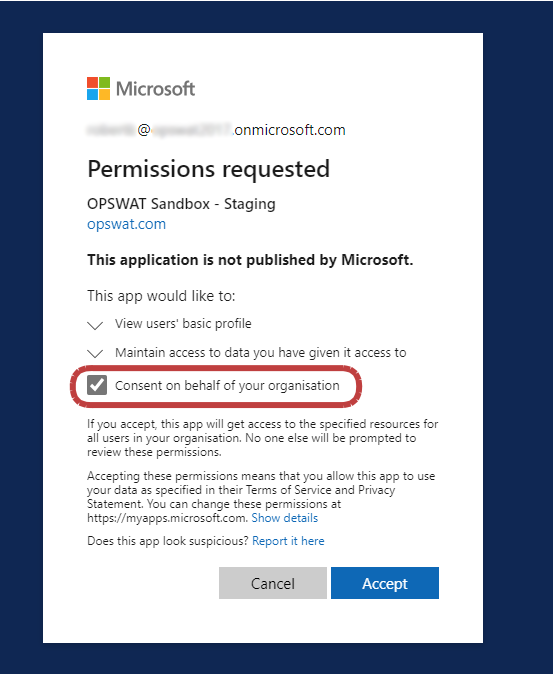
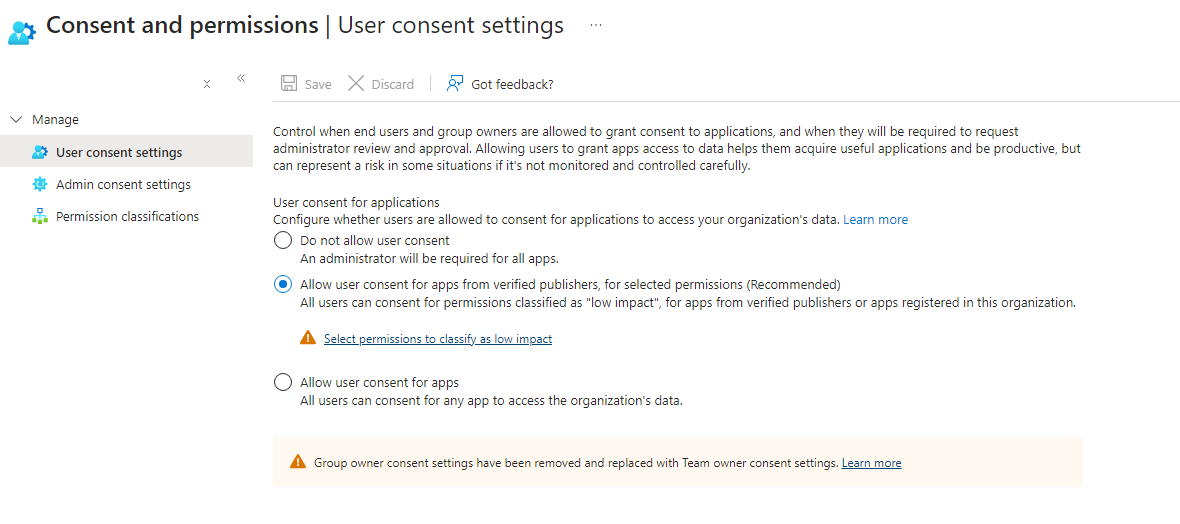
Depending on Entra ID configuration, and organization admin should approve/allow a new application beforehand.
Log in to MetaDefender Sandbox SSO with the Entra ID administrative account and accept the newly created application:
Testing the integration
- Log out of MetaDefender Sandbox
- You will notice that there is a new Sign In with SSO button on the login page
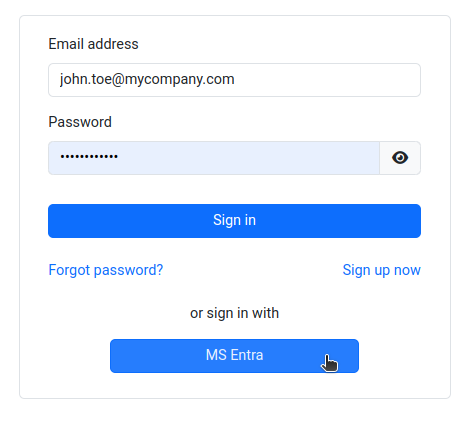
- Click Sign In with SSO. You should be redirected to Microsoft Entra ID to login. Once logged in, you will be redirected back to MetaDefender Sandbox and automatically logged in.
In some cases, the following warning might be displayed even though the login is successful. This is a known issue and will be fixed in the next version of the product.


