In this section, we will highlight our cybersecurity software's key capabilities, including sample analysis, malware family decoding, disassembly unpacking, similarity search, and more. These features represent our commitment to providing comprehensive tools for detecting and combating malware effectively. Explore the reports below to delve into each capability in detail.
#1 Geofencing
Malware documents employing geofencing have become a significant threat to cybersecurity. These malicious files often employ location-based triggers, making detection and mitigation a challenging task. However, Adaptive Threat Analysis stands out from traditional approaches by offering the capability to accurately emulate and falsify the expected geolocation values, effectively neutralizing the tactics employed by malware, thus enhancing our ability to protect against such threats.
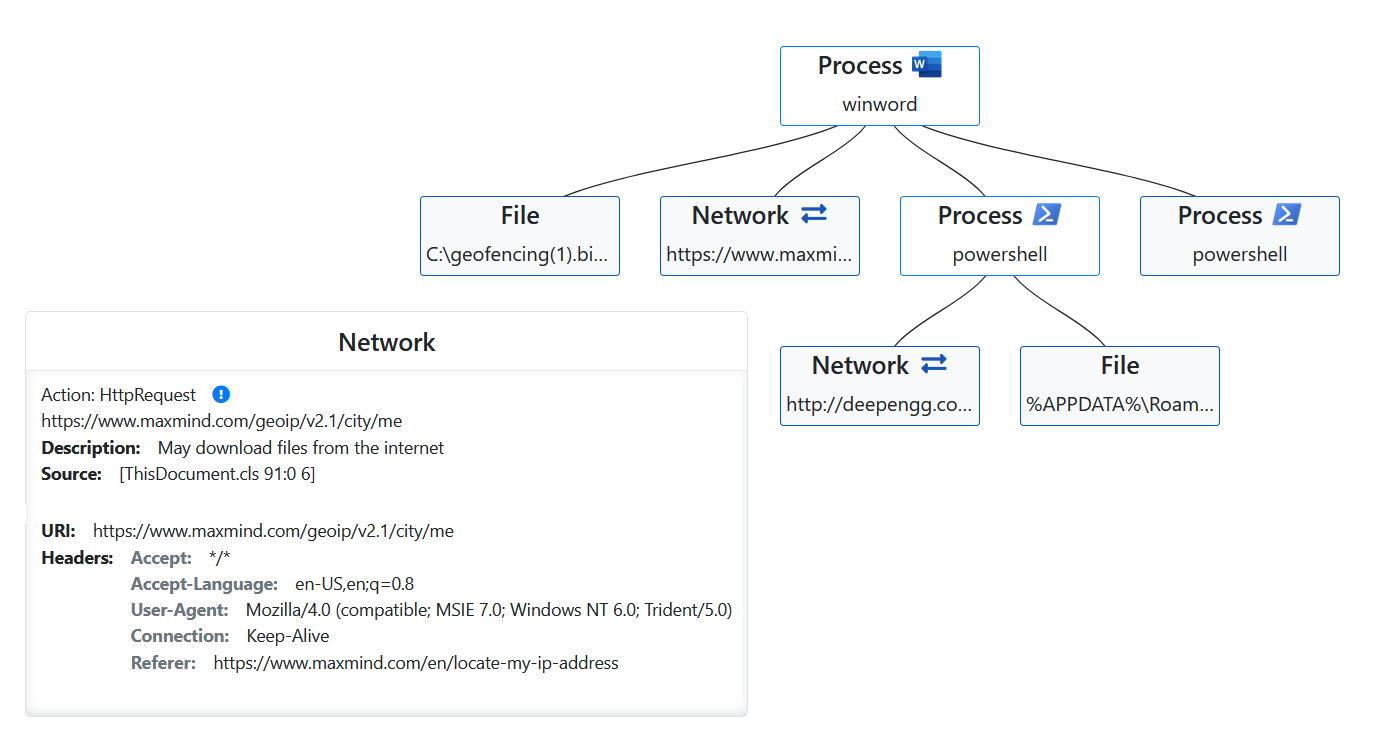
In the sample provided below, we can observe a geofencing malware attempting to execute exclusively within a specific country. However, our innovative solution successfully bypasses this restriction, as previously mentioned, by emulating the desired geolocation values, demonstrating our superior capability in countering such geofencing-based threats.
