Secure Your Applications
Dark Reading’s latest report reveals why an end-to-end defense strategy is essential to protecting your organization against the relentless wave of cyber threats. See why OPSWAT and F5 combined solutions enable organizations to enhance their overall cybersecurity posture.
While CISA Recommends a Defense-In-Depth Approach:
- Only 17% of organizations have fully implemented these strategies
- This leaves 83% of organizations vulnerable, lacking the comprehensive, multi-layered security needed to defend against today’s sophisticated threats
Uncover Expert Strategies for Strengthening Your Cyber Defenses
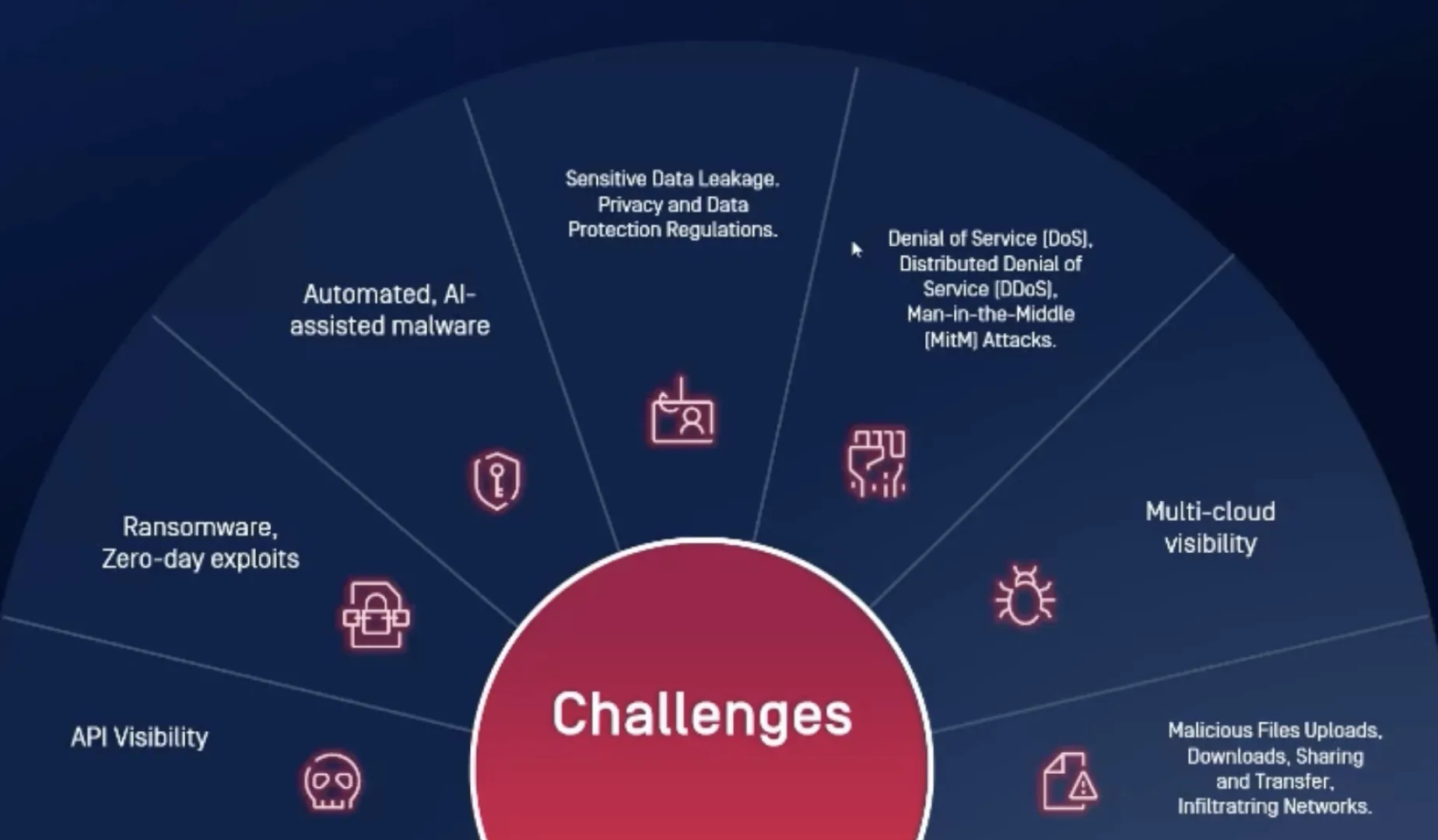
Over 45% of surveyed organizations identified escalating malware attacks as their top challenge. Featuring exclusive data and expert perspectives to inform your security strategy, this report analyzes the current state of cybersecurity, identifying gaps, and highlighting the most common types of attacks such as data theft, ransomware, and denial of service. See how cybersecurity practices are evolving in response to emerging threats.
Gain an insider’s perspective on the complex world of application security and learn from those on the front lines.
Get Data-Backed Intel on Key Topics Including
Lack of Preparedness for Escalating Malware Attacks
Noncompliance with Regulatory Requirements
Perceived Lack of Support from Leadership
Complexity of Web Application Security
Evolving Threat Landscape
Get the Report Now
Download this report now and speak to an expert to arm yourself with the knowledge and strategies needed to build a robust, multi-layered defense system.
Additional Resources
Stay Ahead of the Curve
Don’t leave your applications vulnerable to attack
Explore end-to-end comprehensive cybersecurity solutions by OPSWAT and F5 in the latest panel discussion on the key findings from the report to enhance your security posture