#2 Phishing detection
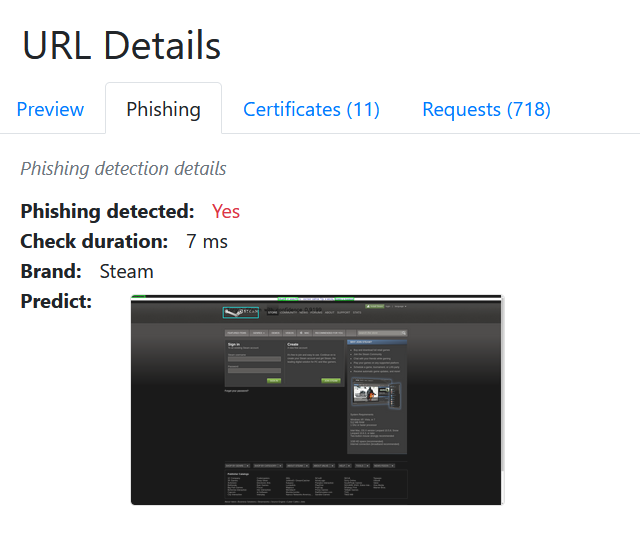
By rendering suspicious websites and subjecting them to our advanced machine learning engine we're capable of identifying near 300 brands. In the example provided below, you can witness a Russian website masquerading as a computer gaming company known as Steam. Our solution excels in comparing the site's content to the genuine URL, swiftly identifying such fraudulent attempts to safeguard your digital assets and personal information.
Learn more about this feature by clicking here.
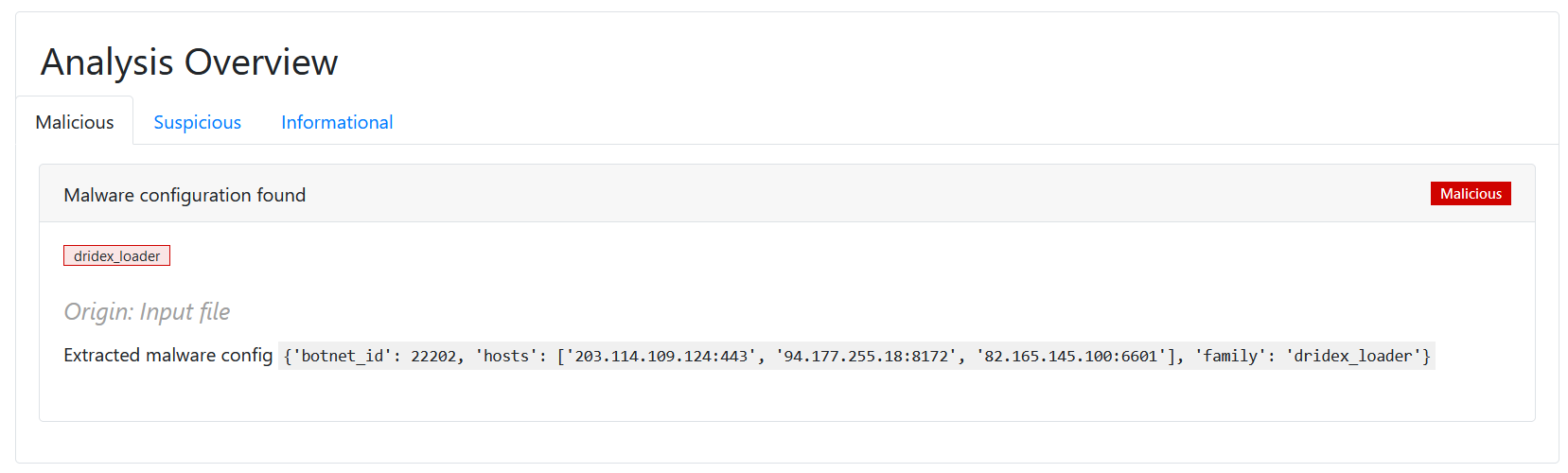
#3 Malware config extraction of a packed sample
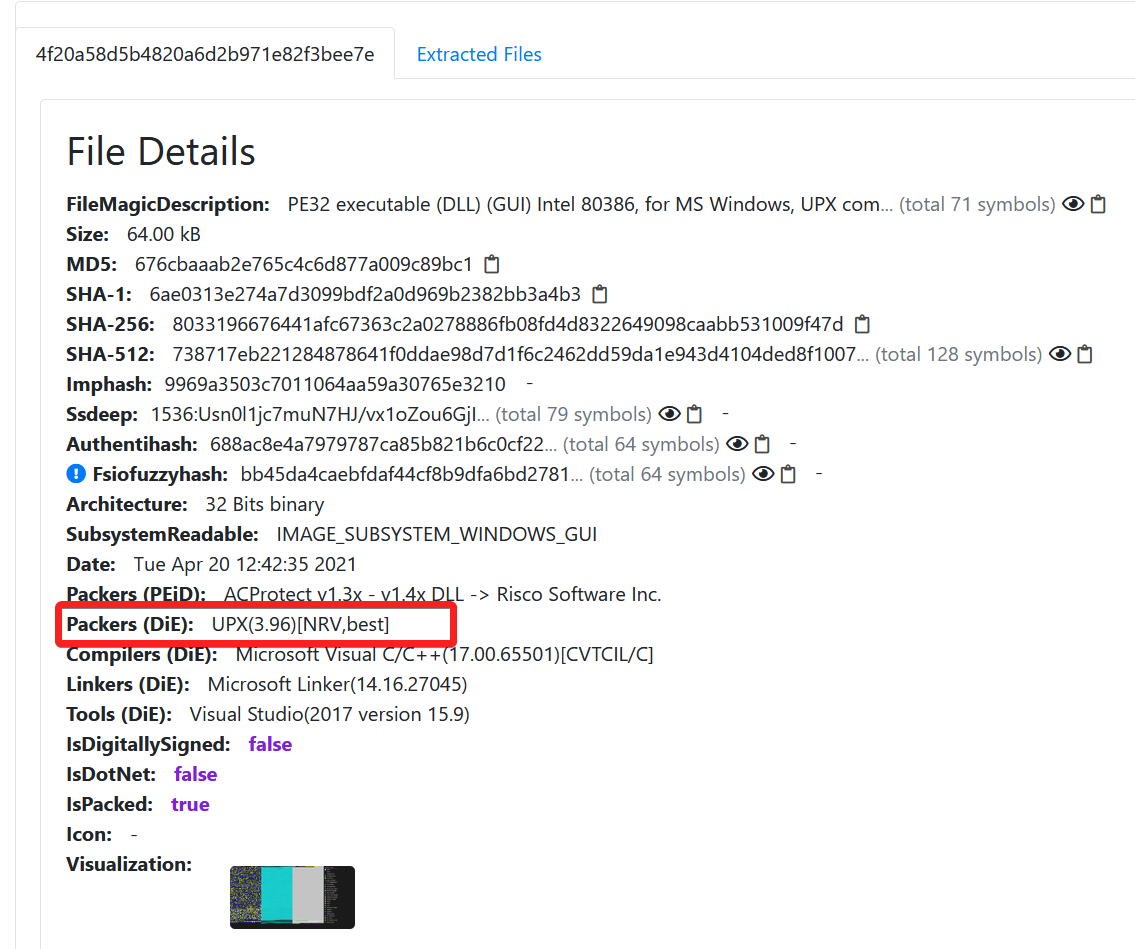
The sample below reveals a malware that was crypted using the UPX packing technique. Despite its attempt to obfuscate, our analysis successfully unpacked the payload, exposing its true identity as a Dridex Trojan. We were able to uncover the correct configuration, shedding light on the malicious intent behind this threat.
Learn more about malware config extraction feature by clicking here.
Learn more about malware unpacking feature by clicking here.
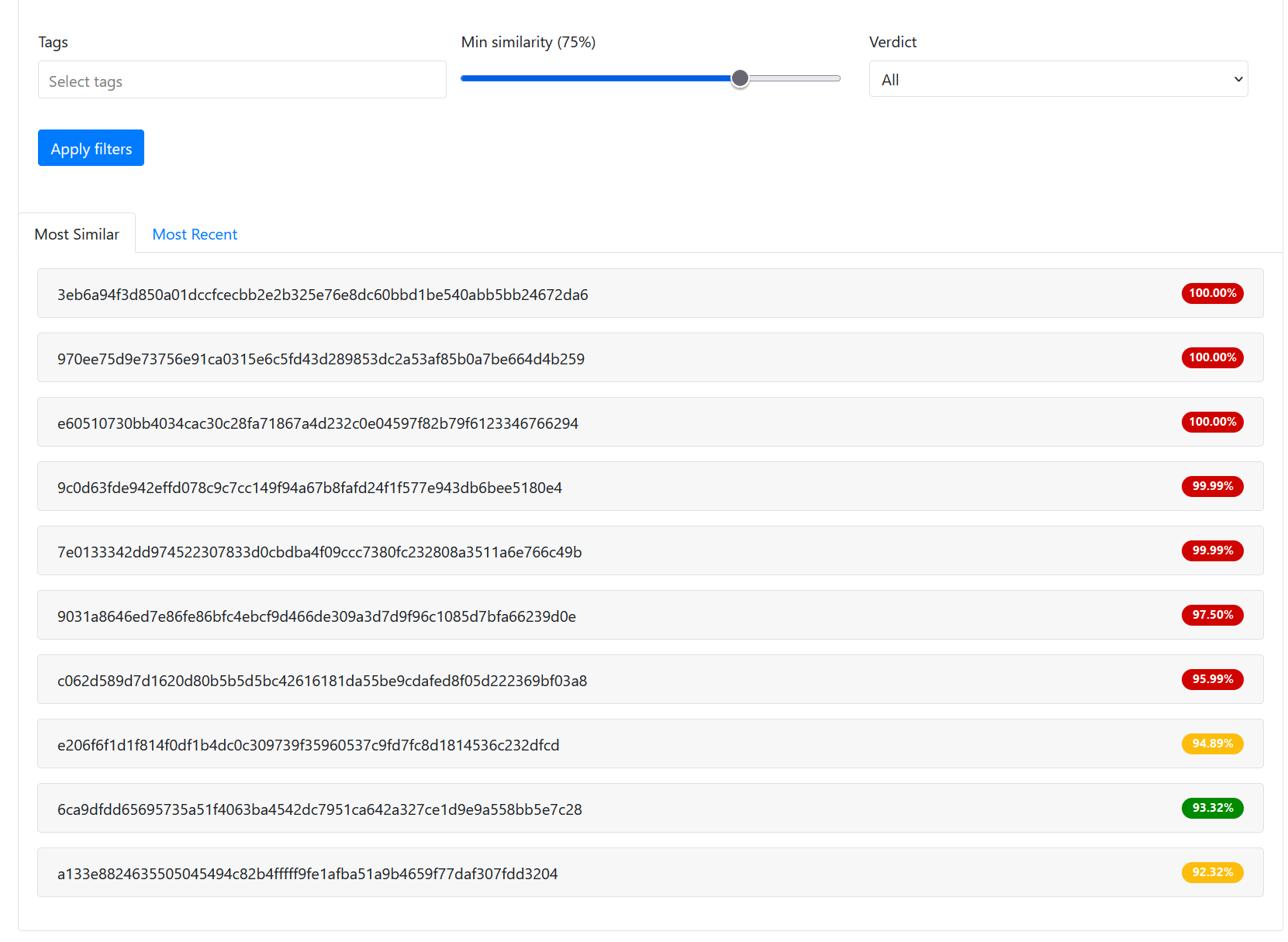
#4 Similarity Search
Employing Similarity Search functionality, has detected a file remarkably resembling a known malware. Notably, this file had been previously marked as non-malicious, revealing the potential for false negatives in our security assessments. This discovery empowers us to specifically target and rectify these overlooked threats.
Learn more about this feature by clicking here.
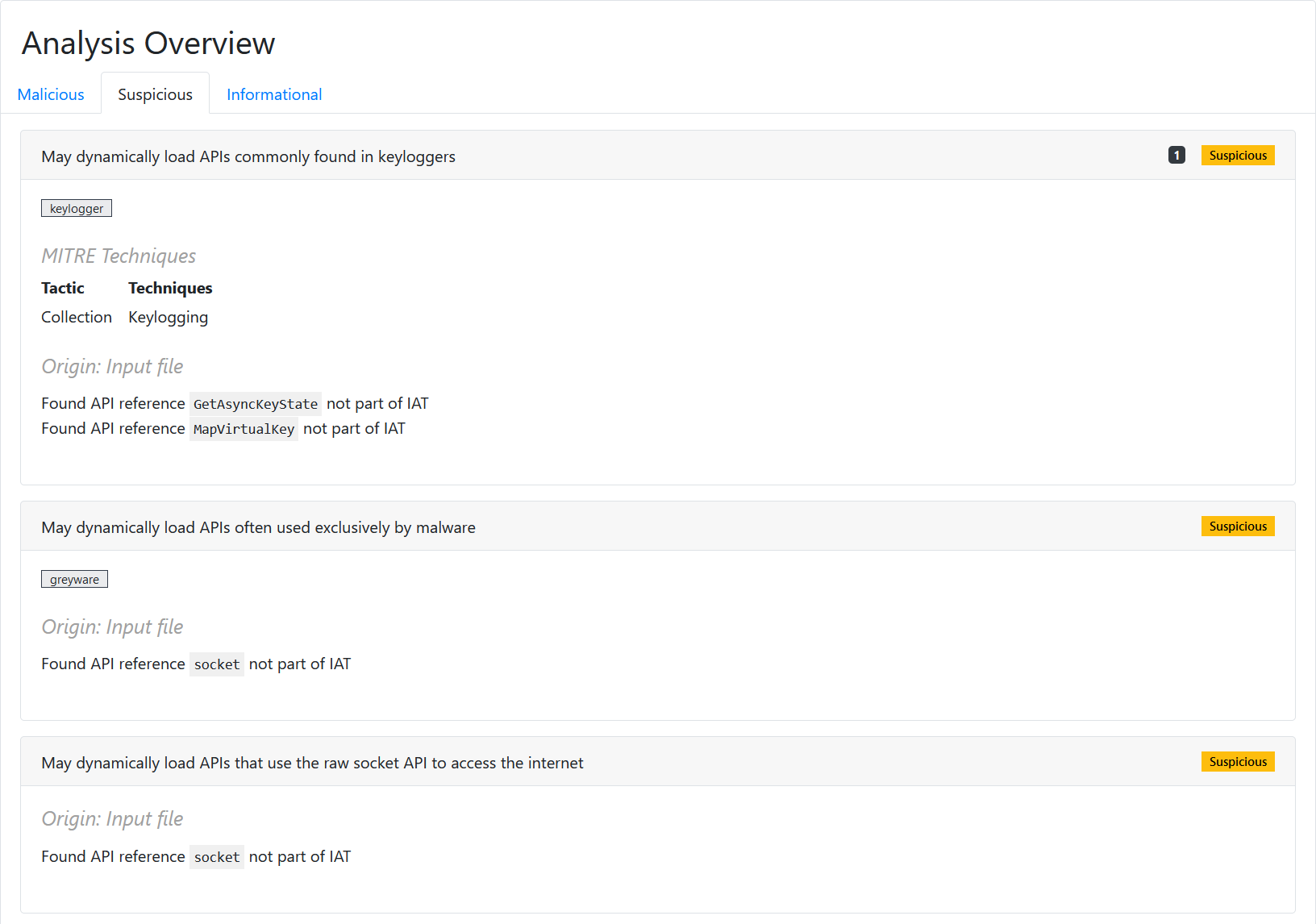
#5 Finding interesting things via Disassembly
#5.1 Native executable
Our disassembling engine revealed intriguing findings within the target
sample. Surprisingly, this sample monitors the system time using the
uncommon rdtsc instruction and accesses an internal, undocumented
structure in Windows. These unusual actions raise questions about its
purpose and underscore the need for further investigation to assess
potential risks to the system.
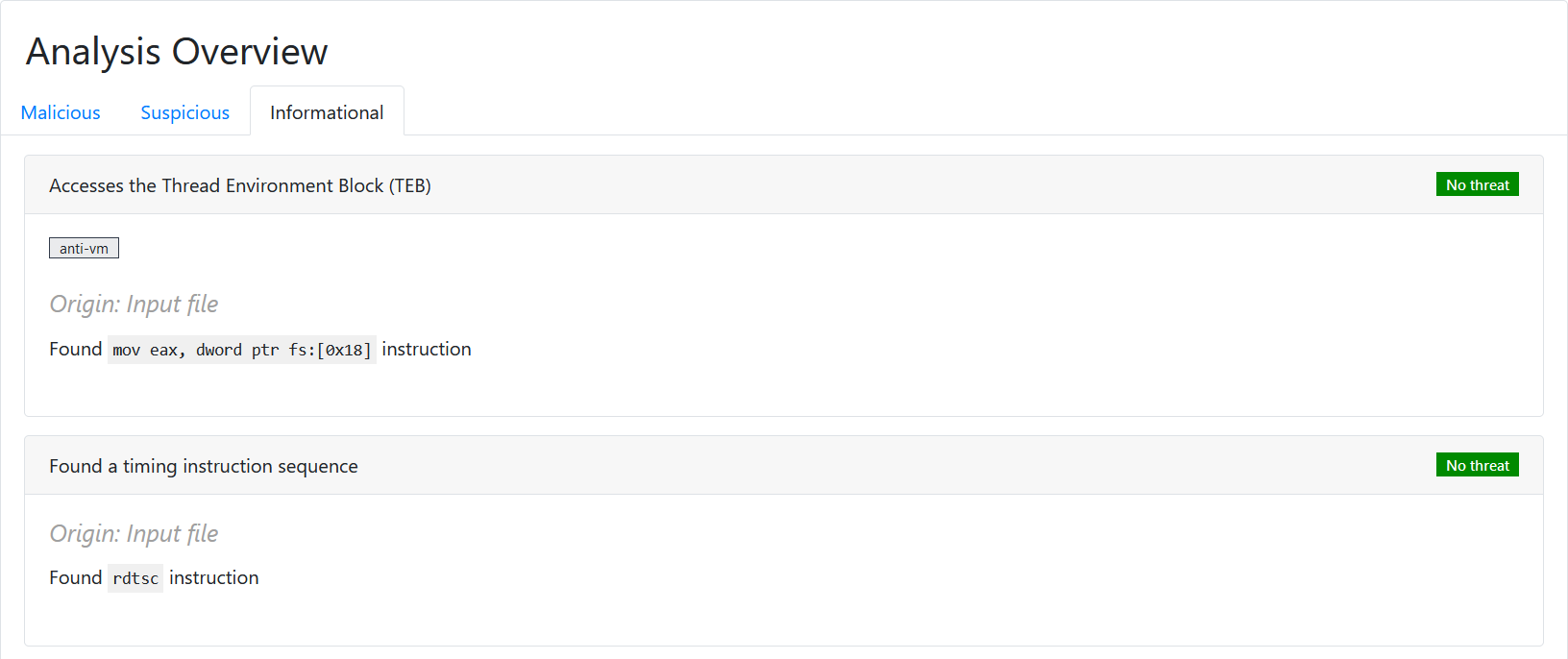
#5.2 .NET Executable
The sample under examination was built using .NET framework. While we refrain from displaying the actual CIL, but our decompilation process extracts and presents noteworthy information, including strings, registry artifacts, and API calls. This comprehensive approach allows us to uncover potential indicators of compromise, facilitating a deeper understanding of the sample.
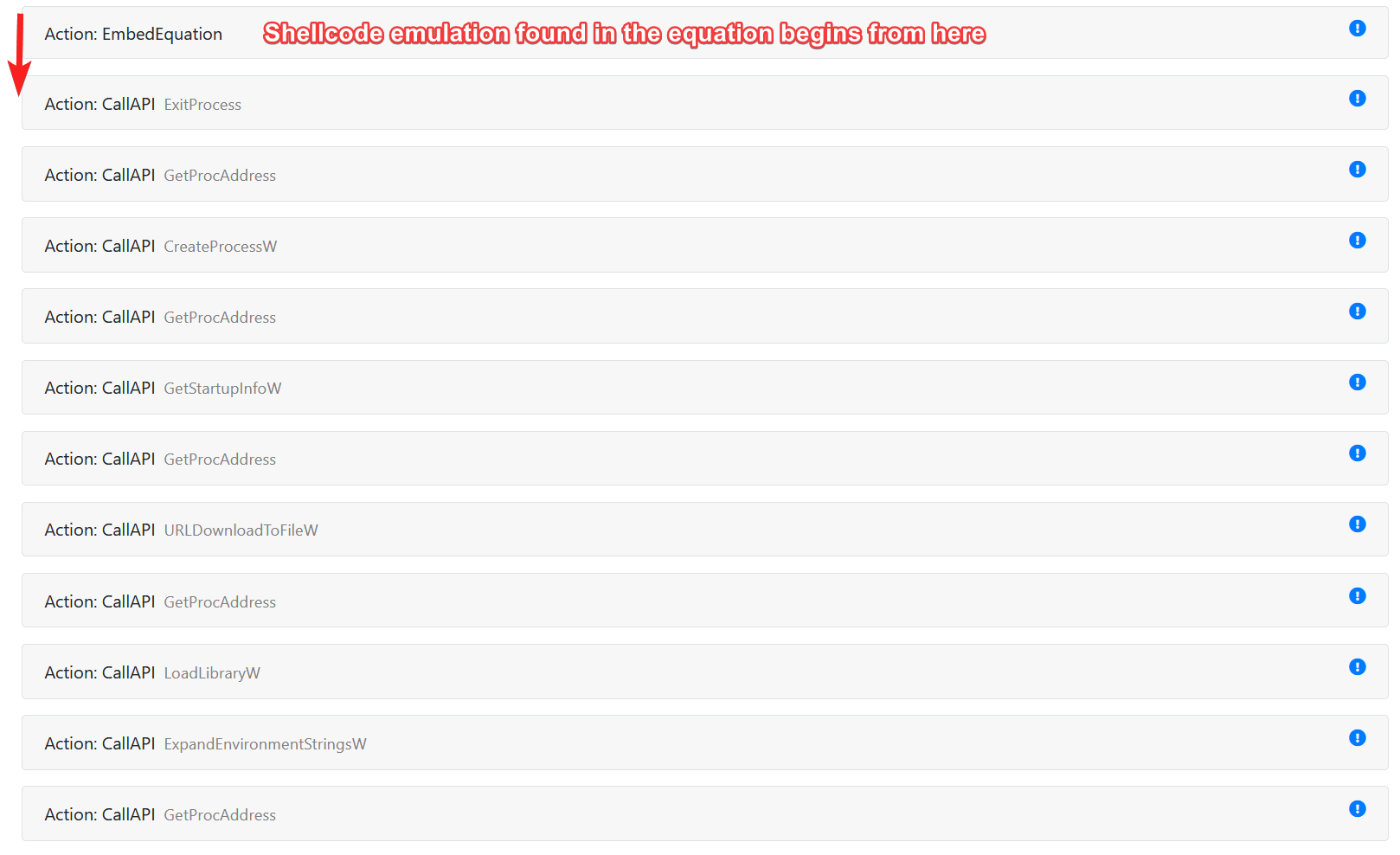
#6 Shellcode emulation